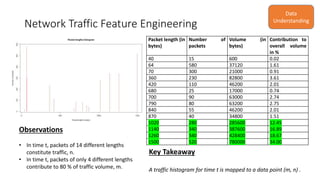
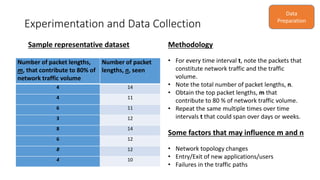
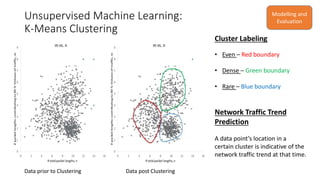
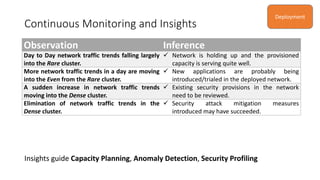
The document discusses the use of machine learning, specifically k-means clustering, to analyze and predict network traffic trends based on packet length data. It aims to provide alerts for potential network instability, detect anomalies, and derive actionable insights for better network management. Continuous monitoring and evaluation of traffic data ultimately guide capacity planning and security measures.