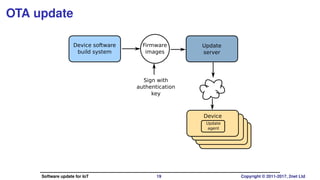
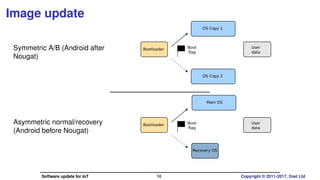
The document discusses software update strategies for Internet of Things (IoT) devices, highlighting the importance of secure, robust, and atomic update processes. It covers various update mechanisms, including over-the-air updates and atomic differential updates, along with challenges and examples of update systems. The conclusion emphasizes the need for a stateless root filesystem and the evolving landscape of IoT software management.











![Examples of containerised updaters
• resin.io: https://resin.io
• Applications distributed in Docker containers
• Managed on device by Resin Container Engine
• Integrates with OTA update server (not open source)
• Licenses: Client: Apache2; Server: proprietary
• Snappy: https://snapcraft.io
• Containers are called snaps
• A snap contains a squashfs file system, mounted on /snap/[app]
• License: GPLv3
Software update for IoT 18 Copyright © 2011-2017, 2net Ltd](https://image.slidesharecdn.com/24iotviichrissimmonds-slides-170312102910/85/Software-update-for-IoT-Embedded-World-2017-18-320.jpg)