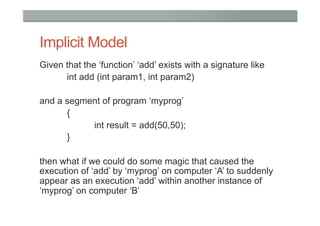
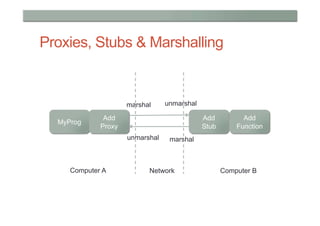
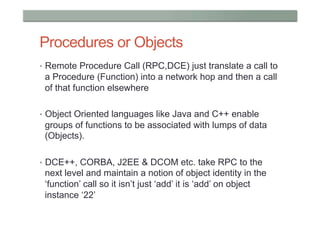
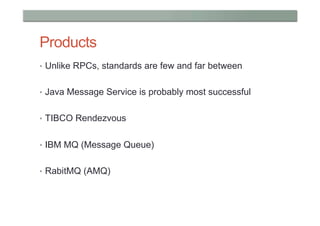
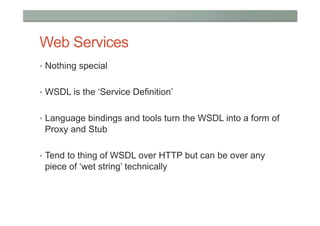
This document provides a high-level overview of key concepts in distributed systems, including programming models, remote procedure calls, messaging, distributed data, peer-to-peer networks, distributed hash tables, cloud computing, and security. It discusses implicit and explicit programming models, synchronous and asynchronous communication, and distributed computing frameworks like MapReduce.