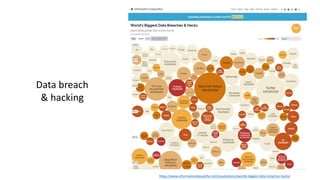
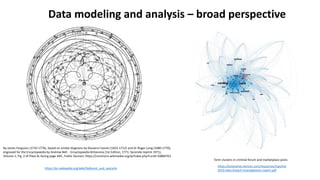
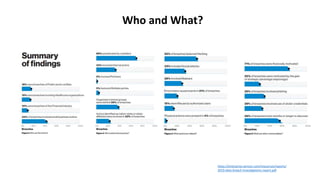
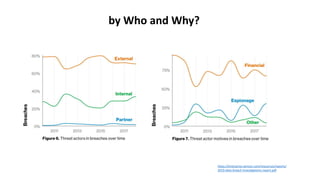
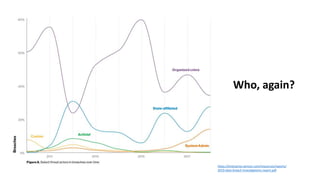
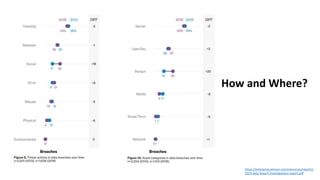
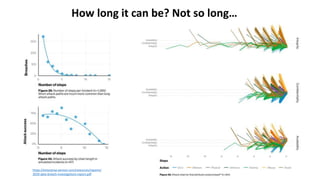
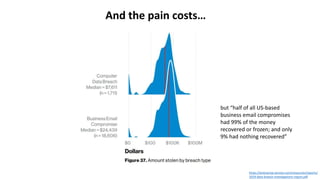
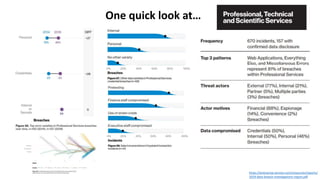
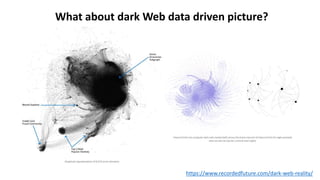
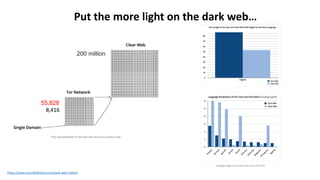
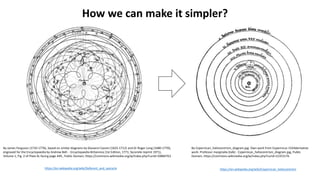
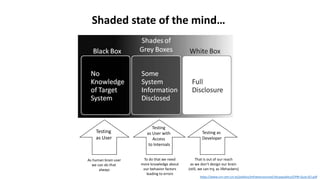
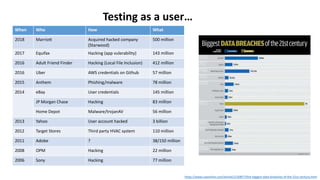
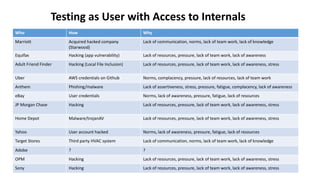
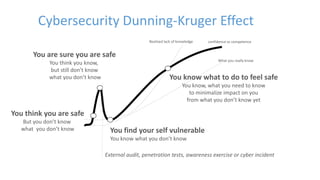
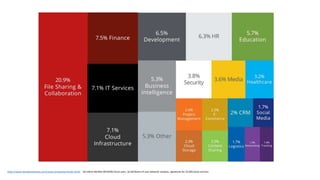
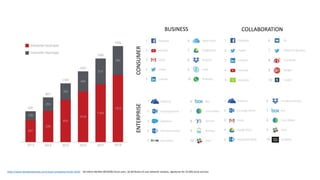
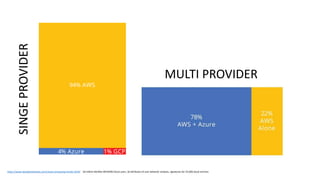
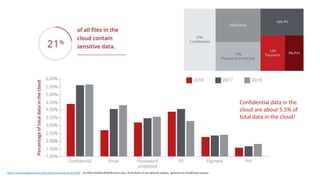
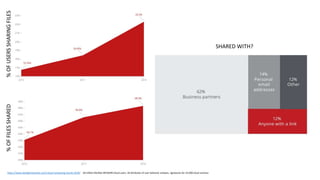
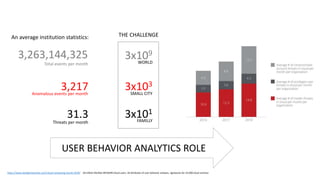
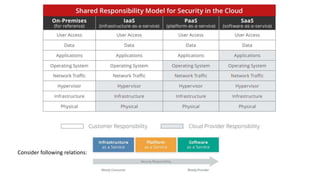
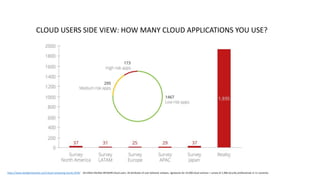
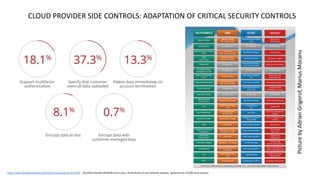
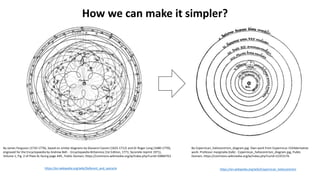
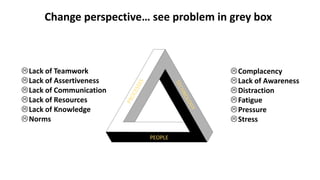
The document discusses various factors related to cybersecurity from multiple perspectives. It begins by looking at common human errors that contribute to cyber incidents, such as lack of communication, knowledge, teamwork, resources, and assertiveness. It then examines specific cybersecurity incidents and attributes the causes to human factors. The document advocates changing perspective to see problems as resulting from human rather than technical factors. It also discusses challenges around cloud computing and the need to consider both user and provider security controls and perspectives. Finally, it analyzes the "dirty dozen" human error types in more depth and provides countermeasures to address each type of error.