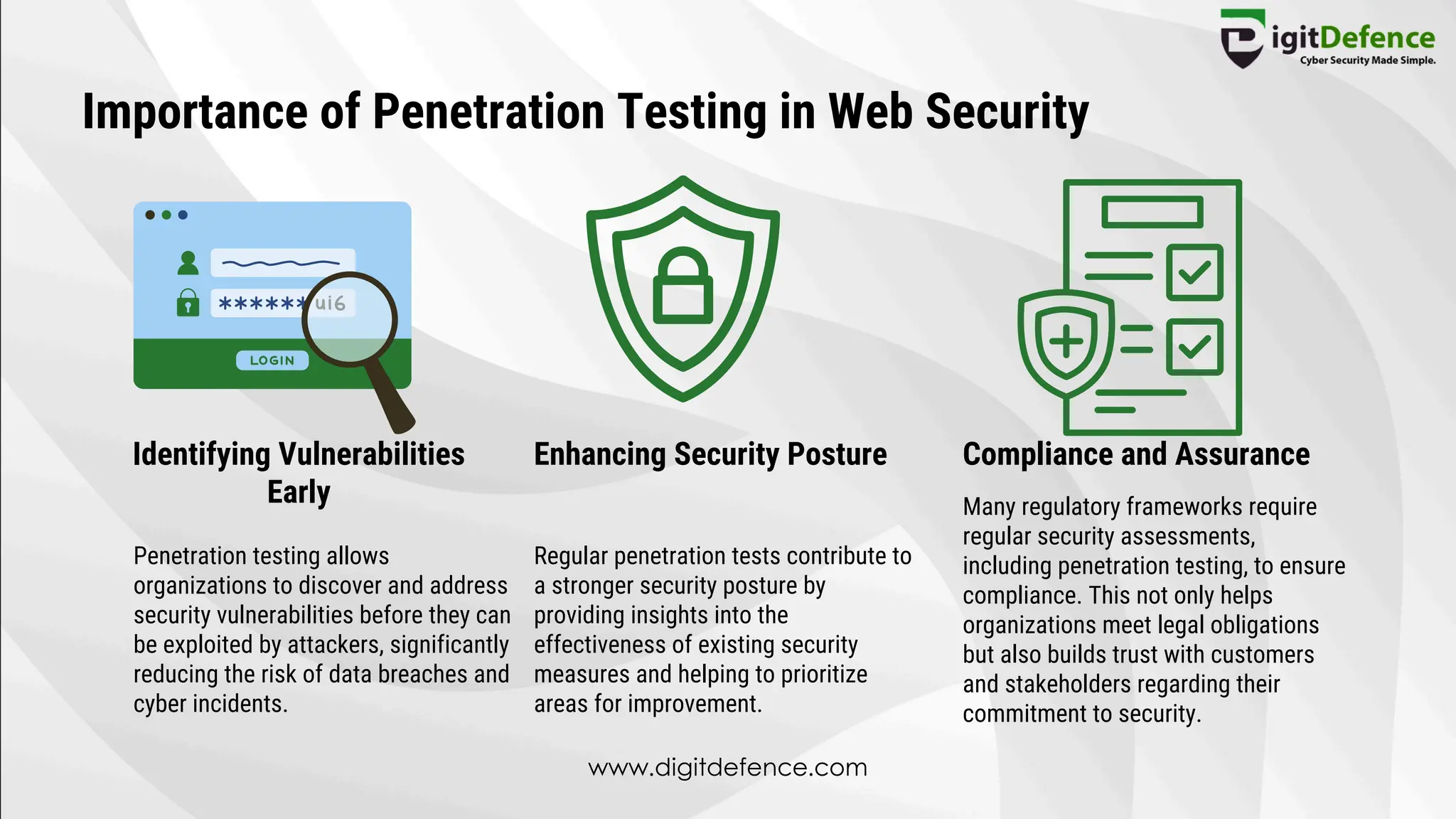
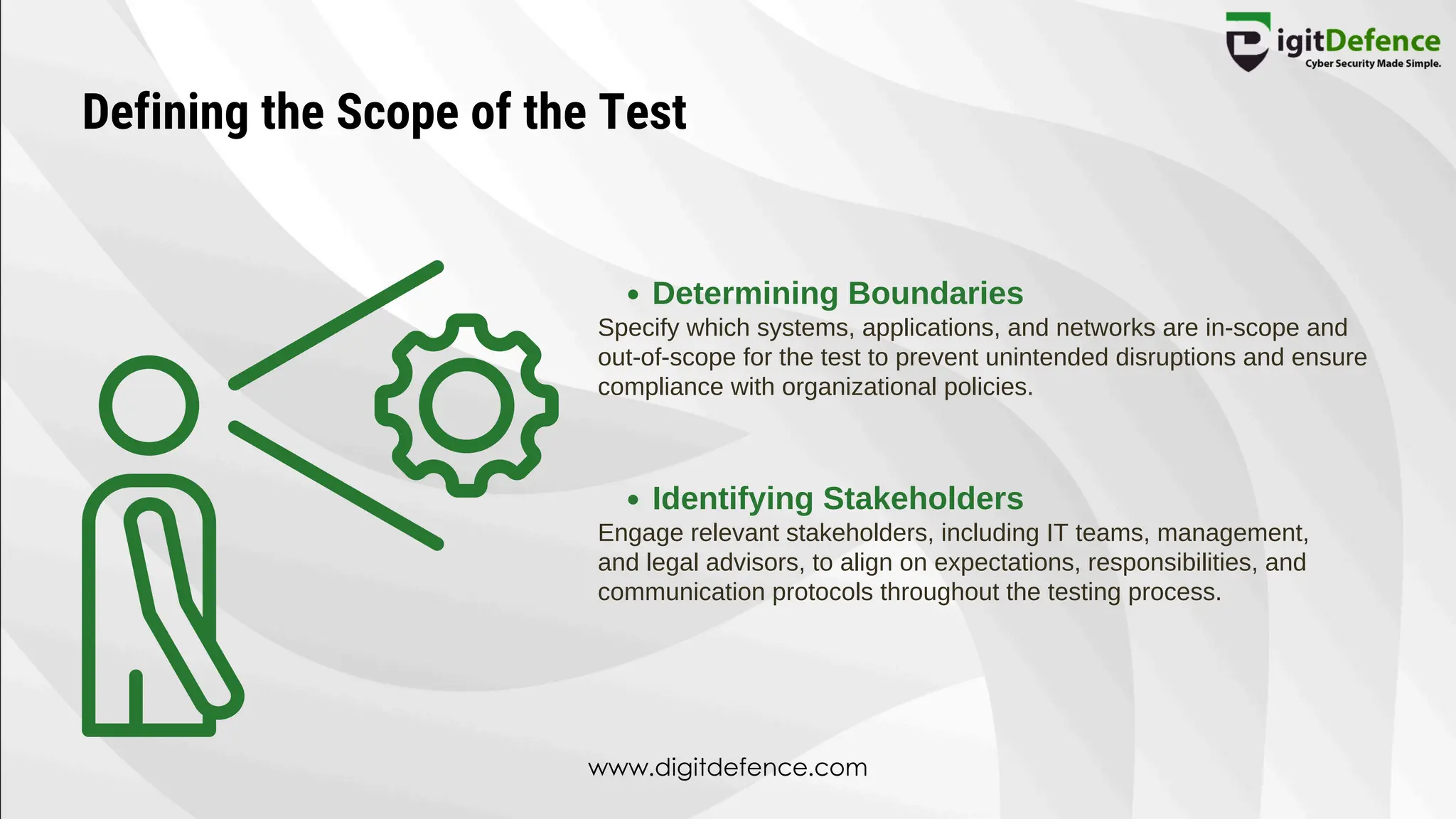
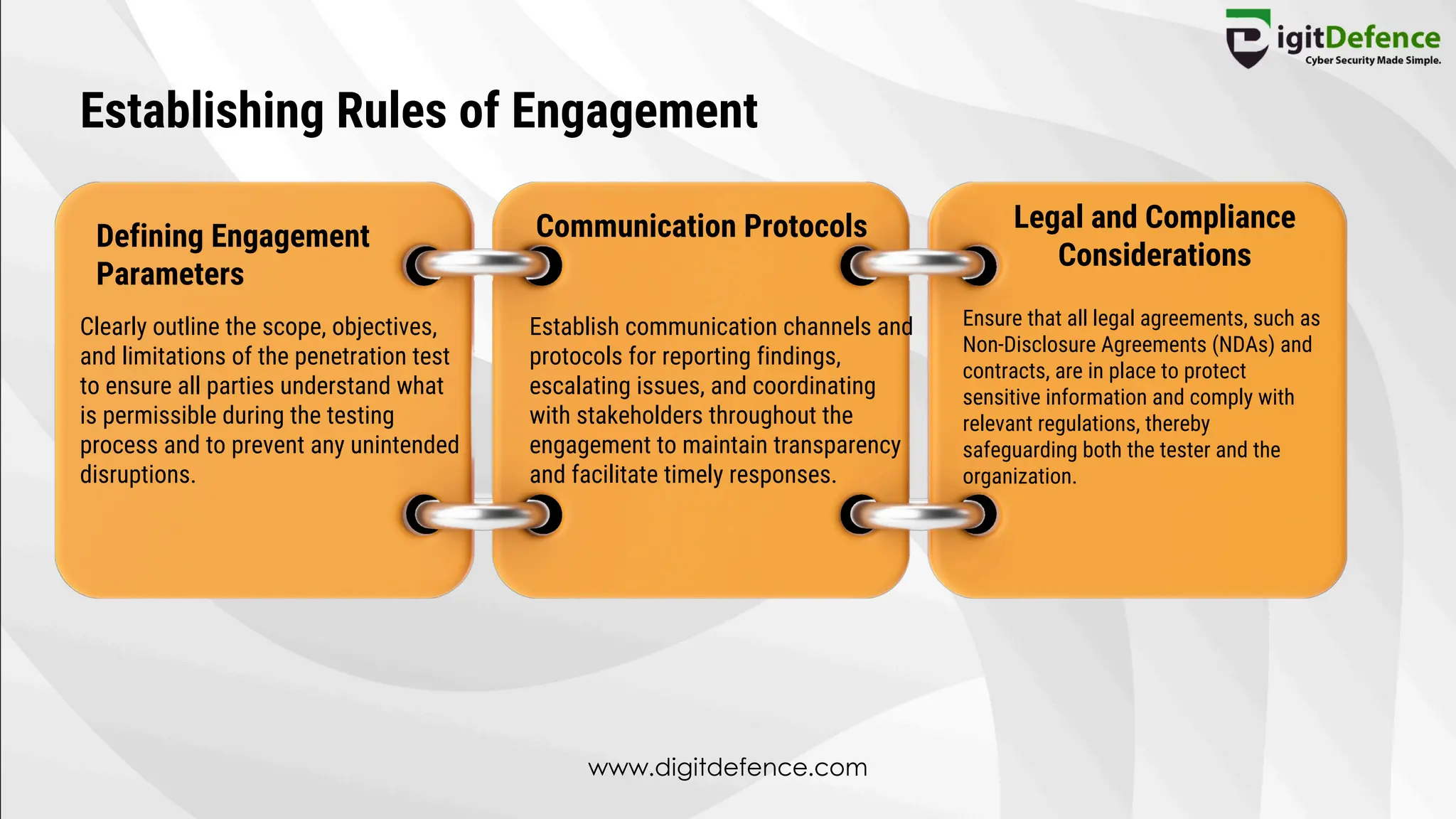
The document outlines the significance and methodologies of penetration testing for websites, defining it as a simulated cyber attack to identify possible vulnerabilities in web applications. It highlights various types of testing such as black box, white box, and gray box, and emphasizes the importance of penetration testing for improving security posture and ensuring regulatory compliance. Additionally, it details the steps involved, including defining the test scope, identifying target assets, gathering information, and strategies for exploitation and remediation.