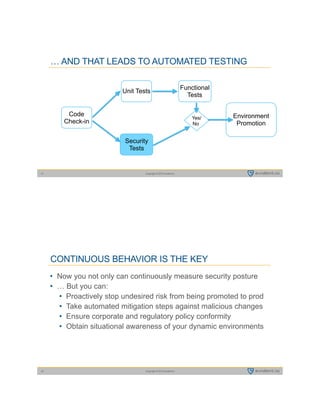
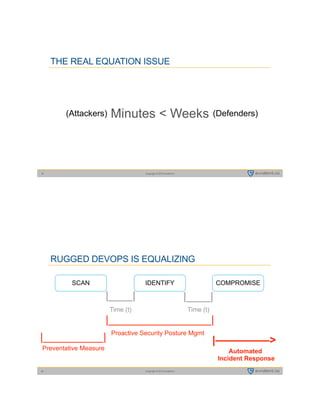
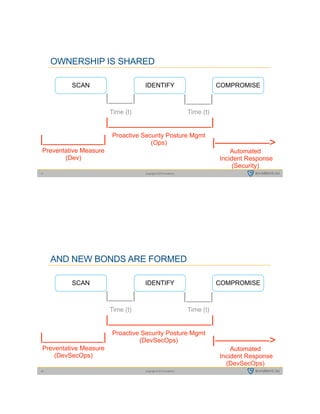
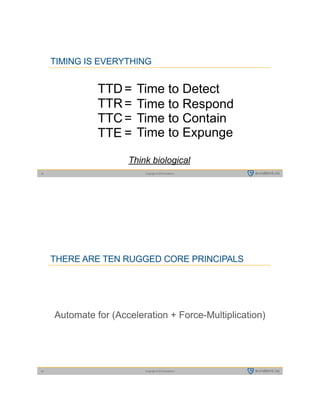
This document summarizes a presentation by Tim Prendergast of Evident.io on developing a rugged DevOps approach to cloud security. It discusses how attackers have advantages over defenders due to their ability to automate attacks. It argues that in order to match attackers, security practices need to be automated and integrated into DevOps workflows through a DevSecOps model. This involves embracing principles like treating security as code, testing security at all stages of development, and ensuring security practices are collaborative rather than siloed. The goal is to minimize the time window attackers have to exploit vulnerabilities before they are detected and remediated.







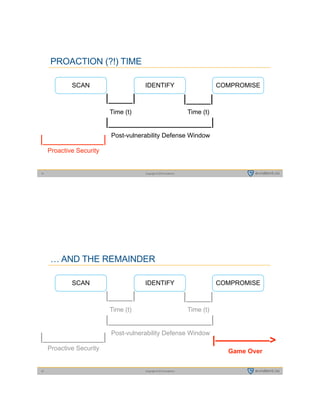



![Copyright © 2015 evident.io29
SECURITY CLARITY IS NECESSITY
PCI DSS Req 3.5.1: Restrict access to cryptographic keys to the fewest
number of custodians necessary.
Translation: We never want more than 2 custodians with access to keys used
for encrypting sensitive data. If there are more than two, we need
to know (organization-wide) to prevent abuse or malicious access.
Copyright © 2015 evident.io30
THIS LEADS TO SECURITY-AS-CODE
{
"Sid": “PCI DSS 3.5.1 - Control Key Access”,
"Effect": "Allow",
"Principal": {"AWS": [
"arn:aws:iam::0123456789:user/Custodian1",
"arn:aws:iam::0123456789:role/Custodian2"
]},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
}
configure do |c|
c.deep_inspection = [:alias_name, :alias_arn,
:target_key_id, :description, :creation_date,
:key_state, :deletion_date, :key_policies]
c.unique_identifier = [:alias_name]
end
def perform(aws)
key_aliases = aws.kms.list_aliases.aliases
key_aliases.each do |key_alias|
key_policies = aws.kms.list_key_policies({key_id:key_alias})
@custodians = key_policies.principal
custodians.each do |users|
{HERE'S THE FUN STUFF}](https://image.slidesharecdn.com/dt33-160916173140/85/Developing-a-Rugged-DevOps-Approach-to-Cloud-Security-17-320.jpg)