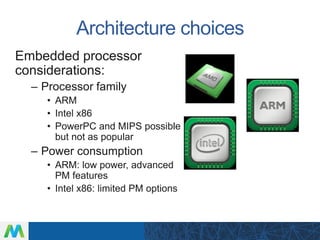
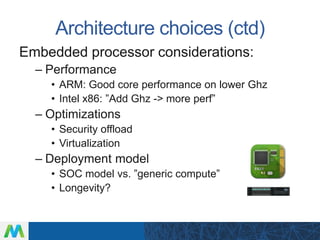
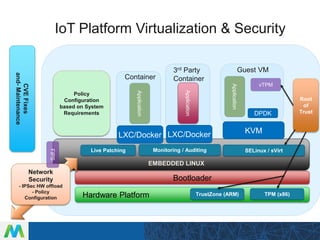
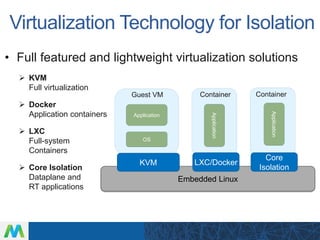
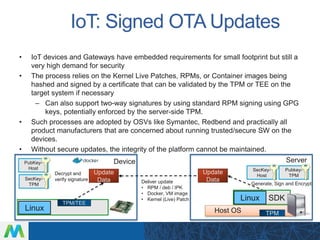
LinuxCon Tokyo 2016 focused on developing secure IoT gateways. The presentation discussed gateway architecture choices like ARM and x86 processors. Connectivity options for sensors like Bluetooth and WiFi were also covered. Security is a major concern, and the talk evaluated both reactive measures like intrusion detection and proactive approaches like mandatory access control. Maintaining gateways over long product lifecycles requires techniques like live kernel patching and signed over-the-air updates to securely deploy upgrades. Embedded Linux provides a robust software platform for building reliable and secure IoT gateways.