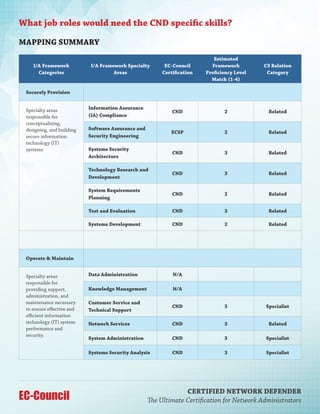
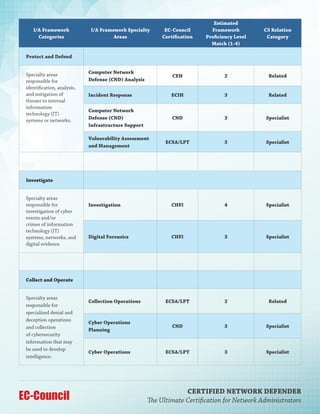
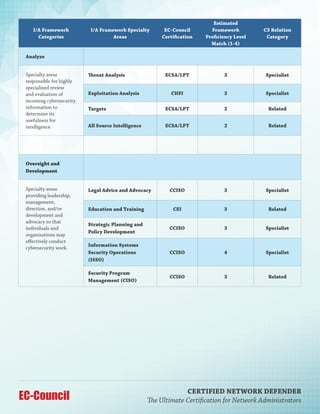
The Certified Network Defender (CND) program by EC-Council is a comprehensive, hands-on training course aimed at equipping network administrators with essential skills in network security, focusing on the protect, detect, and respond framework. It includes practical labs and covers various topics such as security policies, risk management, and incident response, preparing participants for real-world network defense scenarios. With a duration of five days, this vendor-neutral certification is designed to address the critical skills gap in cybersecurity among IT professionals.