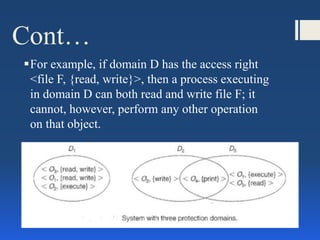
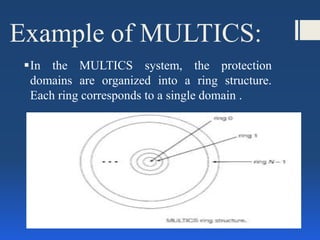
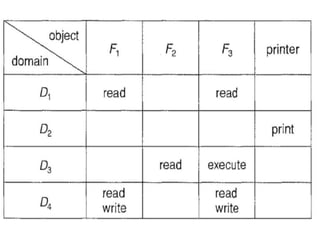
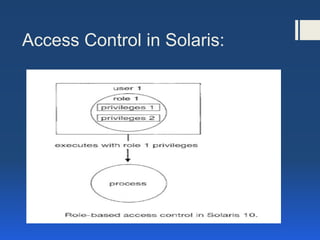
This document discusses computer system protection. It outlines goals of protection like preventing unauthorized access. Principles like least privilege aim to minimize damage from compromised access. Protection domains define which objects and operations processes can access. Access matrices represent these access rights. Examples of early capability-based and language-based protection systems are described.