Double hashing uses two hash functions, h1 and h2. If h1 causes a collision, h2 is used to compute an increment to probe for the next empty slot. Common definitions for h2 include h2(key)=1+key%(tablesize) or h2(key)=M-(key%M) where M is a prime smaller than the table size. Quadratic probing probes locations using the formula h(key)=[h(key)+i^2]%table_size. Rehashing doubles the table size when the load factor exceeds 0.75, reinserting all elements to maintain a low load factor.



![• Example: load the keys 18,26,35,9,64,47,96,36 and 70 in this order, in an empty
hash table of size 13.
• h1(key)=key%13
• h2(key)= 7- key%7
H(key)=[h1(key)+i*h2(key)]%13
DEPARTMENT OF COMPUTER ENGINEERING, Sanjivani COE, Kopargaon 5](https://image.slidesharecdn.com/doublehashing-230705084211-d6101b38/85/Double-Hashing-pptx-5-320.jpg)

![e.g. 4371,1323,6173,4199,4344,9699,1889
h1(x)=key %10
h2(x)= 7 – (x %7)
h(key)=H(key)=[h1(key)+i*h2(key)]%10
DEPARTMENT OF COMPUTER ENGINEERING, Sanjivani COE, Kopargaon 7
0
1
2
3
4
5
6
7
8
9
1889
4371
9699
1323
6173
4344
4199
6173=3
h2(key)= 7-6=1
H(key)= (3+1*1)%10= 4
4344=4
h2(key)= 7- key % 7 =43
H(key)= (3+1*3)%10= 6
9699=9
h2(key)= 7- key % 7 =3
H(key)= (9+1*3)%10=2
1889=9
h2(key)= 7- key % 7 =1
H(key)= (9+1*1)%10=0](https://image.slidesharecdn.com/doublehashing-230705084211-d6101b38/85/Double-Hashing-pptx-7-320.jpg)
![// function to insert key into hash table
void insertHash(int key)
{
// if hash table is full
if (isFull())
return;
// get index from first hash
int index = hash1(key);
// if collision occurs
if (ht[index] != -1) {
// get index2 from second hash
int step= hash2(key);
int i = 1;
while (1) {
DEPARTMENT OF COMPUTER ENGINEERING, Sanjivani COE, Kopargaon 8
// get newIndex
int newIndex = (index + i * step) %
TABLE_SIZE;
// if no collision occurs, store the key
if (ht[newIndex] == -1) {
ht[newIndex] = key;
break;
}
i++;
}
}
// if no collision occurs
else
ht[index] = key;
}](https://image.slidesharecdn.com/doublehashing-230705084211-d6101b38/85/Double-Hashing-pptx-8-320.jpg)
![// function to search key in hash table
void search(int key)
{
int index1 = hash1(key);
int step = hash2(key);
int i = 0;
while (ht[(index1 + i * step) % TABLE_SIZE] != key) {
if (ht[(index1 + i * step) % TABLE_SIZE] == -1) {
cout << key << " does not exist" << endl;
return; }
i++;
}
cout << key << " found" << endl; }
DEPARTMENT OF COMPUTER ENGINEERING, Sanjivani COE, Kopargaon 9](https://image.slidesharecdn.com/doublehashing-230705084211-d6101b38/85/Double-Hashing-pptx-9-320.jpg)

![• In quadratic probing, empty location is searched using the formula,
h(key)=[h(key) + i2] % table_size
• Let hash(x) be the slot index computed using the hash function.
• If the slot hash(x) % S is full, then we try (hash(x) + 1*1) % S.
• If (hash(x) + 1*1) % S is also full, then we try (hash(x) + 2*2) % S.
• If (hash(x) + 2*2) % S is also full, then we try (hash(x) + 3*3) % S.
• This process is repeated for all the values of i until an empty slot is found.
DEPARTMENT OF COMPUTER ENGINEERING, Sanjivani COE, Kopargaon 11](https://image.slidesharecdn.com/doublehashing-230705084211-d6101b38/85/Double-Hashing-pptx-11-320.jpg)
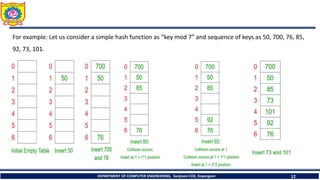
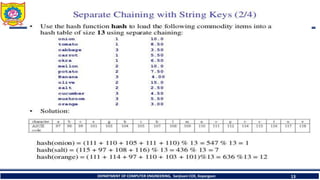


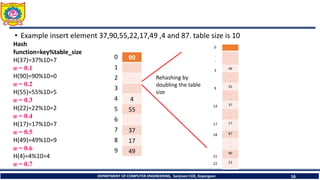

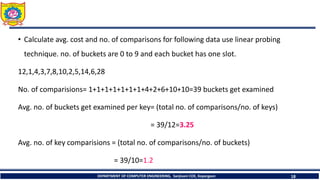
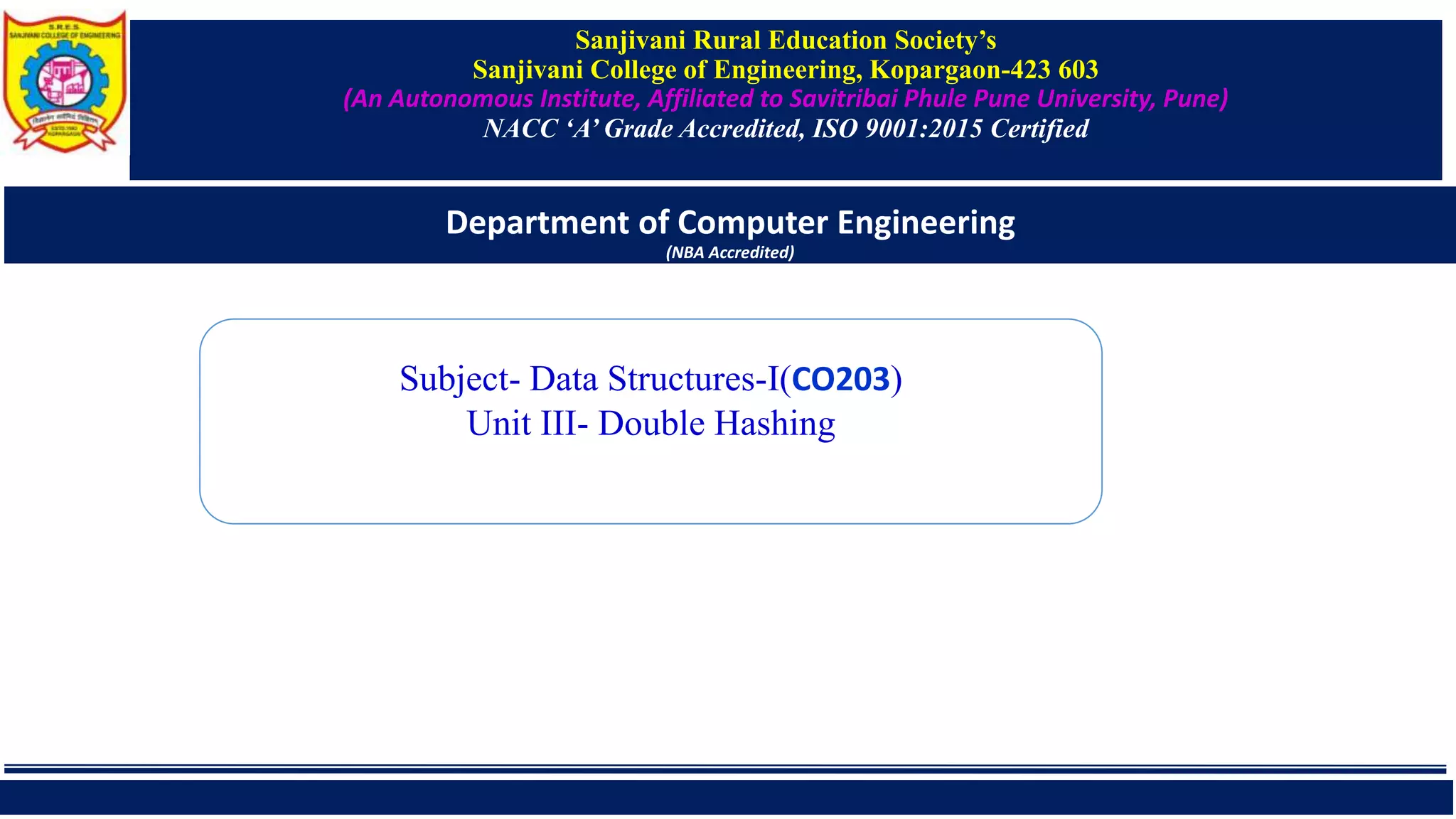
![Avg. cost can be computed by calculating successful(Sn) and unsuccessful
search(Un)
Sn = ½( 1+ [1/(1- α )])
= 1/2 ( 1+[1/ (1- 1.2)])
= -2
Un =1/2(1+[1/(1-α)2])
= ½ (1+(1/0.04))
=13
Total cost= Sn + Un
= -2+13=11
DEPARTMENT OF COMPUTER ENGINEERING, Sanjivani COE, Kopargaon 19](https://image.slidesharecdn.com/doublehashing-230705084211-d6101b38/85/Double-Hashing-pptx-19-320.jpg)