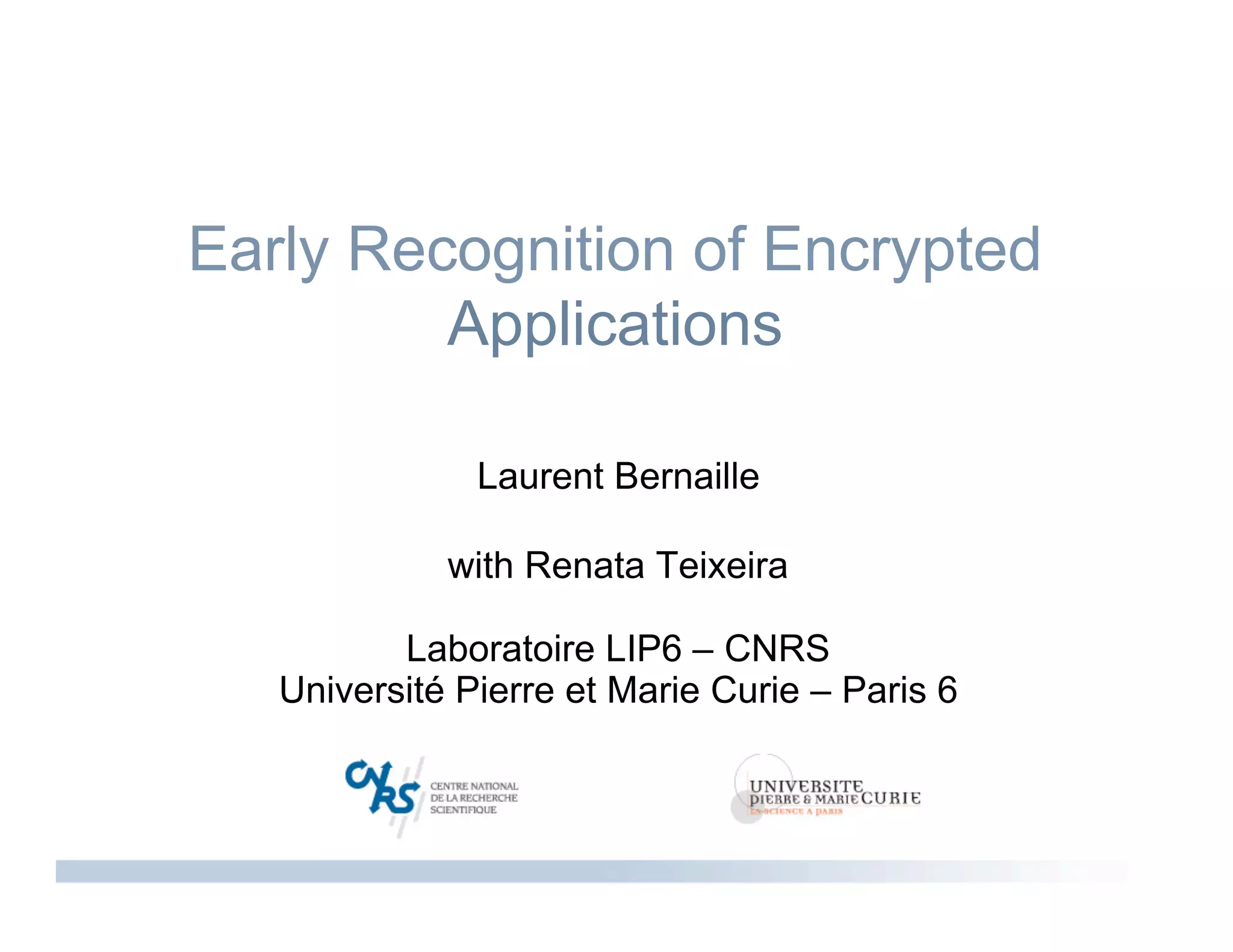
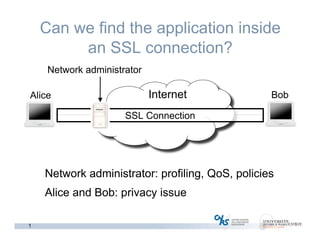
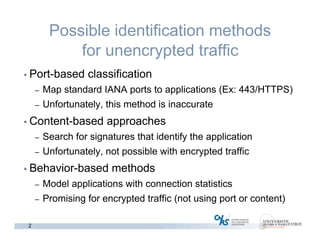
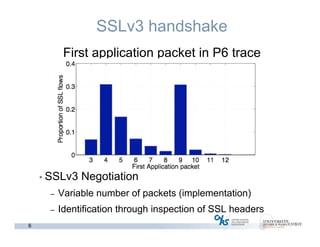
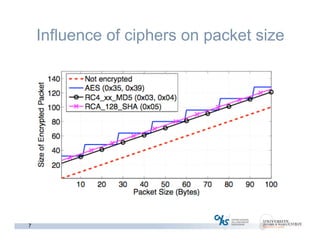
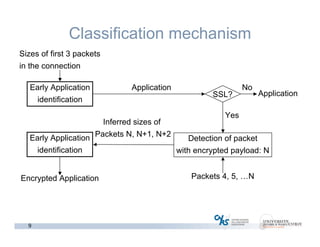
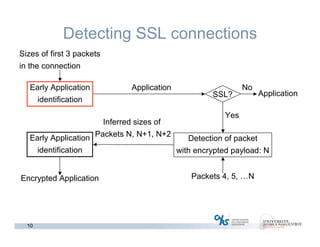
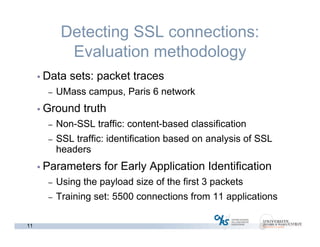
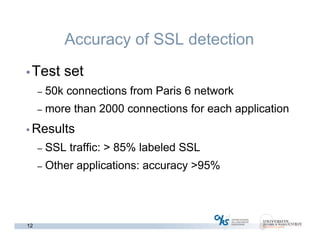
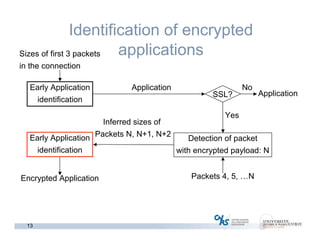
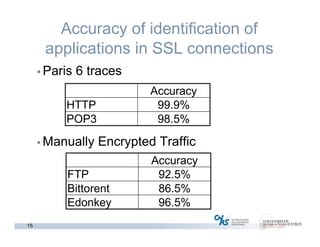
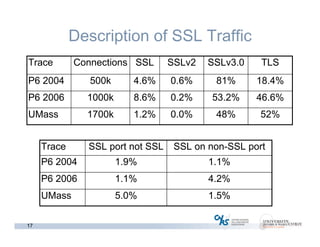
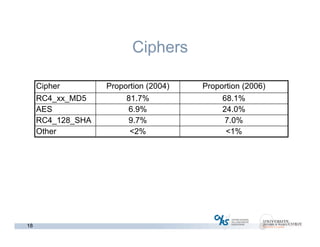
The document discusses methods for early identification of applications within SSL connections, highlighting challenges with encrypted traffic that complicate typical classification approaches. It presents an effective behavior-based method leveraging the sizes of the first packets to infer application data, achieving high accuracy in identifying applications like HTTP and POP3 over SSL. The study indicates potential for future work, including exploring other protocols like IPsec and SSH for application identification.