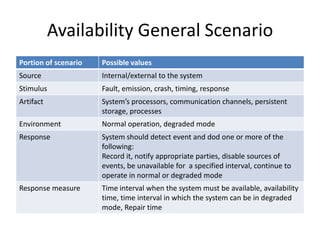
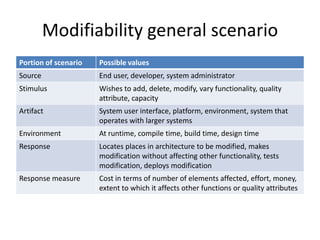
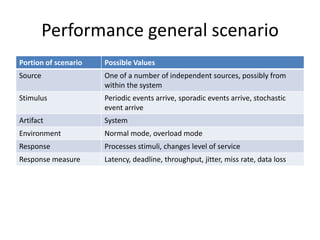
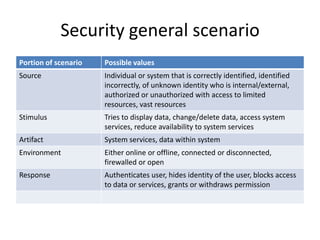
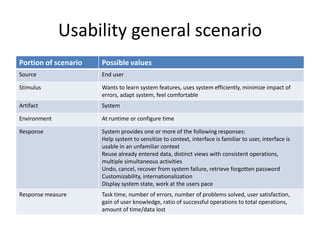
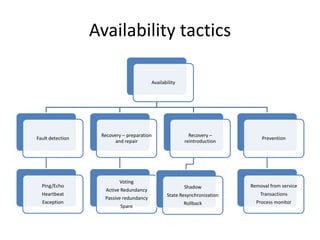
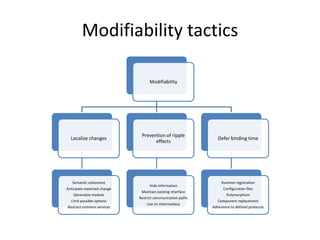
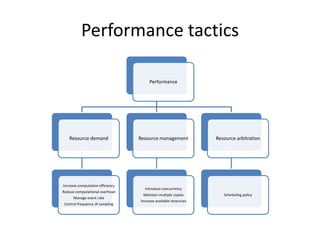
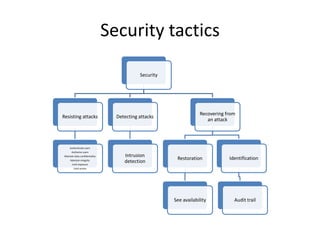
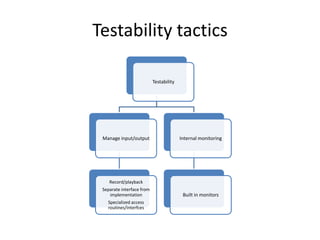
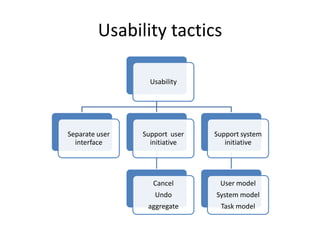
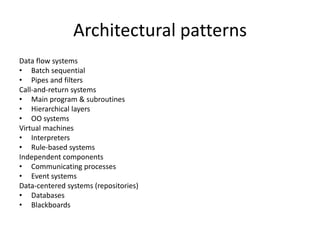
This document discusses quality attributes and tactics for software architecture. It describes key quality attributes like availability, modifiability, performance, security, testability and usability. For each attribute, it provides general scenarios and possible values. It also outlines tactics that can be used to achieve each quality attribute at the architectural level. Finally, it briefly introduces the Attribute-Driven Design method for designing software architectures to meet both functional and quality requirements.