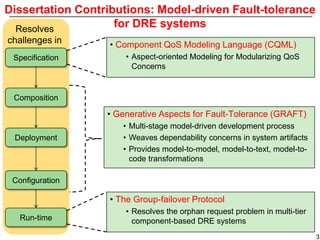
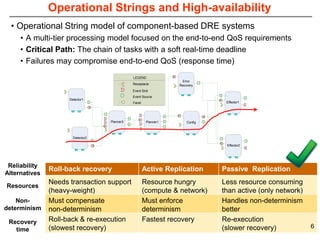
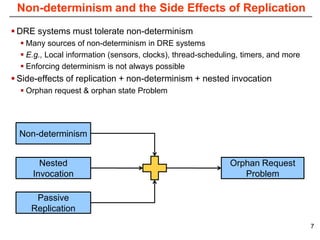
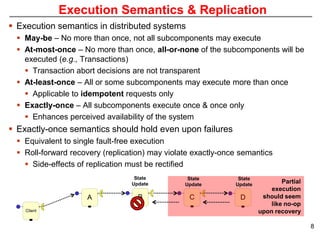
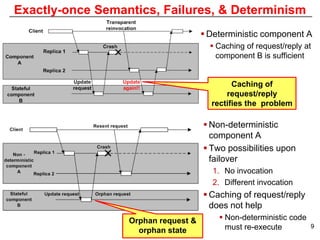
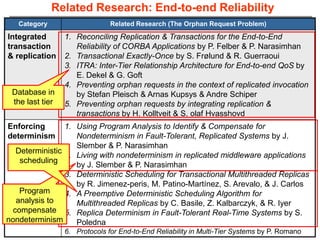
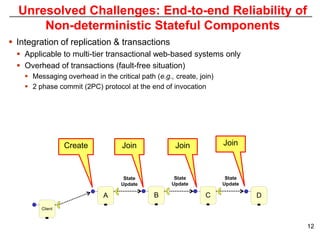
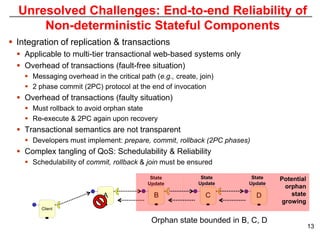
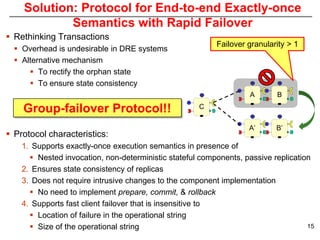
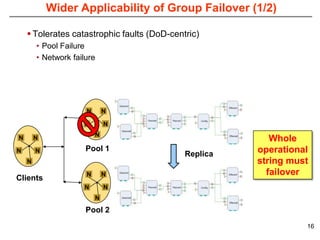
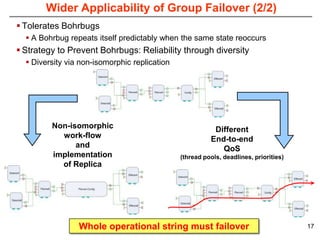
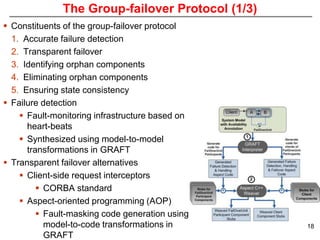
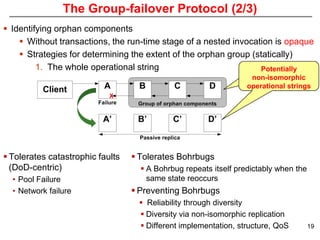
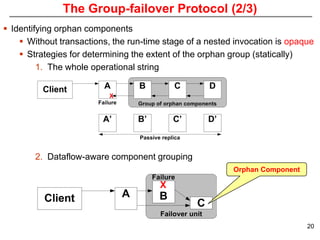
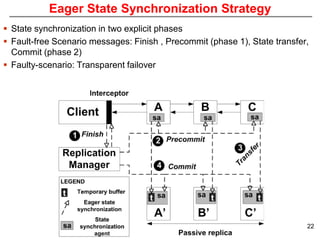
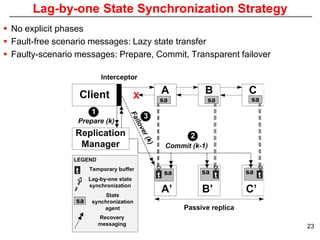
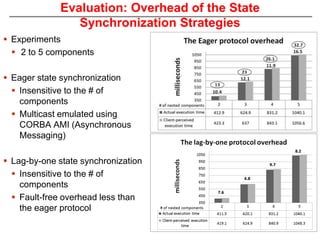
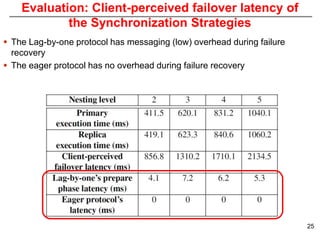
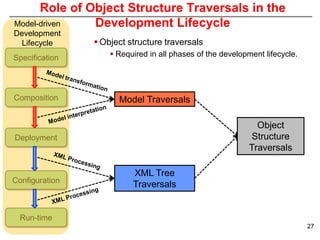
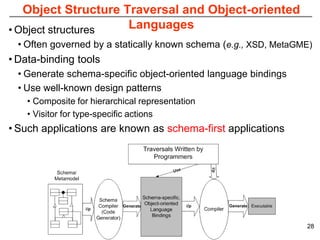
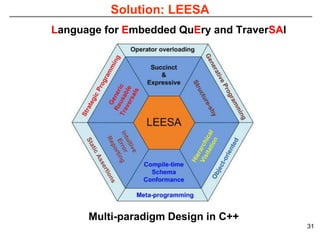
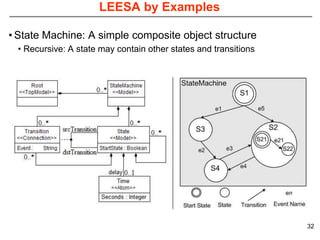
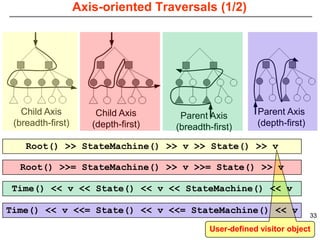
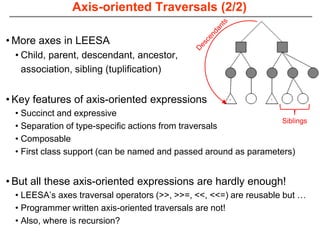
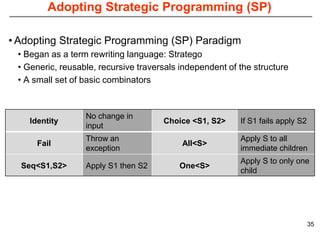
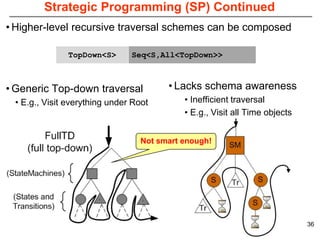
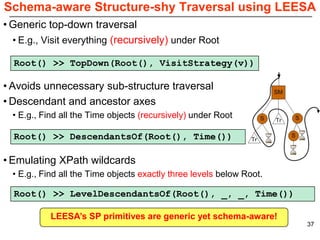
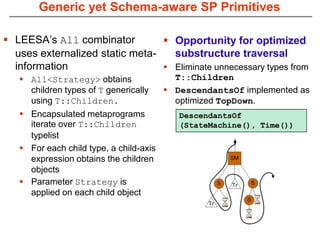
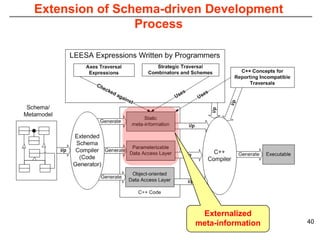
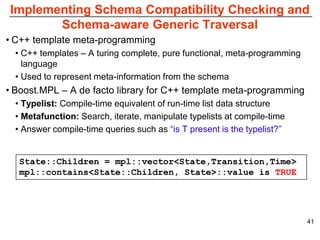
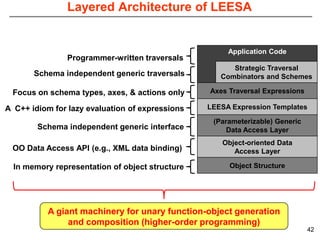
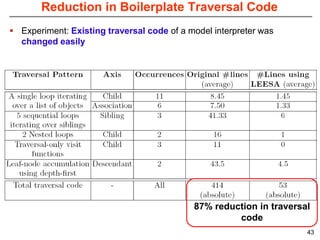
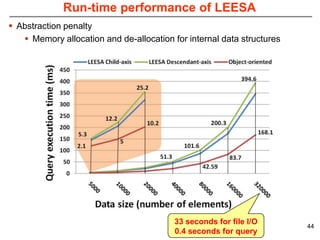
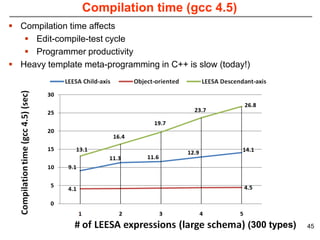
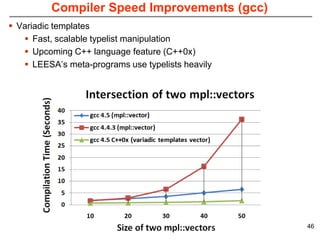
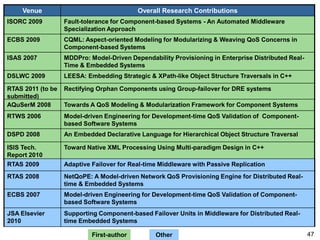
This document describes Sumant Tambe's PhD dissertation defense on end-to-end reliability of non-deterministic stateful components. The dissertation addresses challenges in specifying, composing, deploying, and configuring fault tolerance for distributed real-time embedded systems. It presents the Group-failover Protocol to solve the orphan request problem and ensure exactly-once execution semantics without transactions. It also introduces typed traversals and the LEESA solution to compose components while enforcing type safety. The dissertation contributes model-driven techniques for modularizing quality of service concerns and generating fault tolerance aspects to weave dependability into system artifacts.