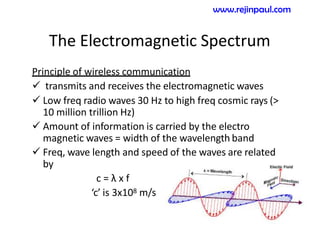
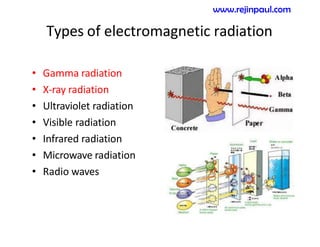
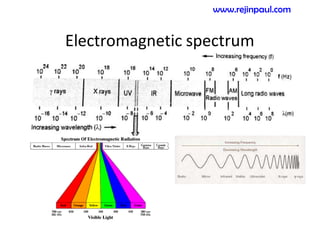
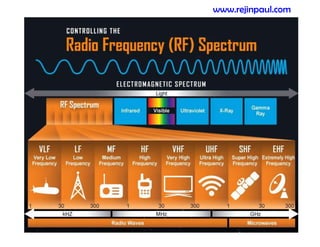
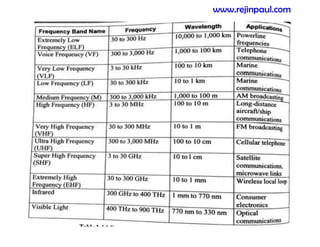
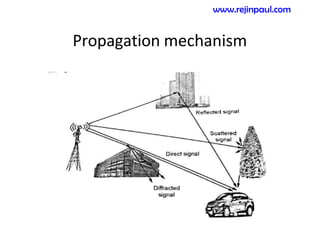
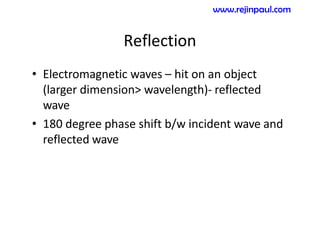
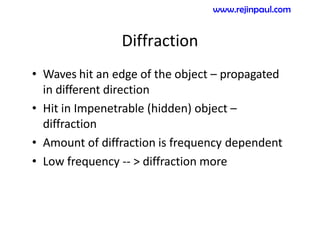
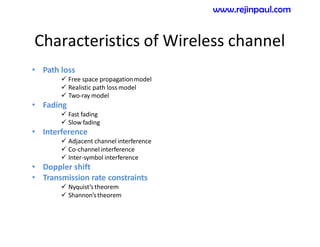
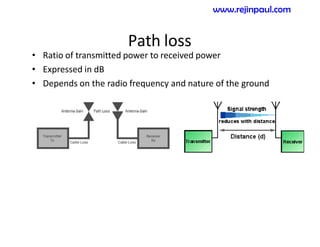
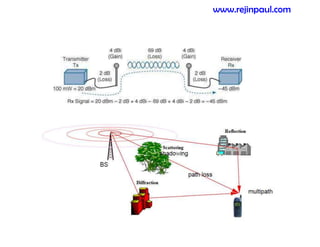
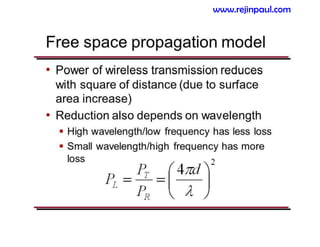
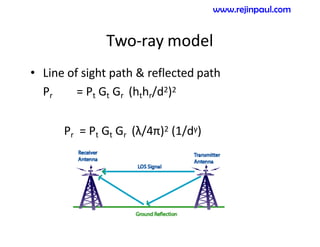
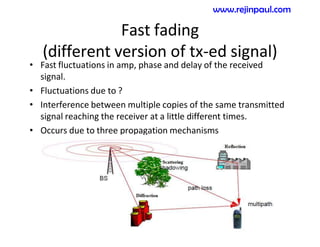
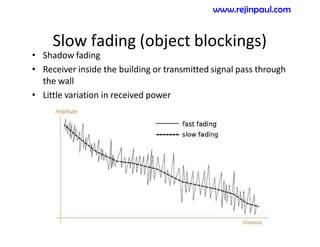
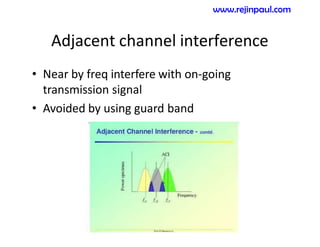
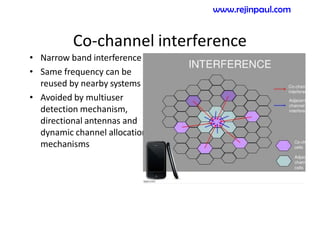
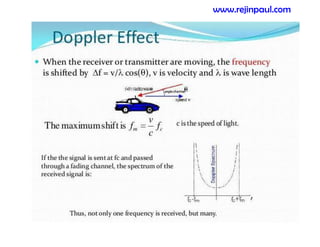
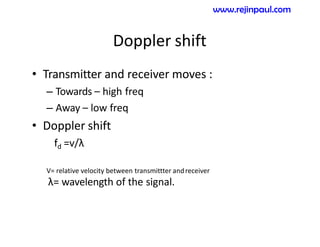
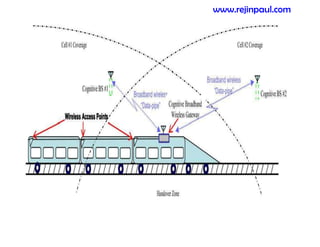
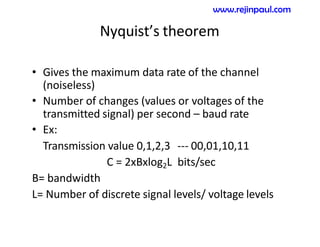
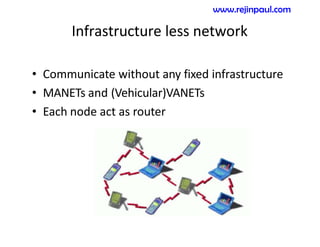
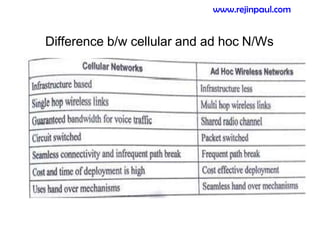
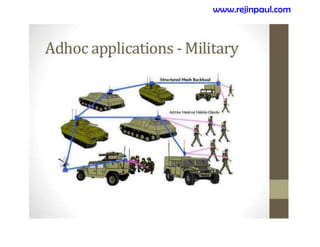
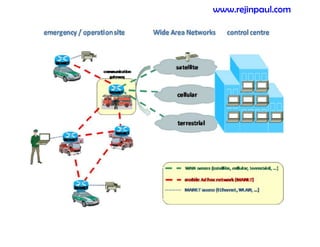
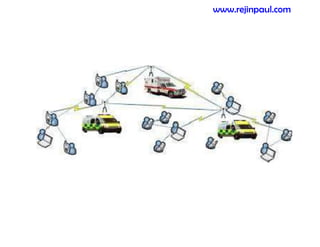
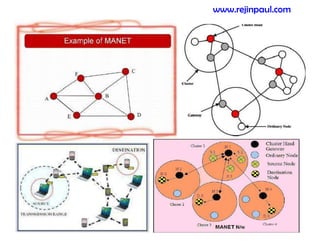
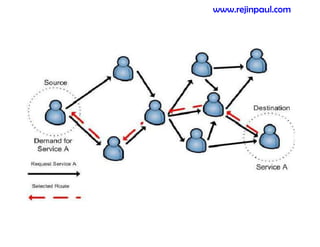
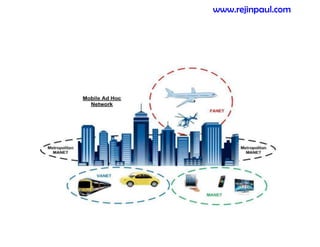
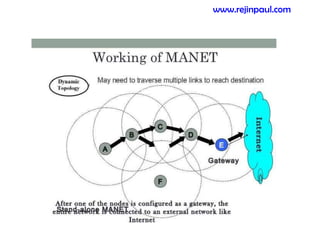
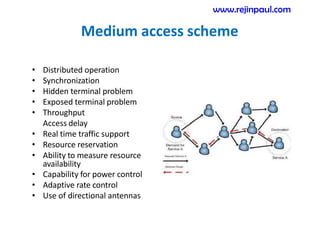
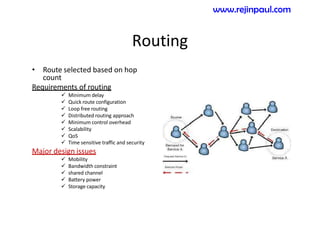
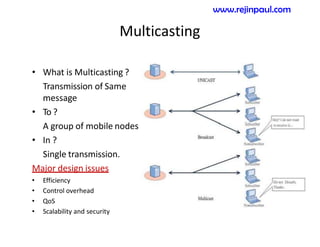
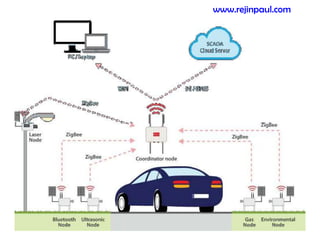
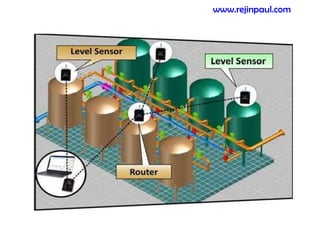
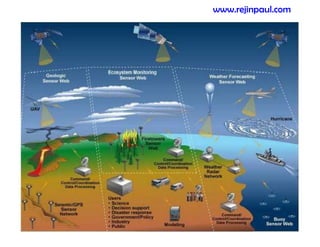
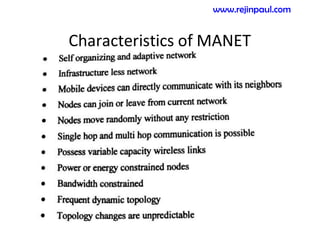
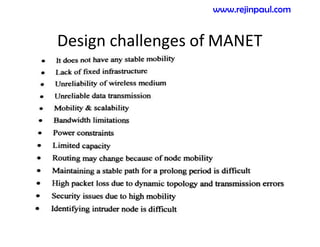
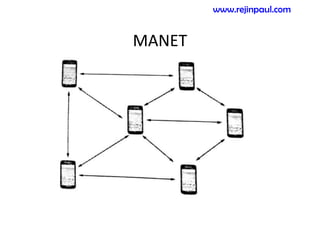
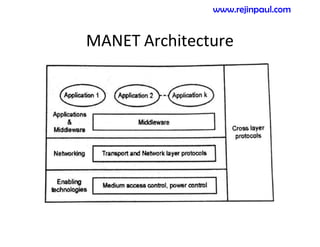
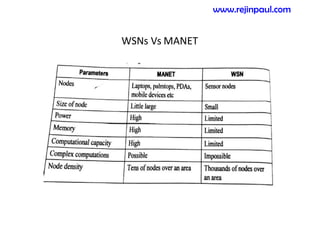
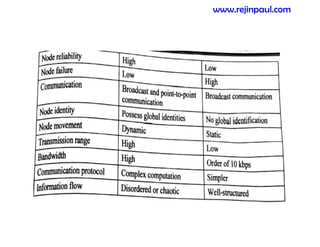
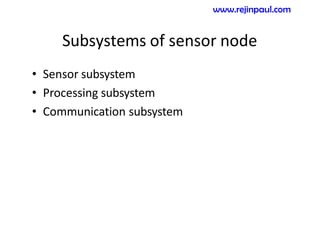
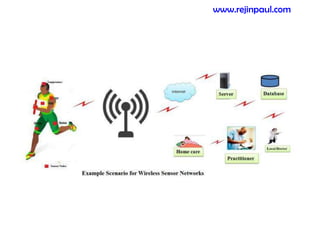
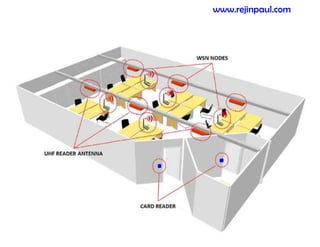
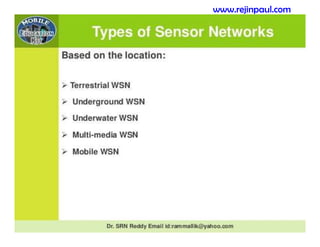
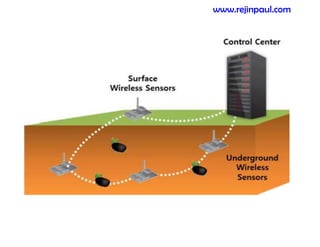
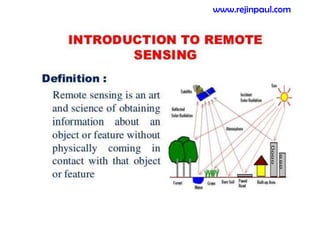
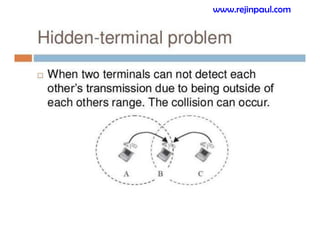
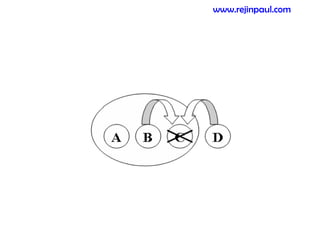
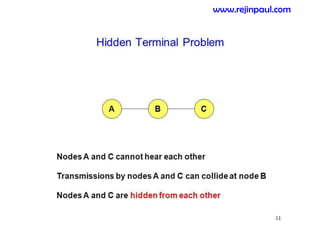
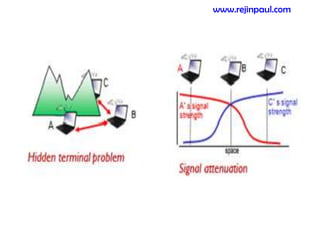
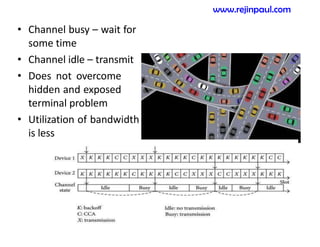
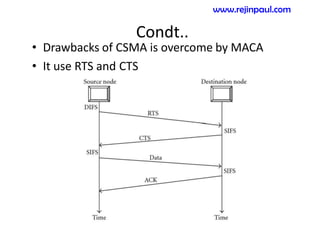
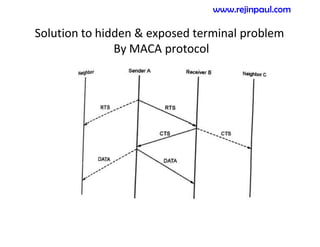
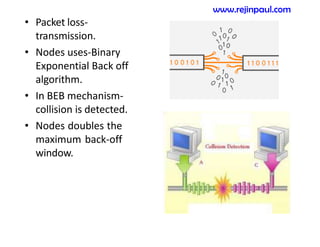
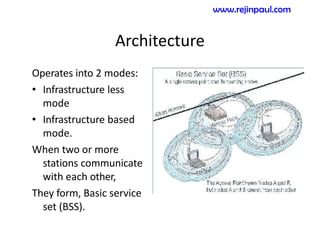
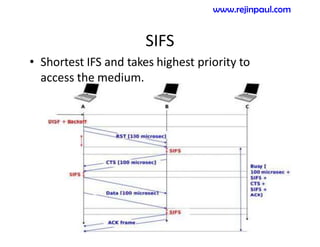
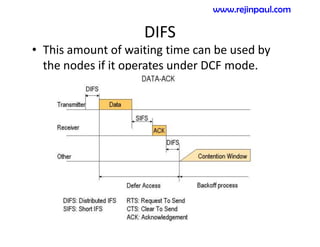
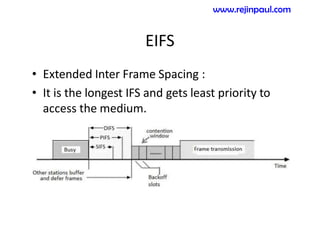
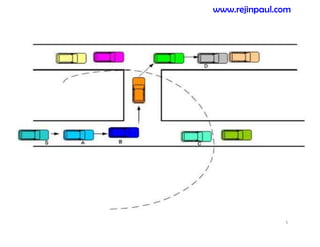
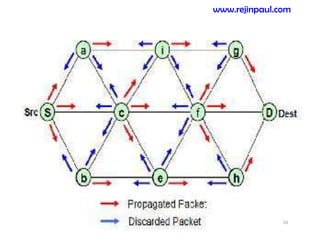
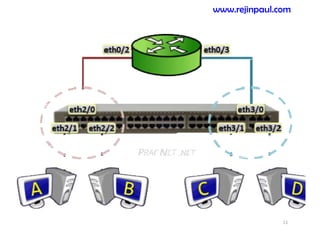
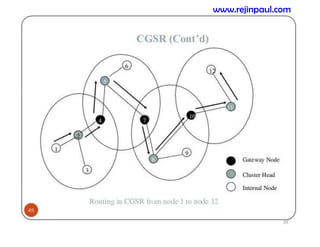
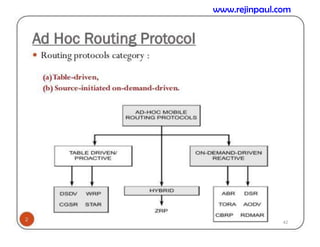
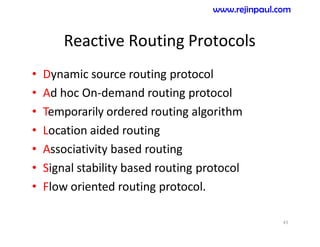
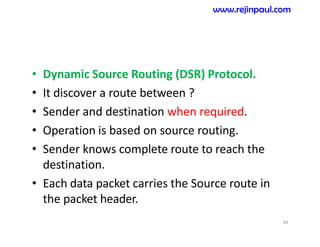
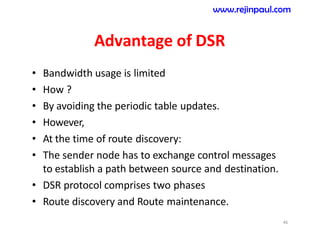
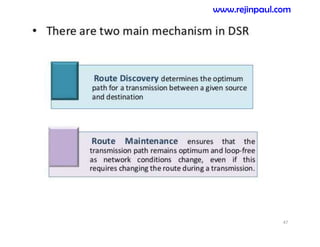
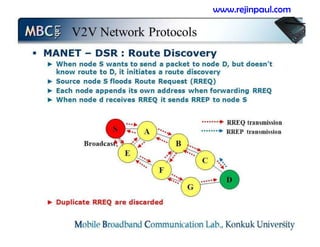
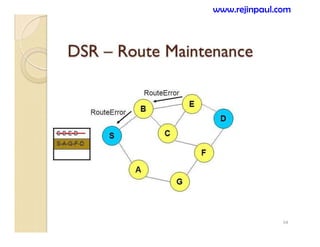
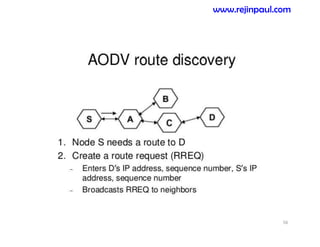
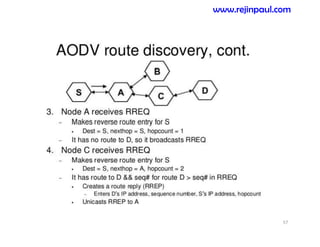
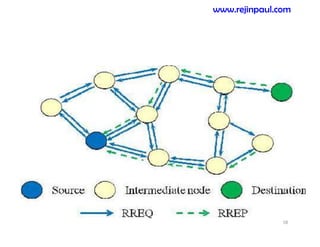
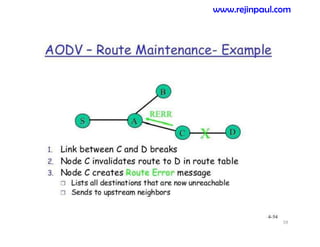
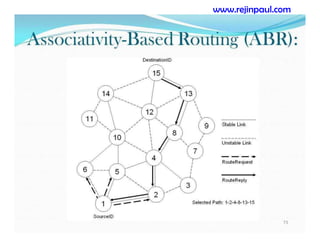
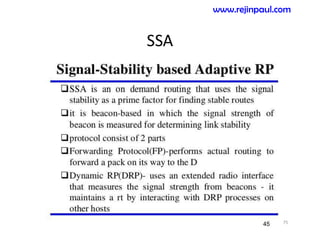
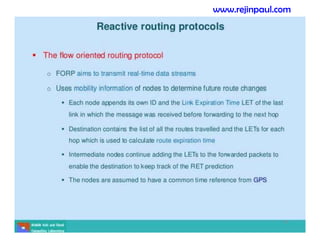
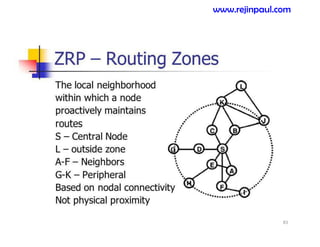
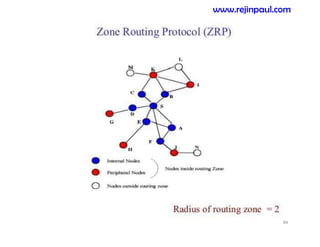
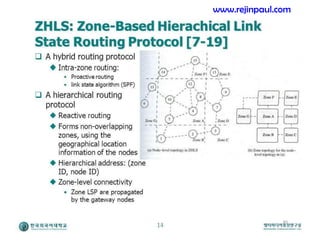
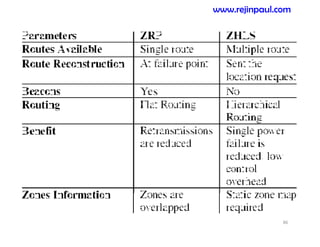
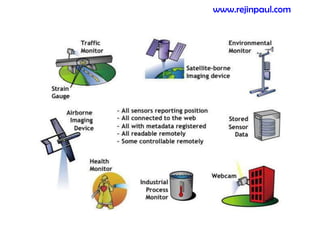
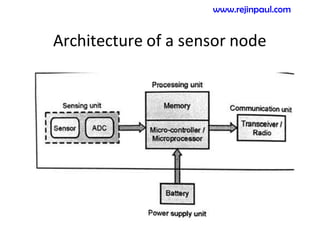
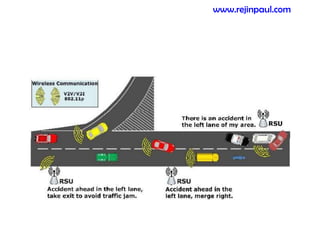
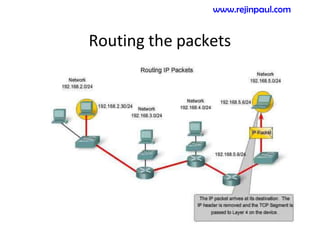
This document provides an overview of topics related to ad hoc and wireless sensor networks. It discusses fundamentals of wireless communication including different types of wireless networks like WLANs, Bluetooth, Zigbee. It also covers electromagnetic spectrum, propagation mechanisms, characteristics of wireless channels including path loss, fading and interference. Mobile ad hoc networks and wireless sensor networks are also listed as topics to be covered.