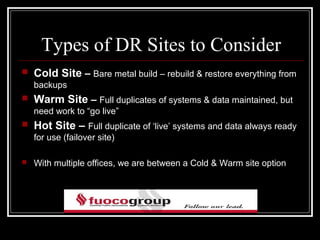
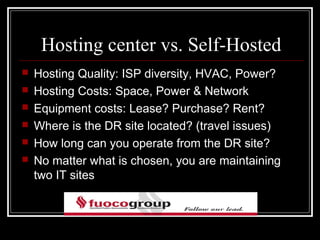
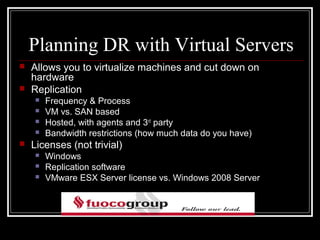
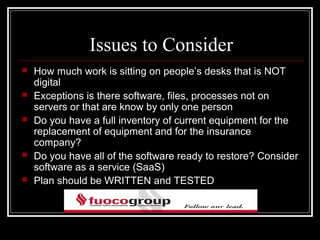
This document discusses disaster recovery and risk management for an accounting firm with offices in New York, Florida, and Long Island. It defines key terms like RTO, RPO, and BIA. It also covers considerations for disaster recovery planning like acceptable downtime, data loss tolerance, and types of disaster sites. The document discusses virtualization, document retention policies, privacy issues, and IT security risks.