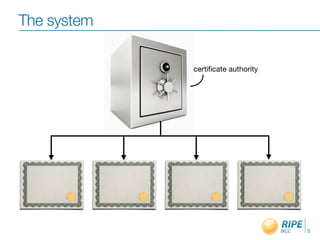
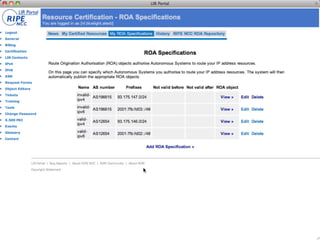
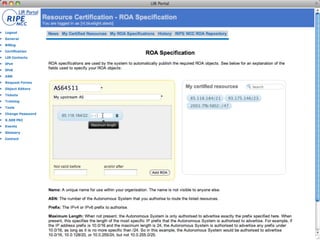
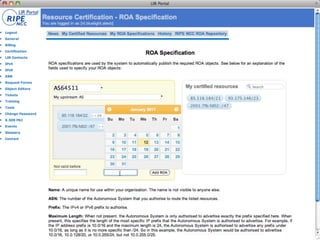
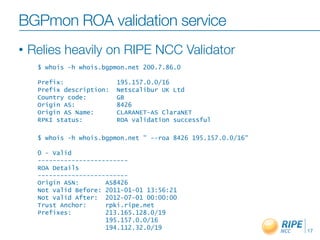
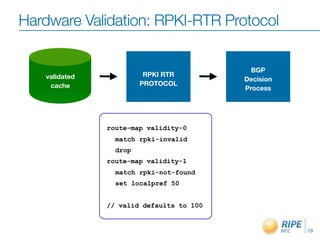
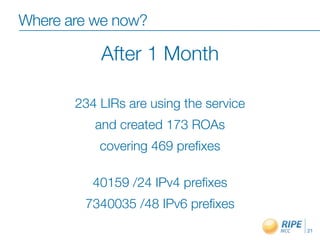
This document discusses resource certification and secure inter-domain routing. It describes how digital resource certificates issued by Regional Internet Registries (RIRs) can provide proof of resource holdership and enable route origin authorization to help secure routing and validate route announcements. The system uses X.509 certificates linked to registry information. Software and hardware tools allow validating route origins using the RPKI-RTR protocol to query a validated cache of certificates and route origin authorizations. Early adoption rates and next steps are outlined.