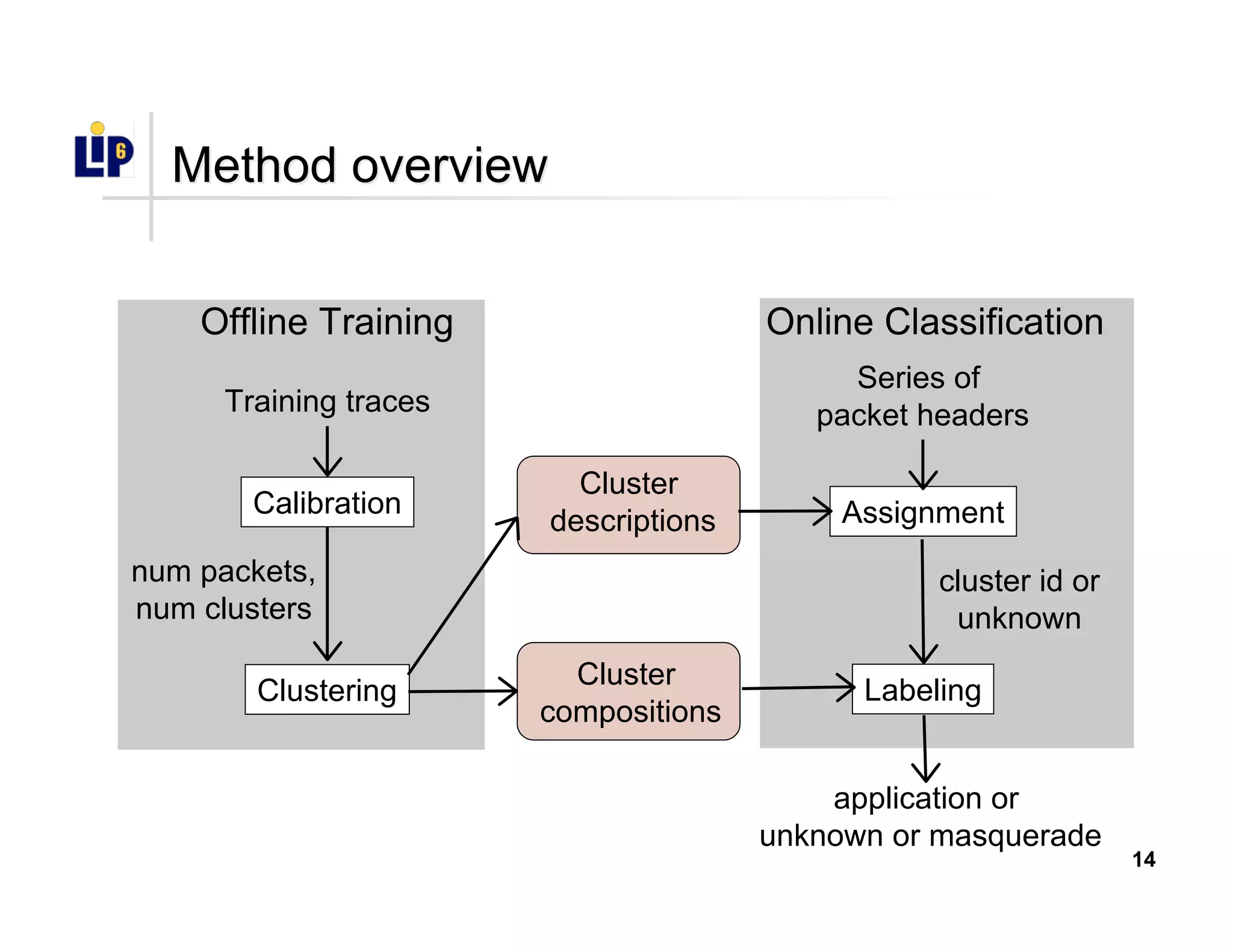
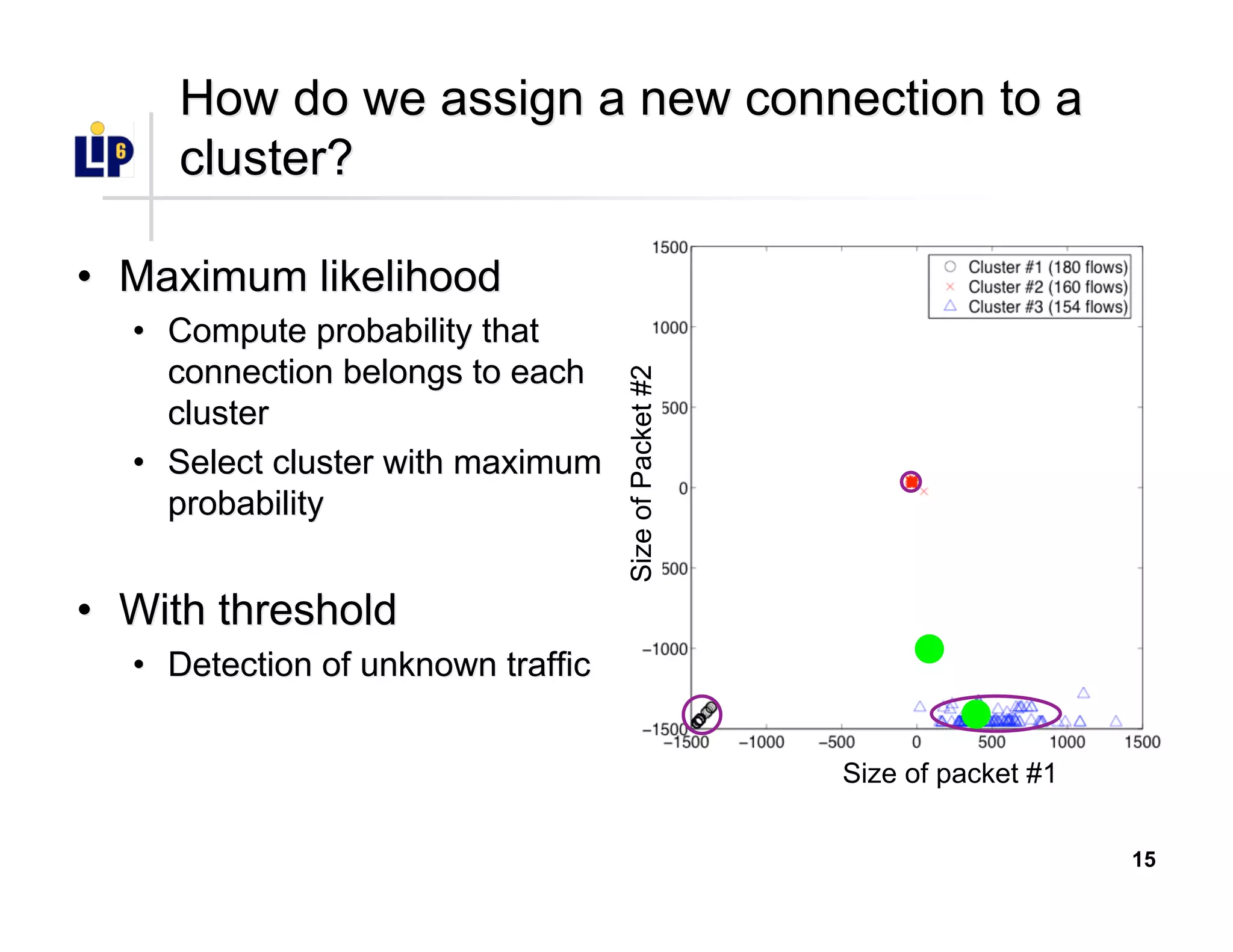
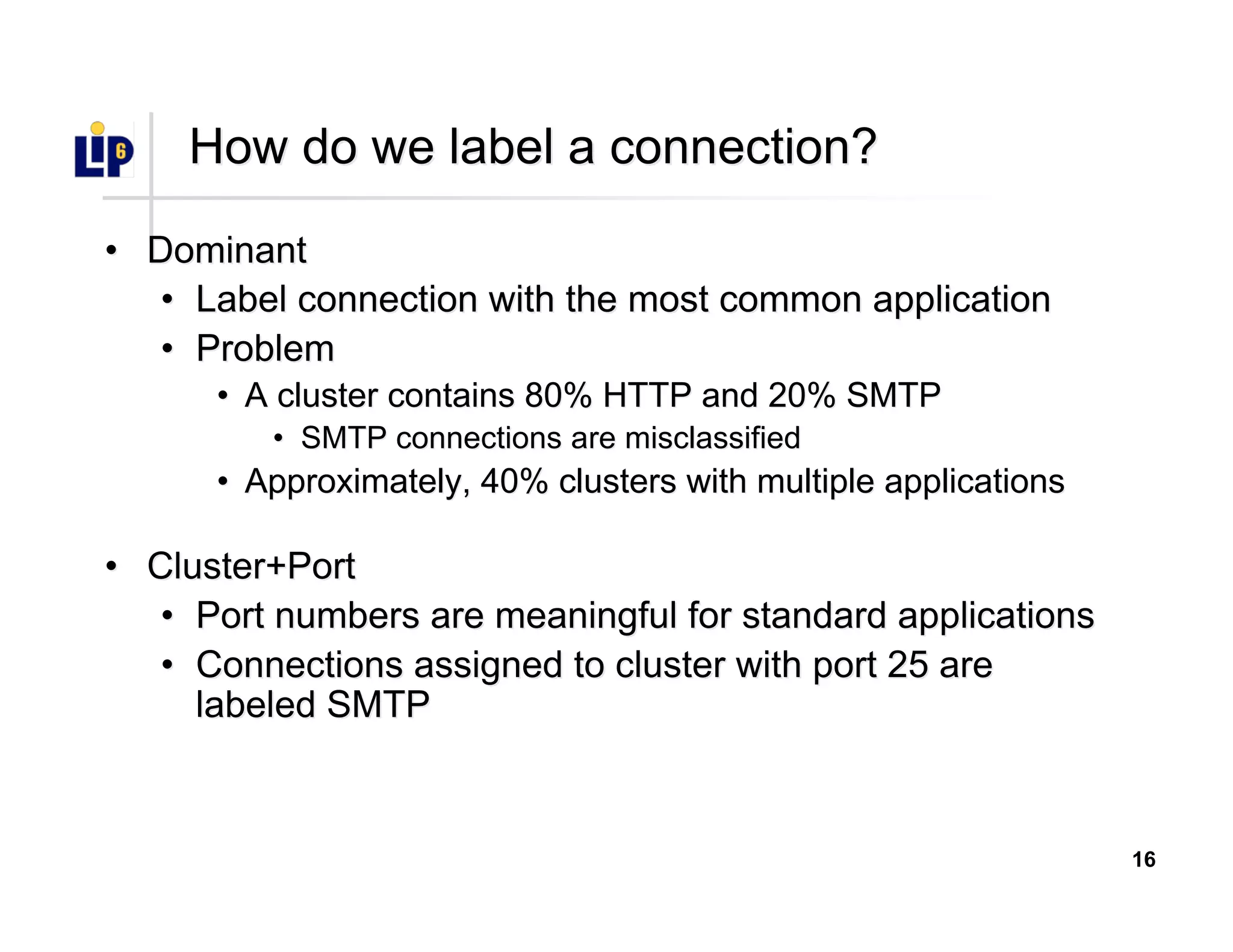
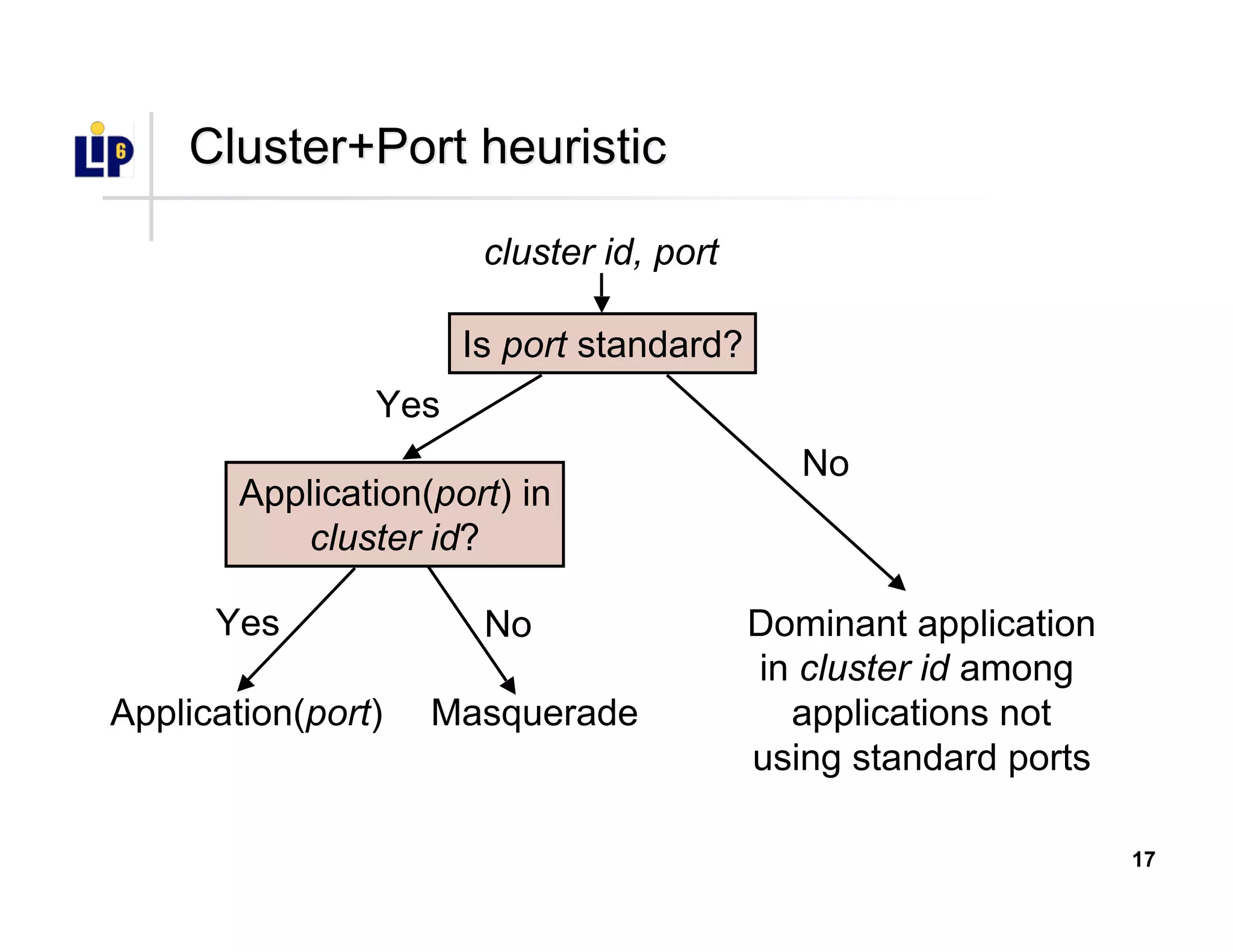
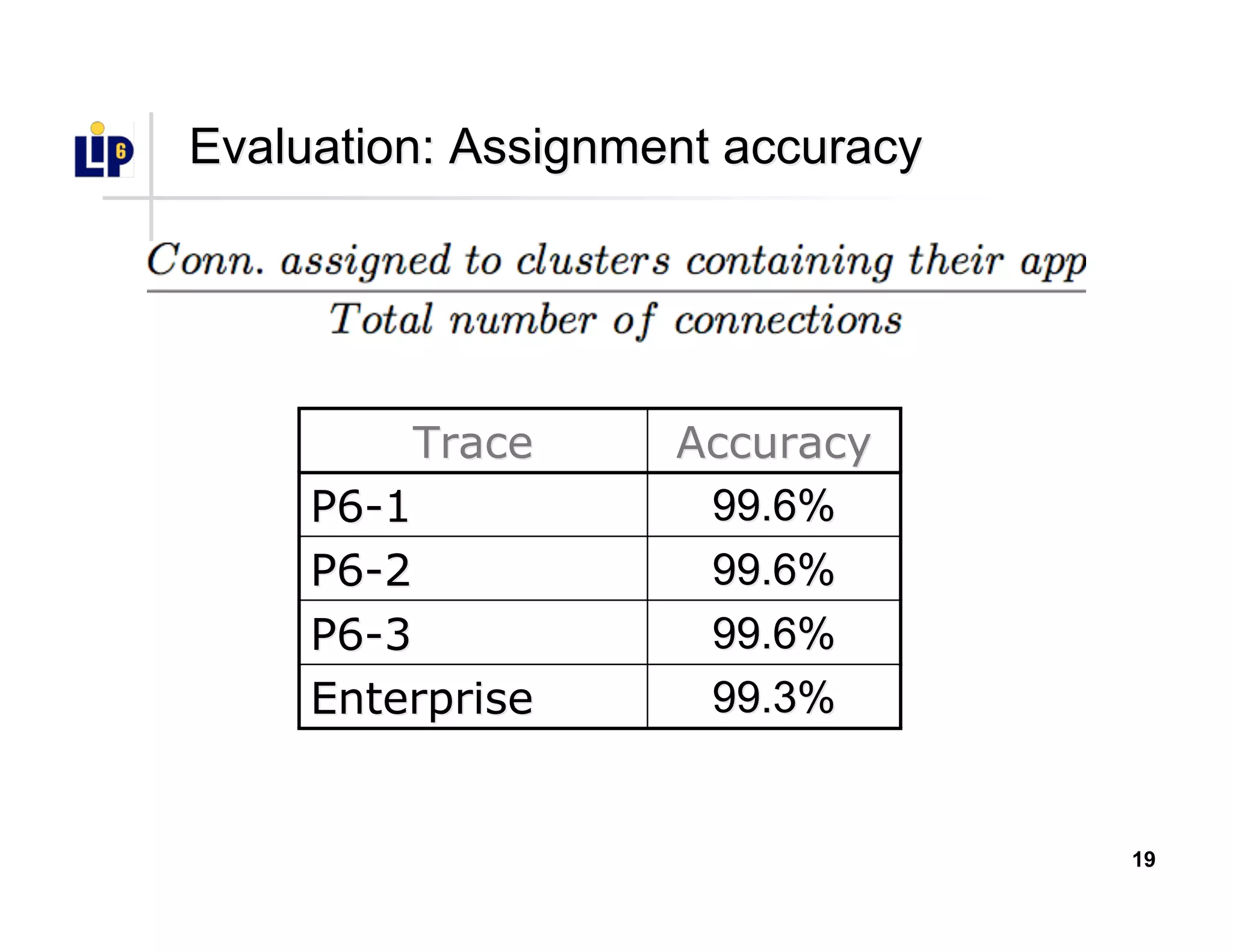
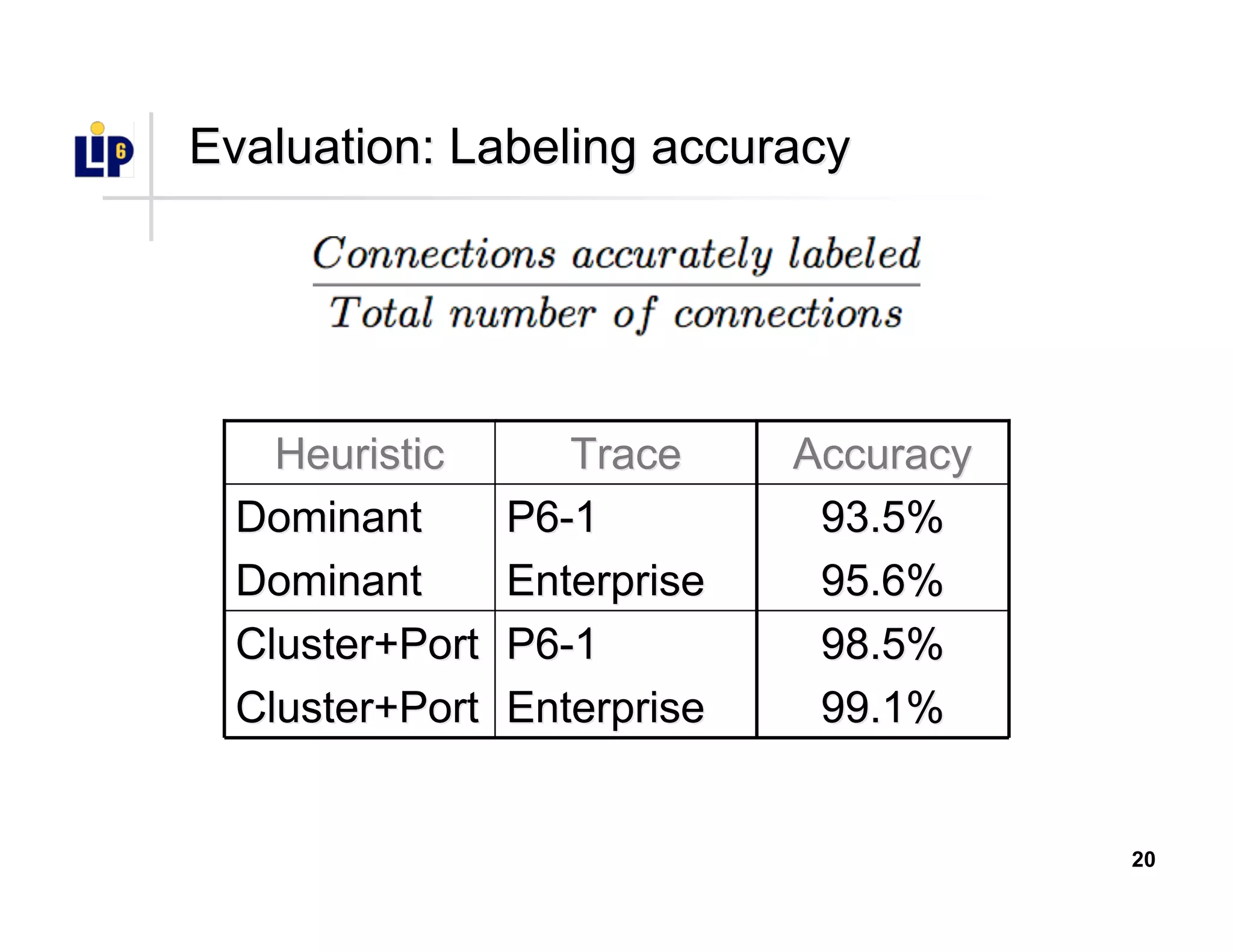
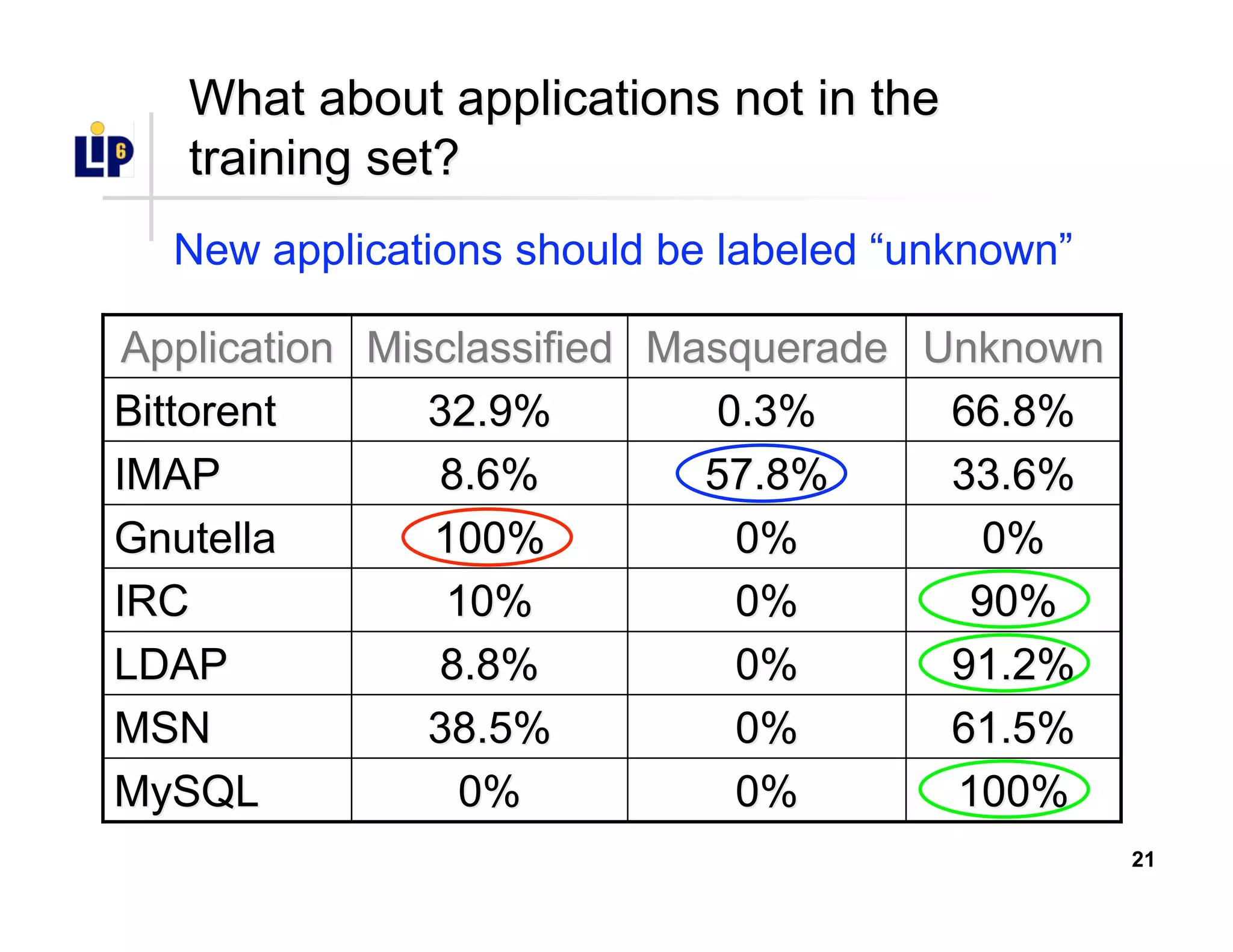
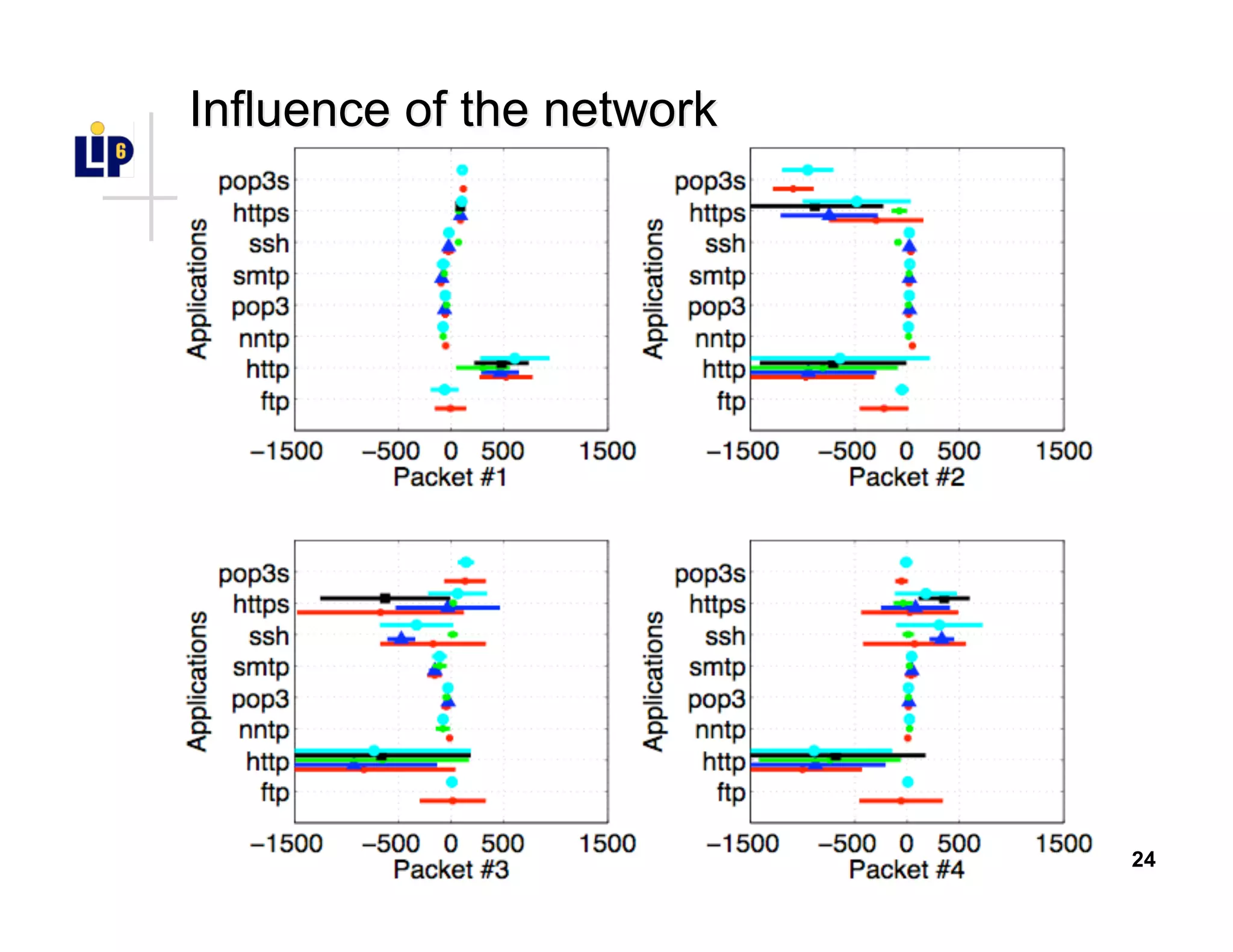
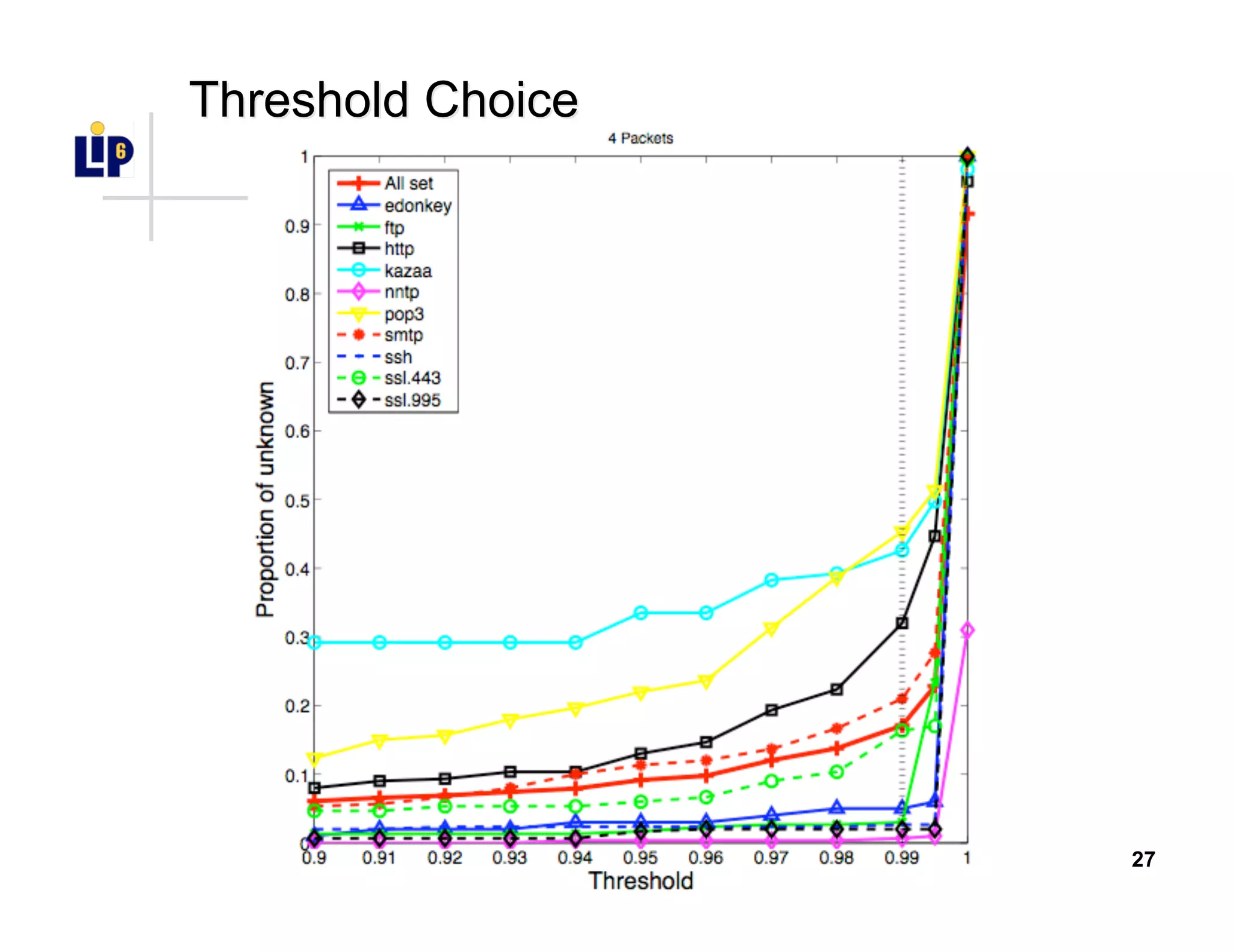
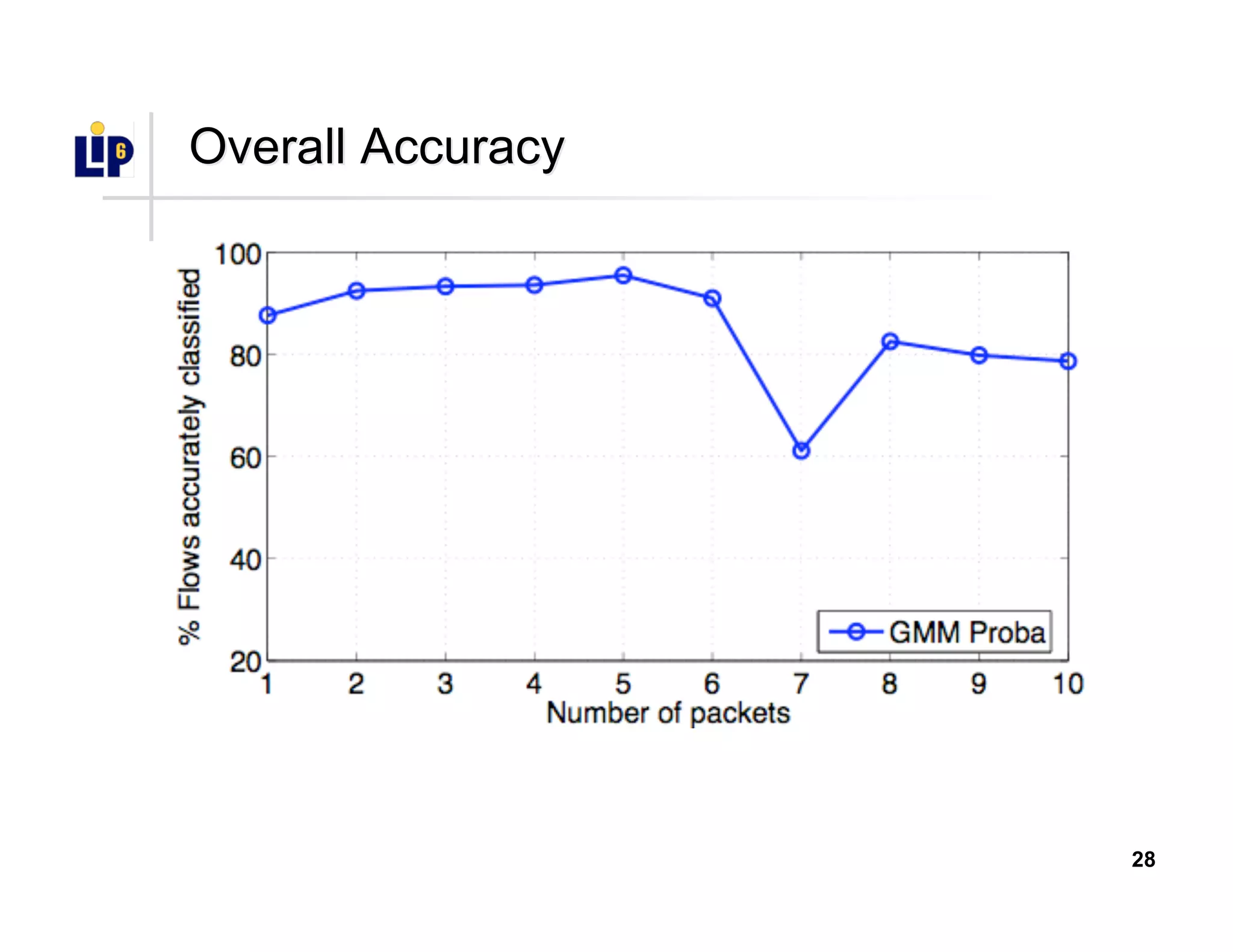
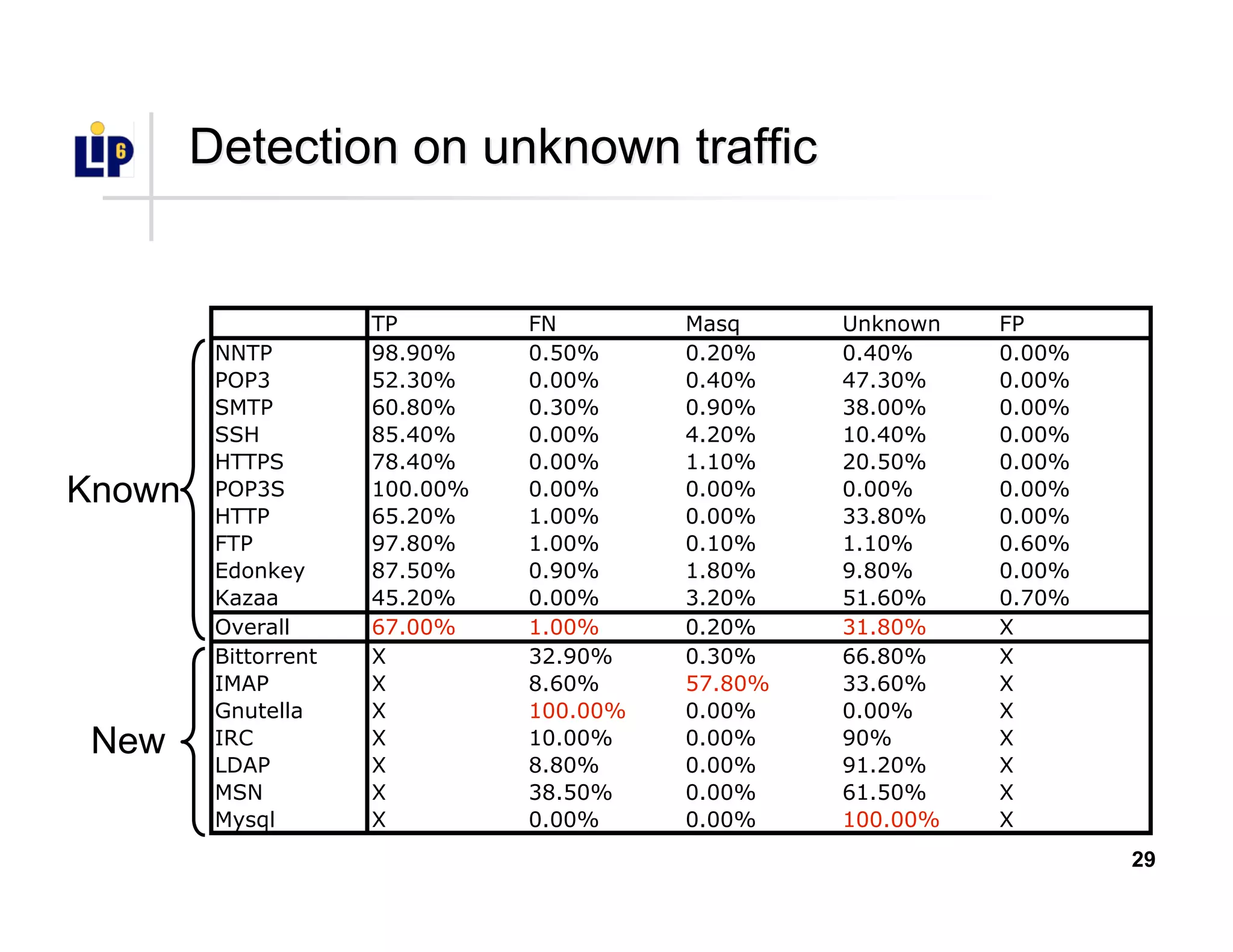
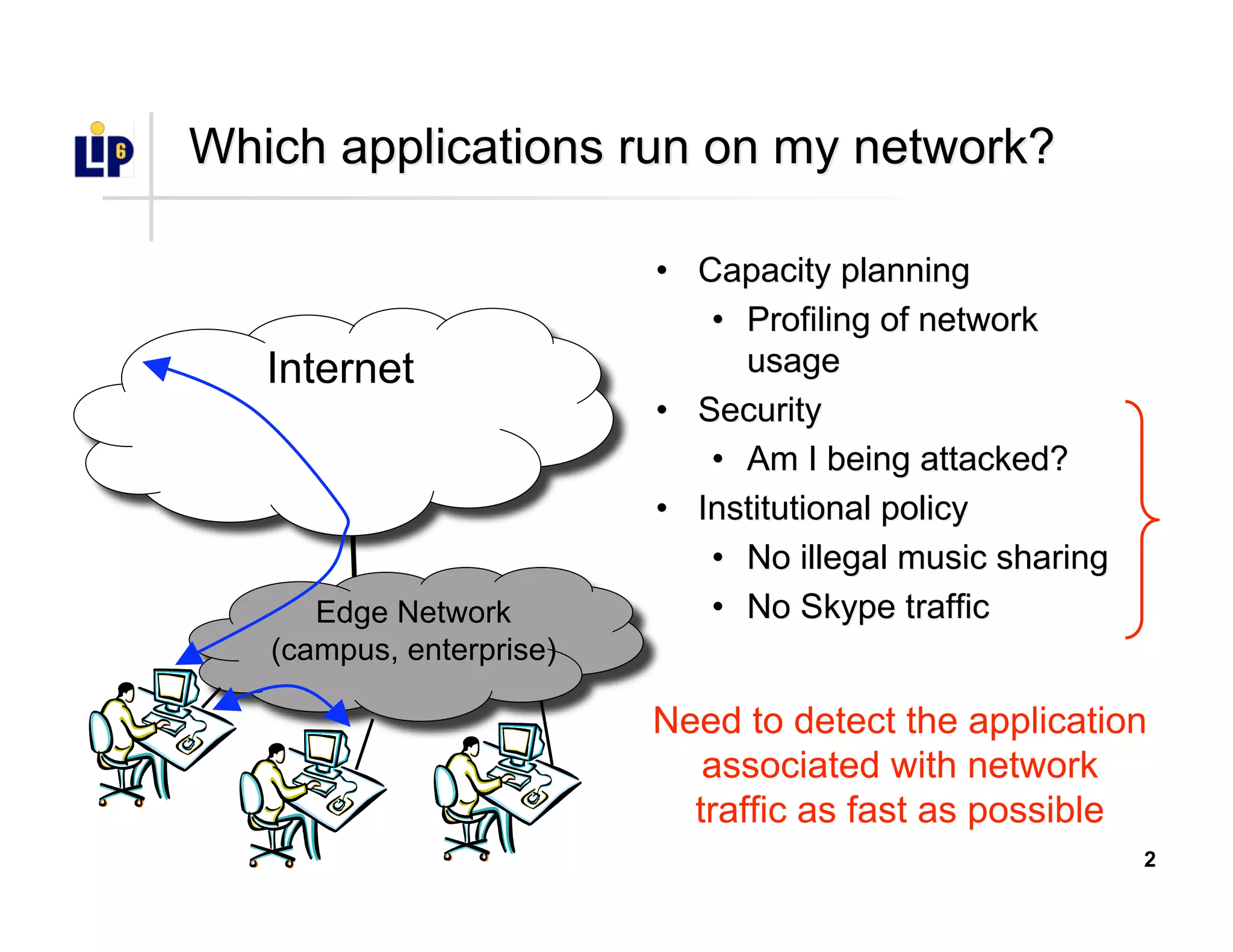
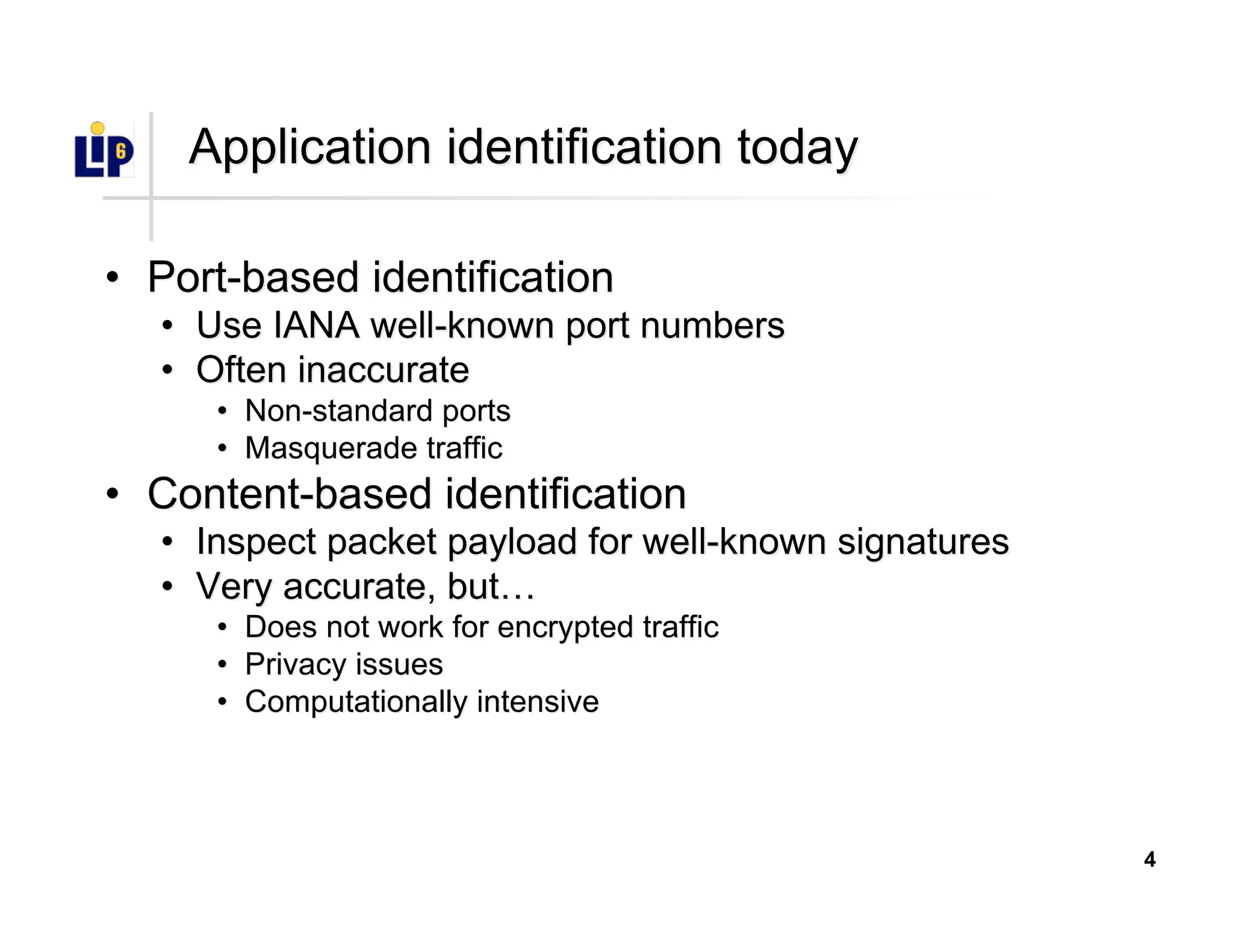
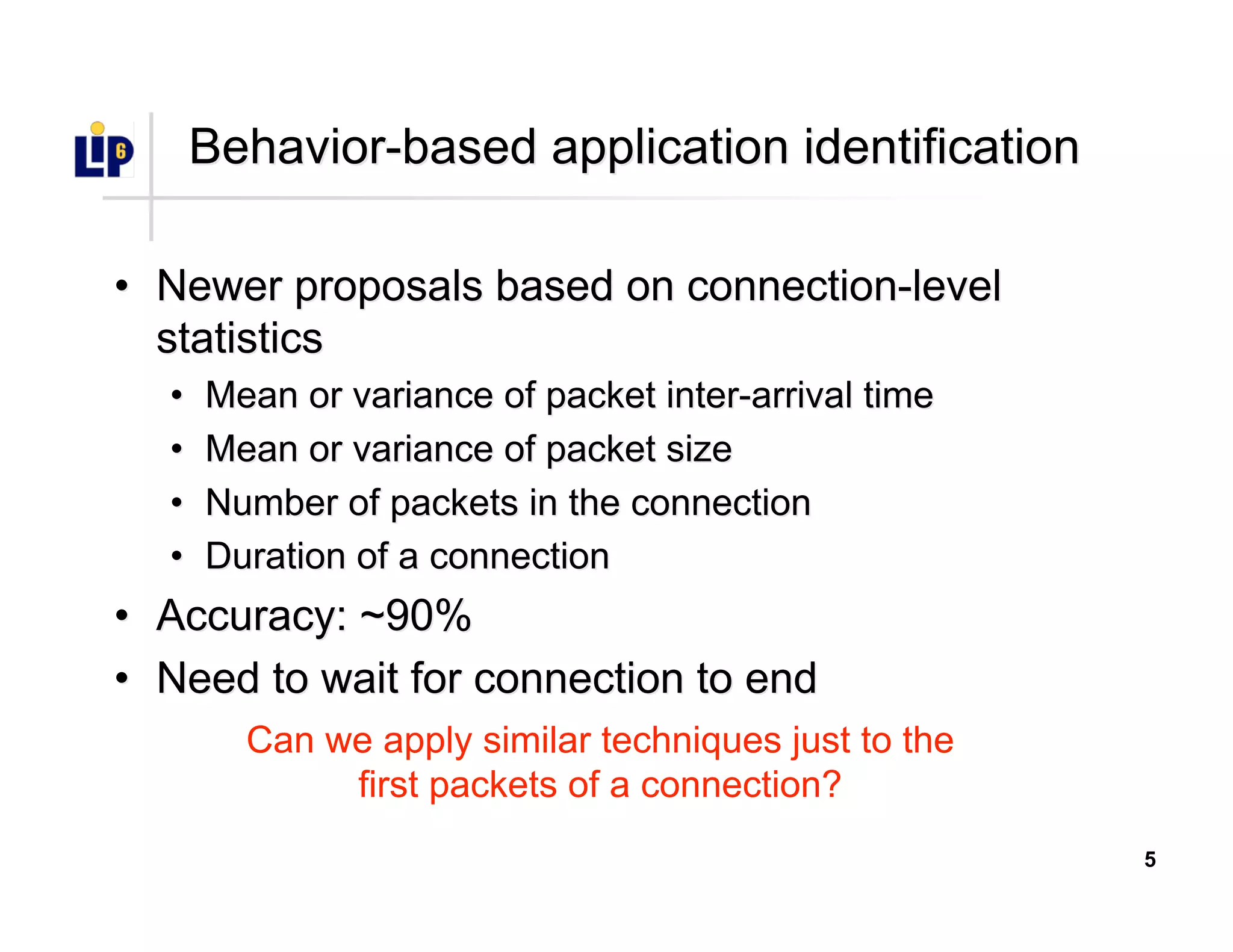
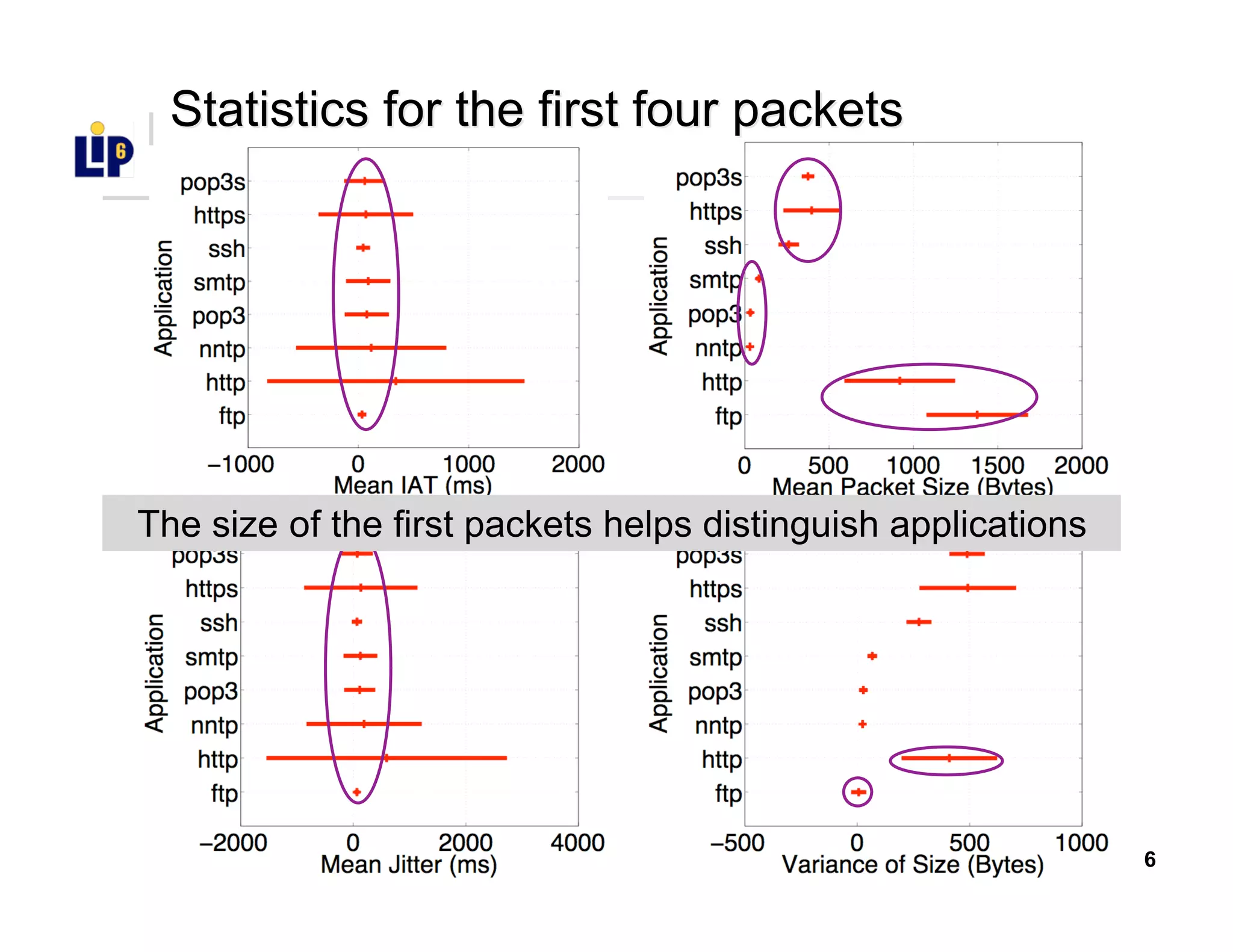
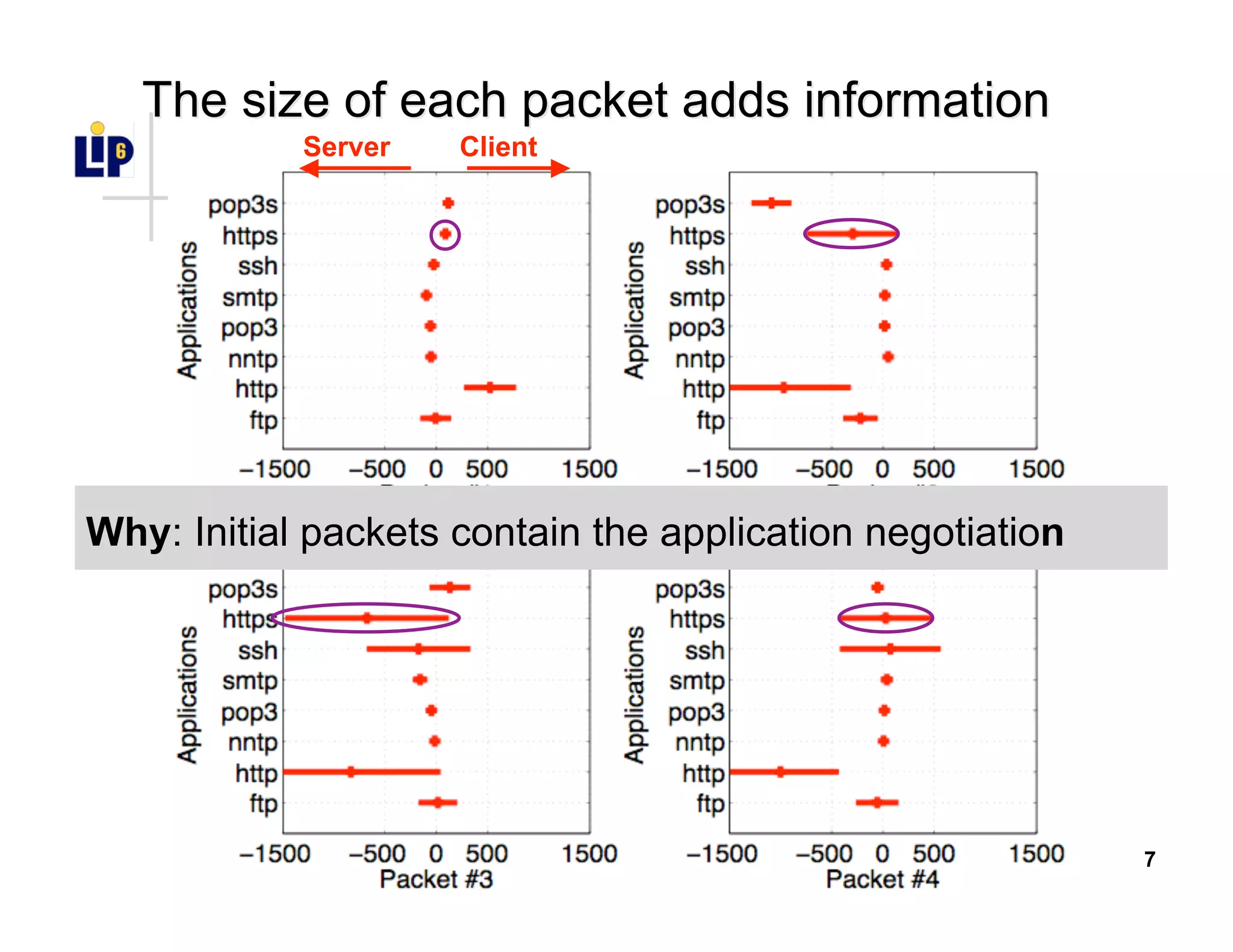
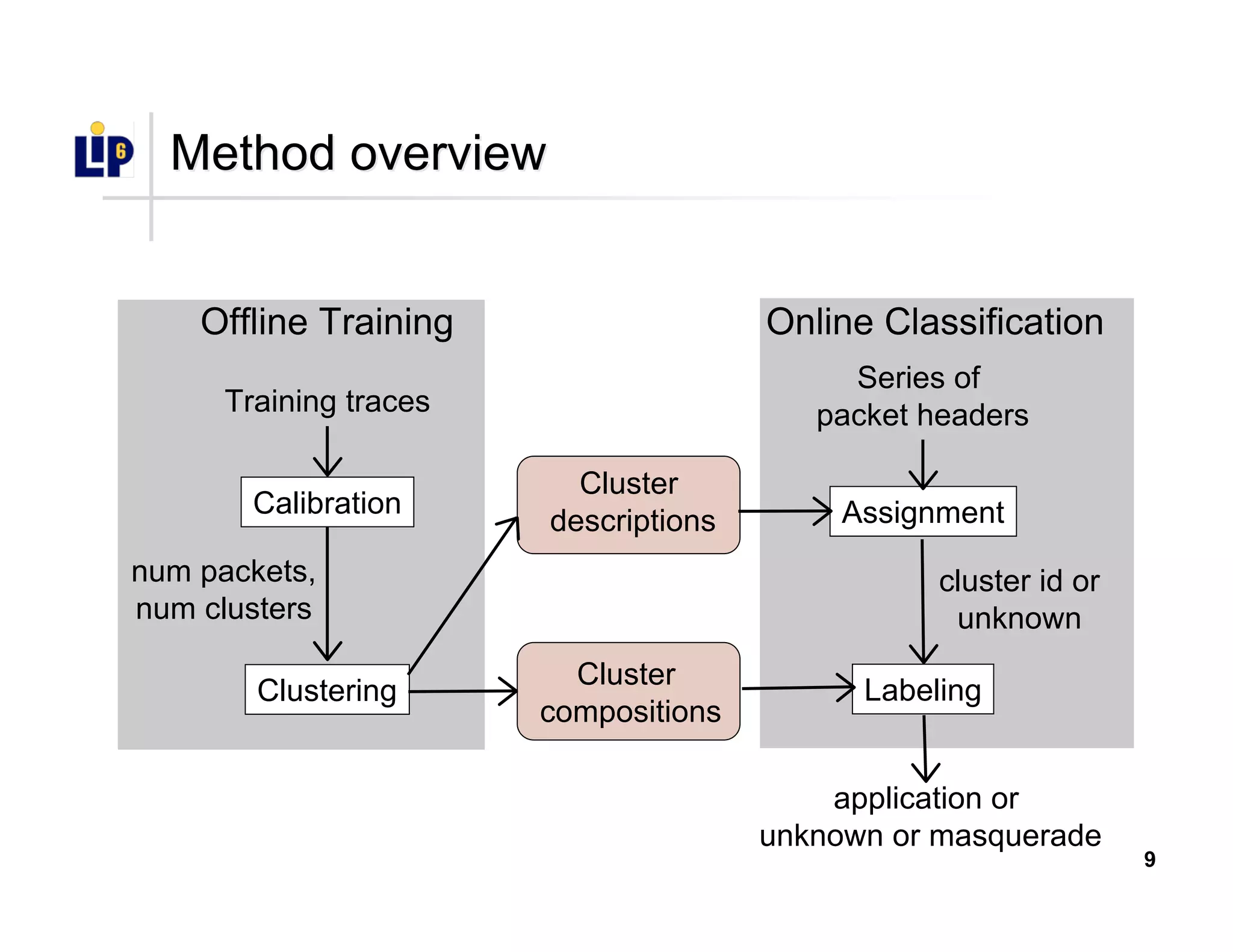
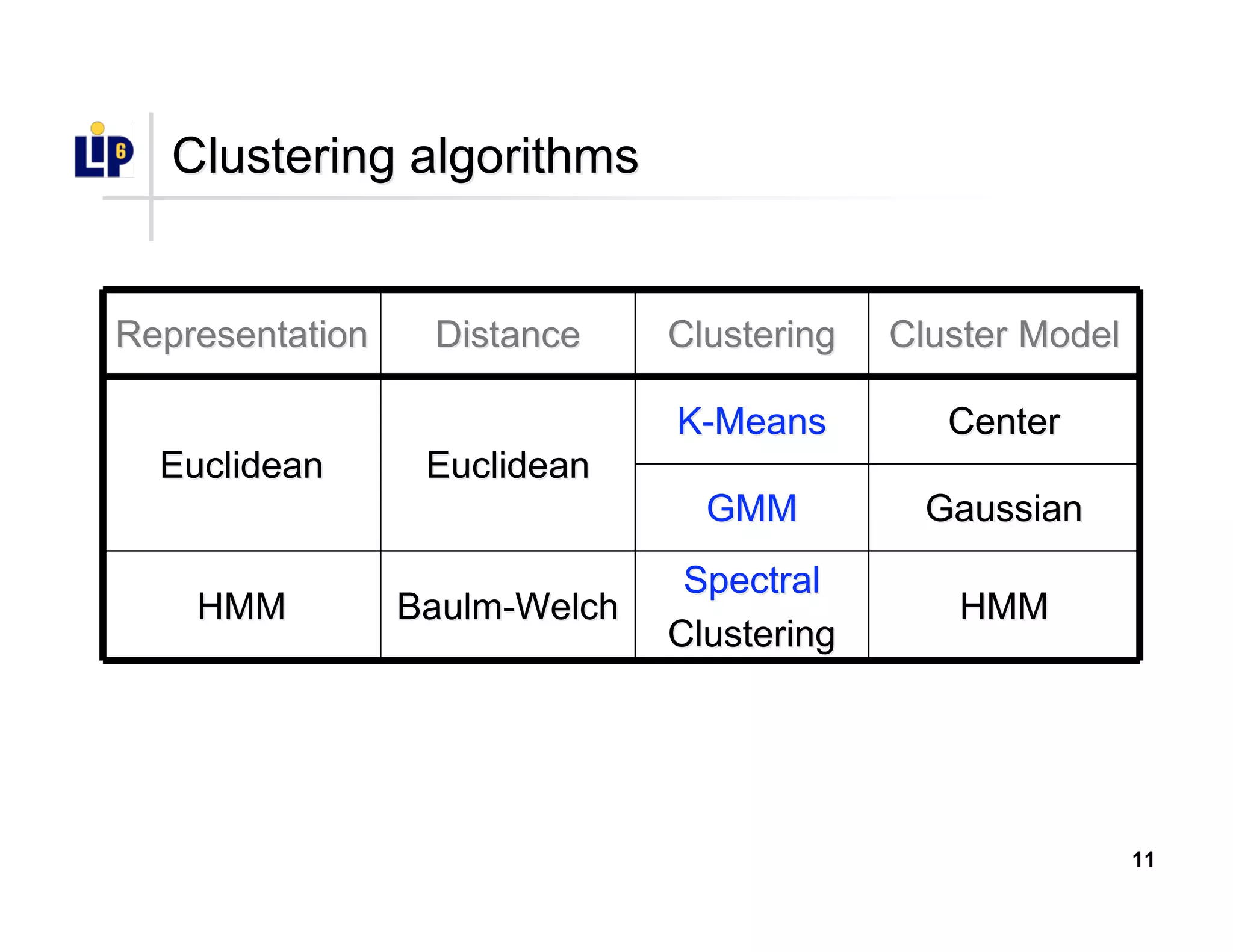
The document discusses the development of a new application identification classifier that inspects the first few packets of TCP connections to accurately determine associated applications using only TCP/IP header information. It compares traditional port-based and content-based identification methods and introduces behavior modeling through clustering algorithms, achieving high accuracy in application detection. Ongoing work involves refining traffic detection, particularly for encrypted traffic, and improving the classification of unknown applications.




![12
CalibrationCalibration
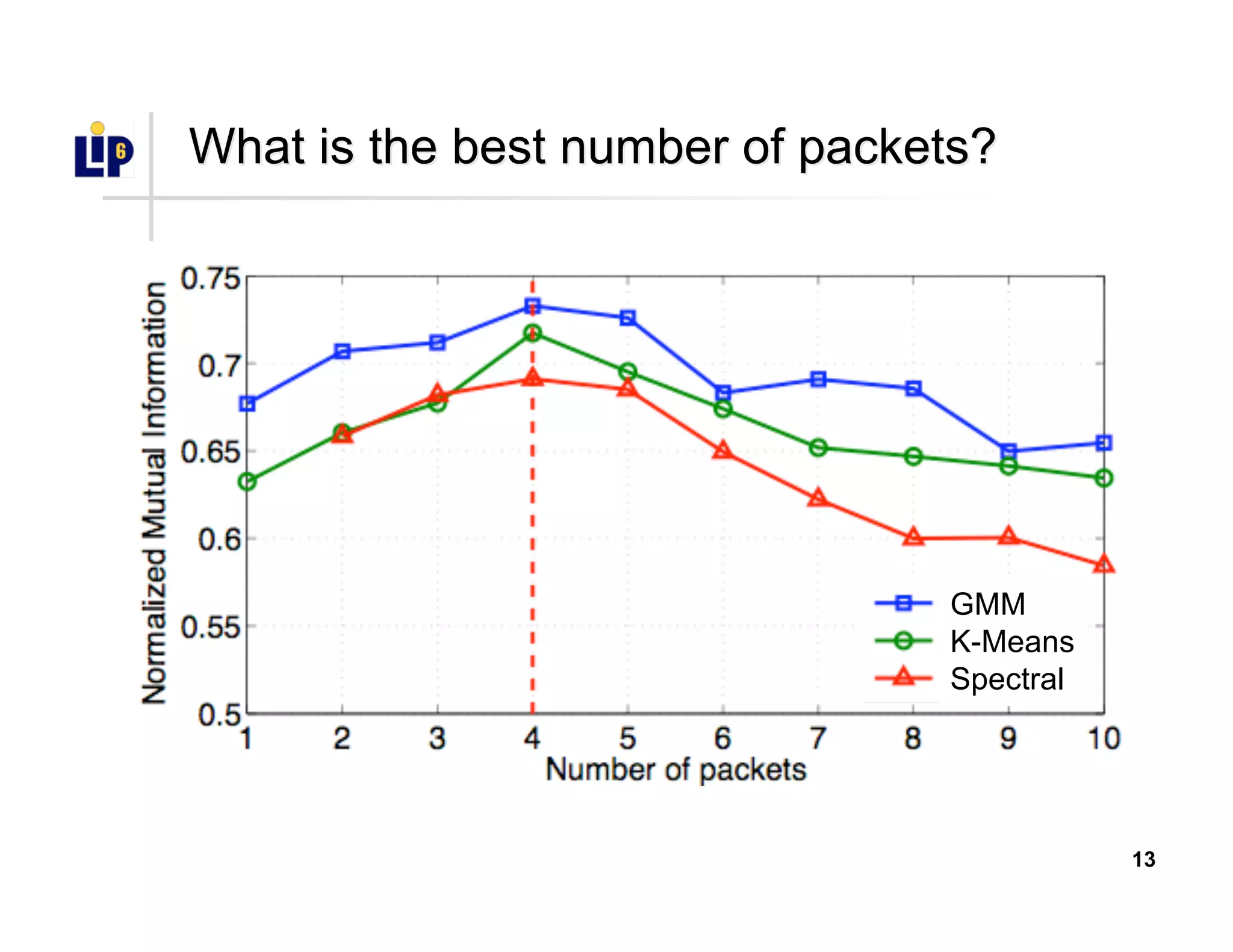
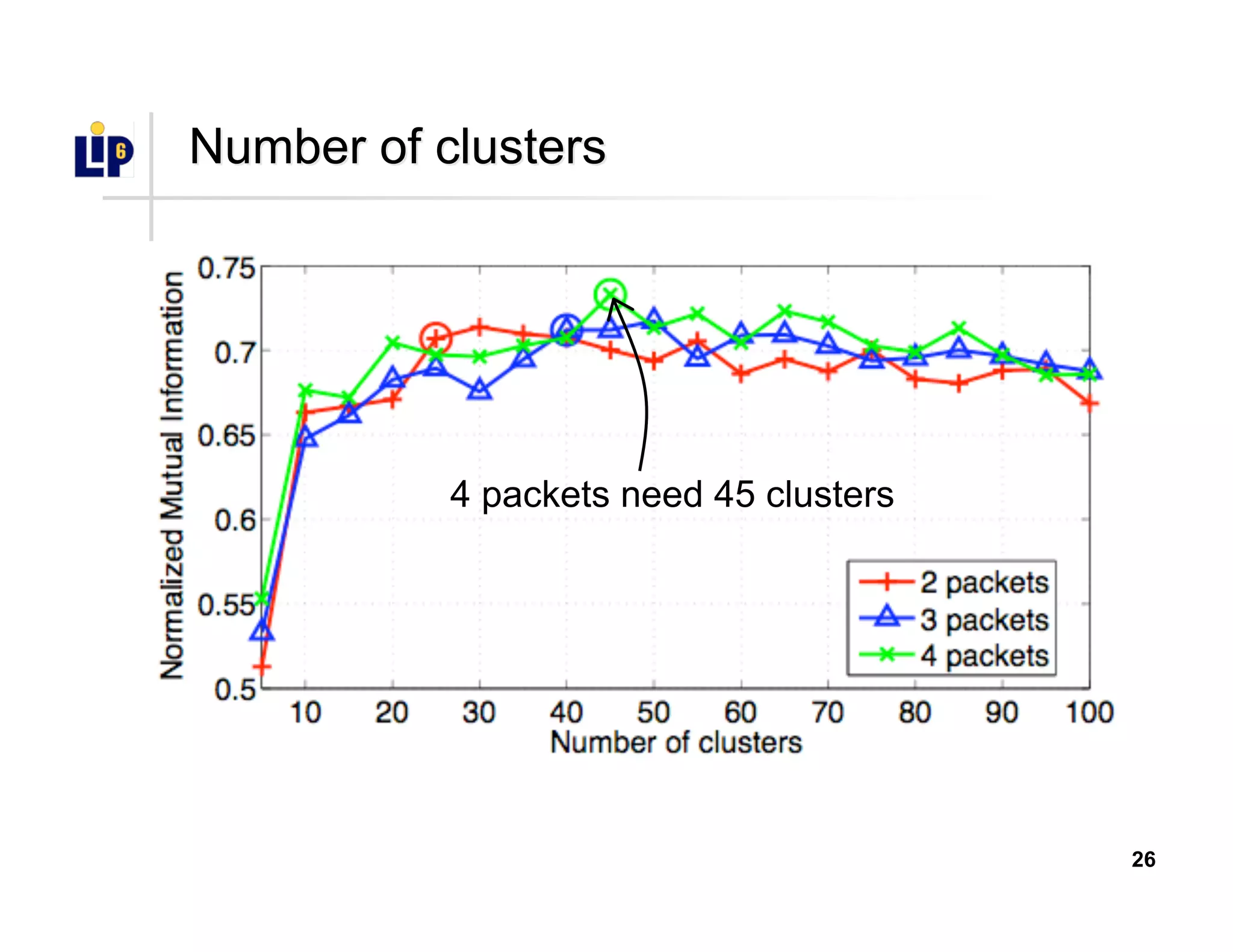
•• Select number of packets and clustersSelect number of packets and clusters
•• Compute clustering spanning a vast parameter spaceCompute clustering spanning a vast parameter space
•• Number of packets: [1, 10]Number of packets: [1, 10]
•• Number of clusters: [5, 100]Number of clusters: [5, 100]
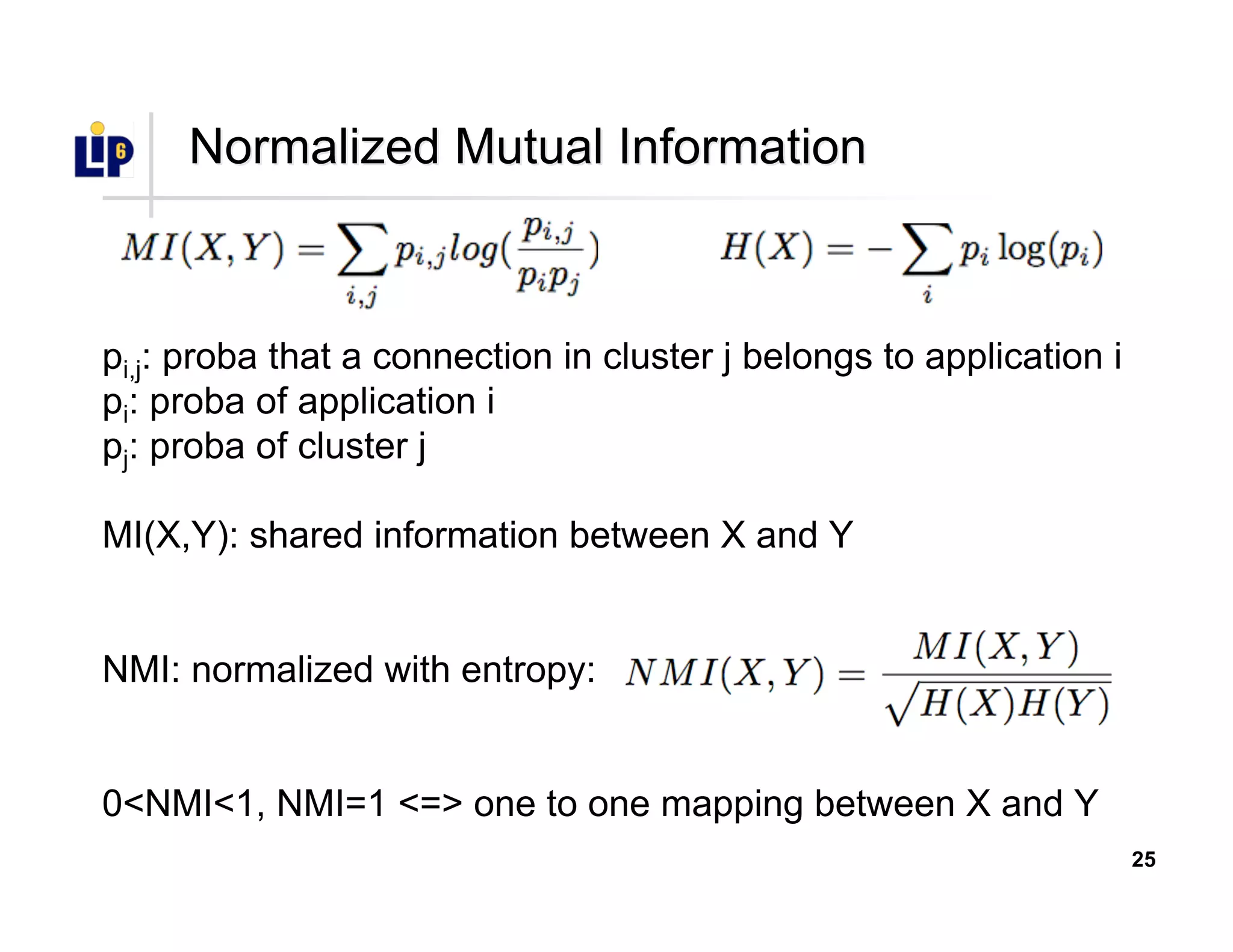
•• Metric of clustering qualityMetric of clustering quality
•• Normalized Mutual Information (NMI)Normalized Mutual Information (NMI)
•• NMI = 1: ideal clusteringNMI = 1: ideal clustering
Distribution of
applications
Distribution of
clusters
Mutual
Information
Normalized by
the entropies](https://image.slidesharecdn.com/slides-conext2006-150406070937-conversion-gate01/75/Early-application-identification-CONEXT-2006-12-2048.jpg)