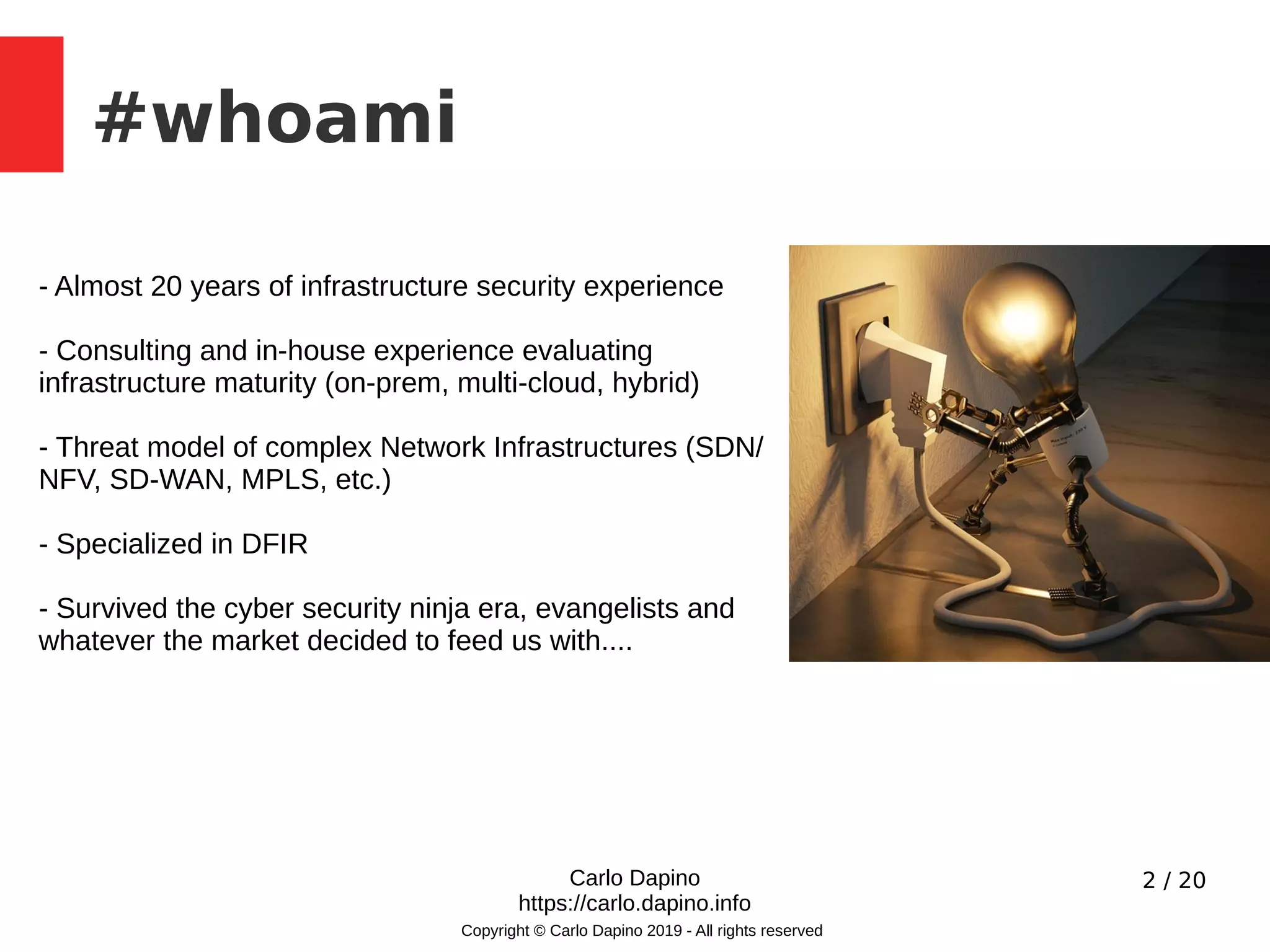
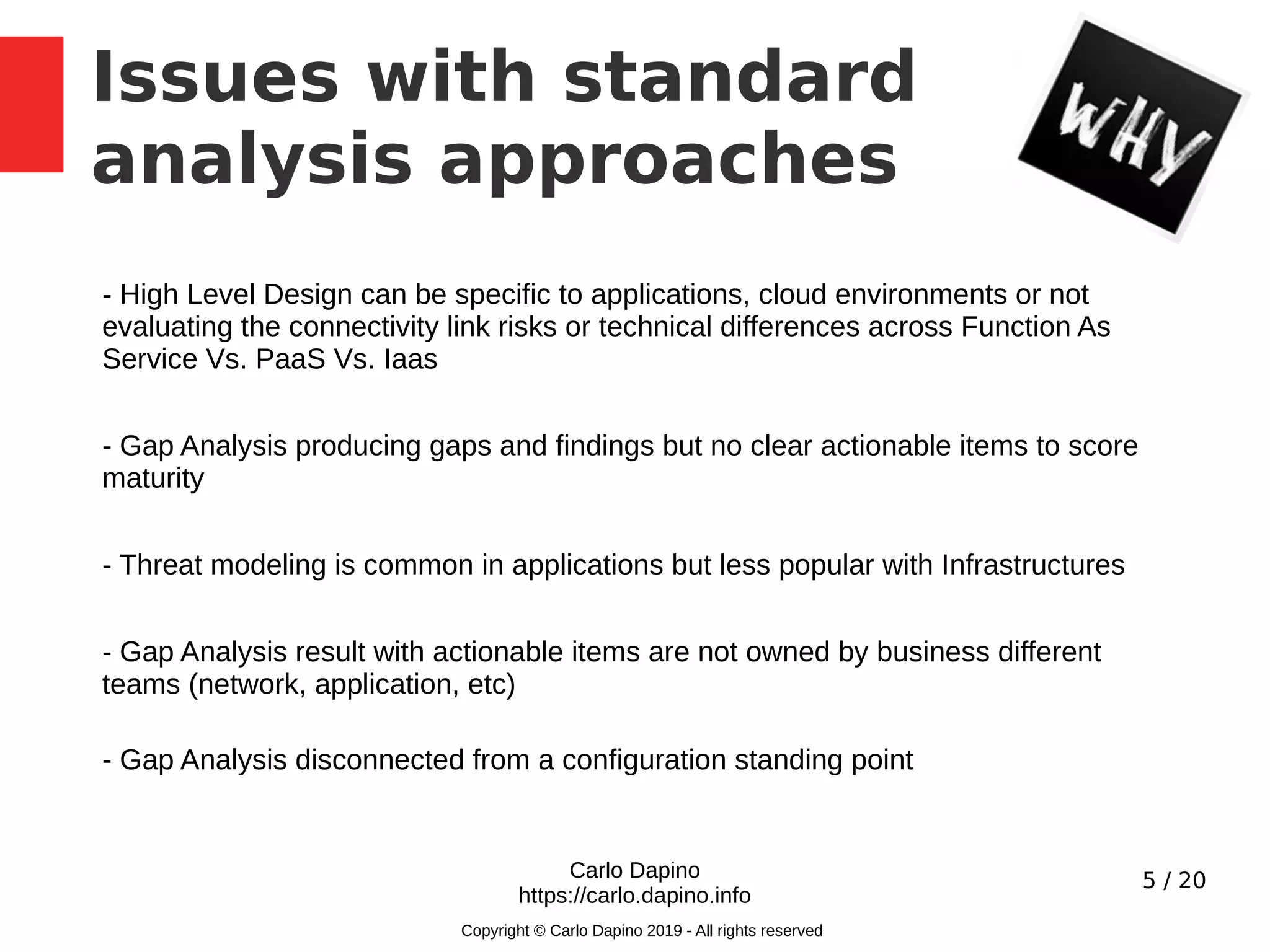
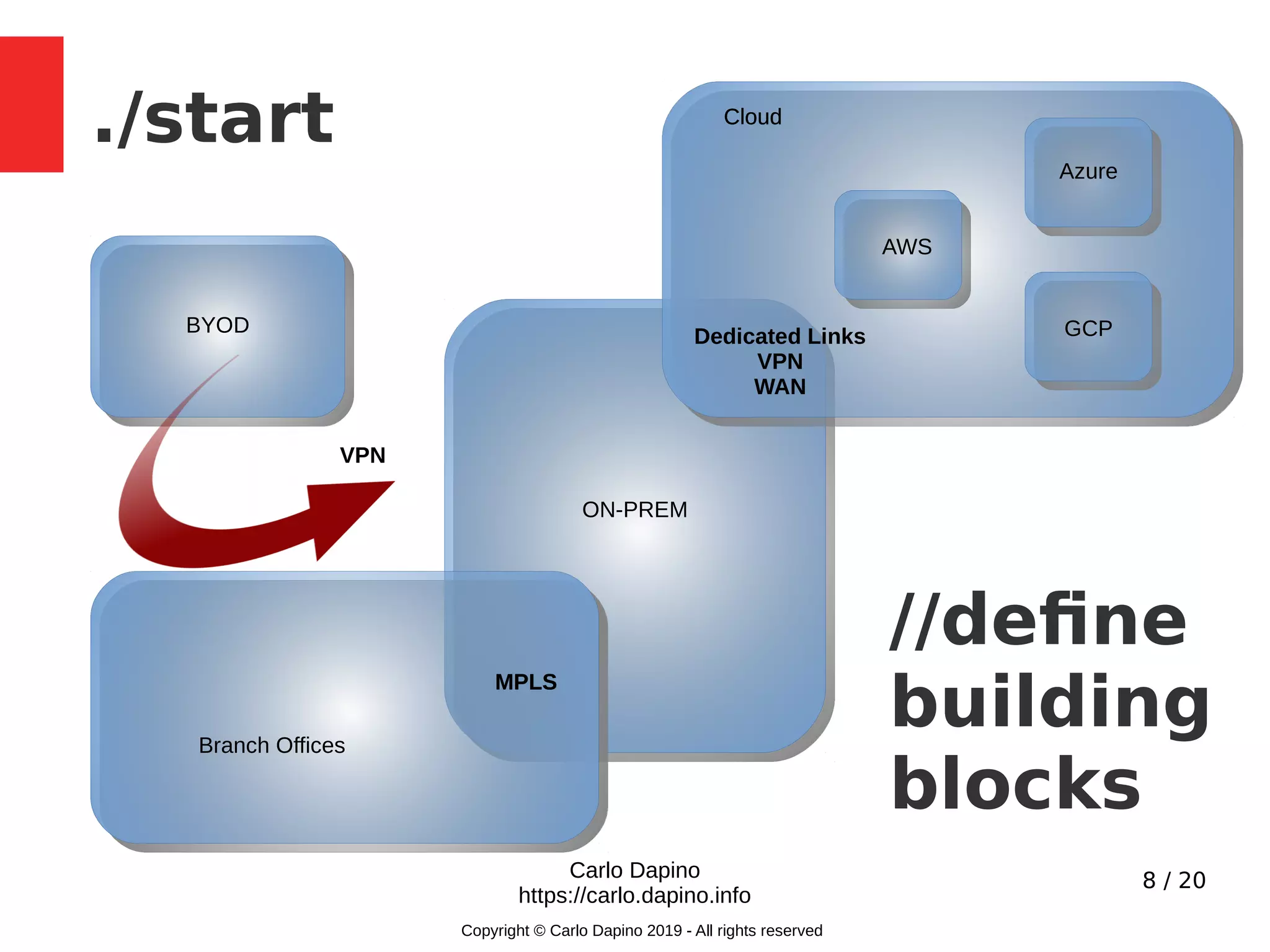
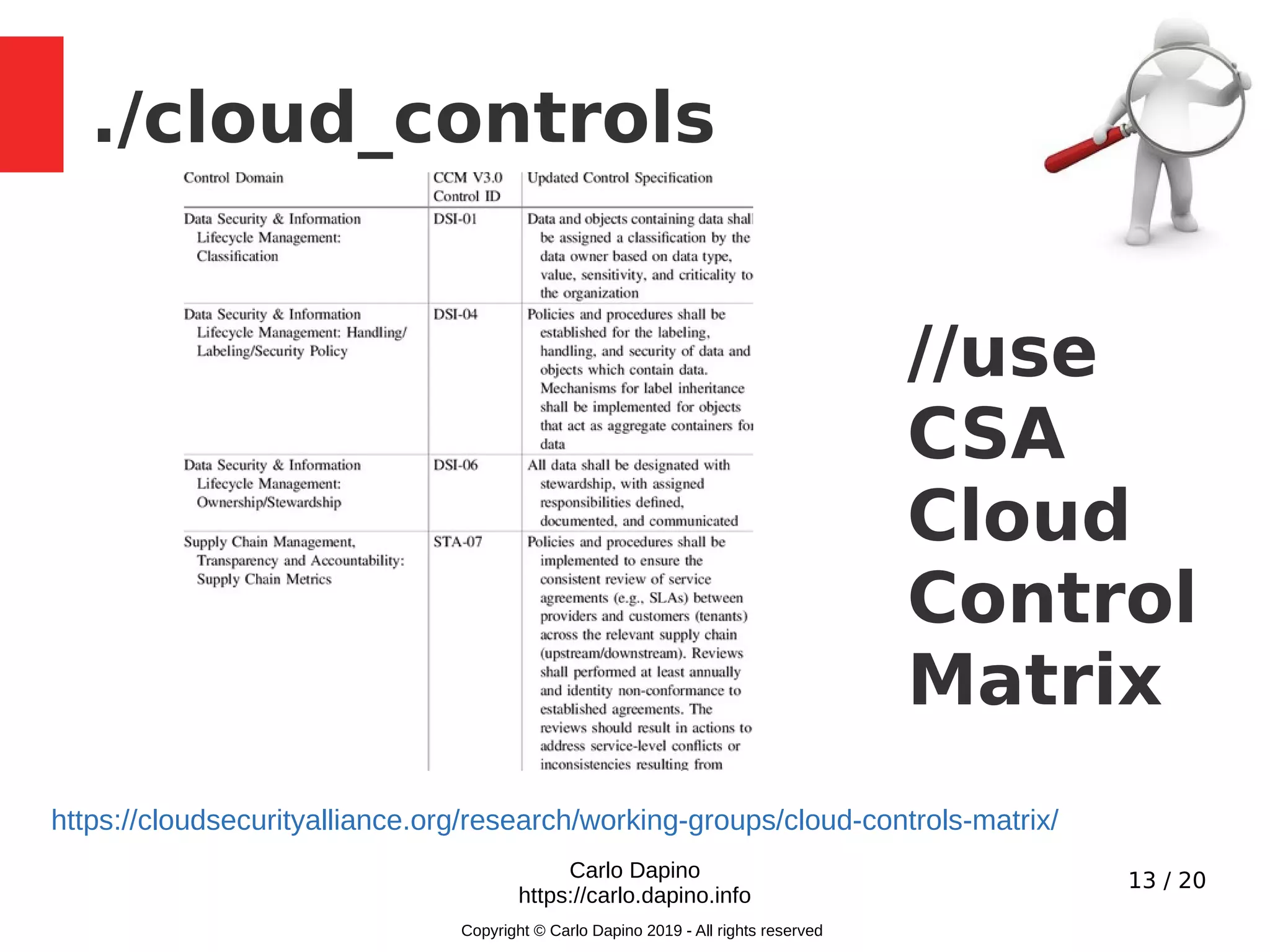
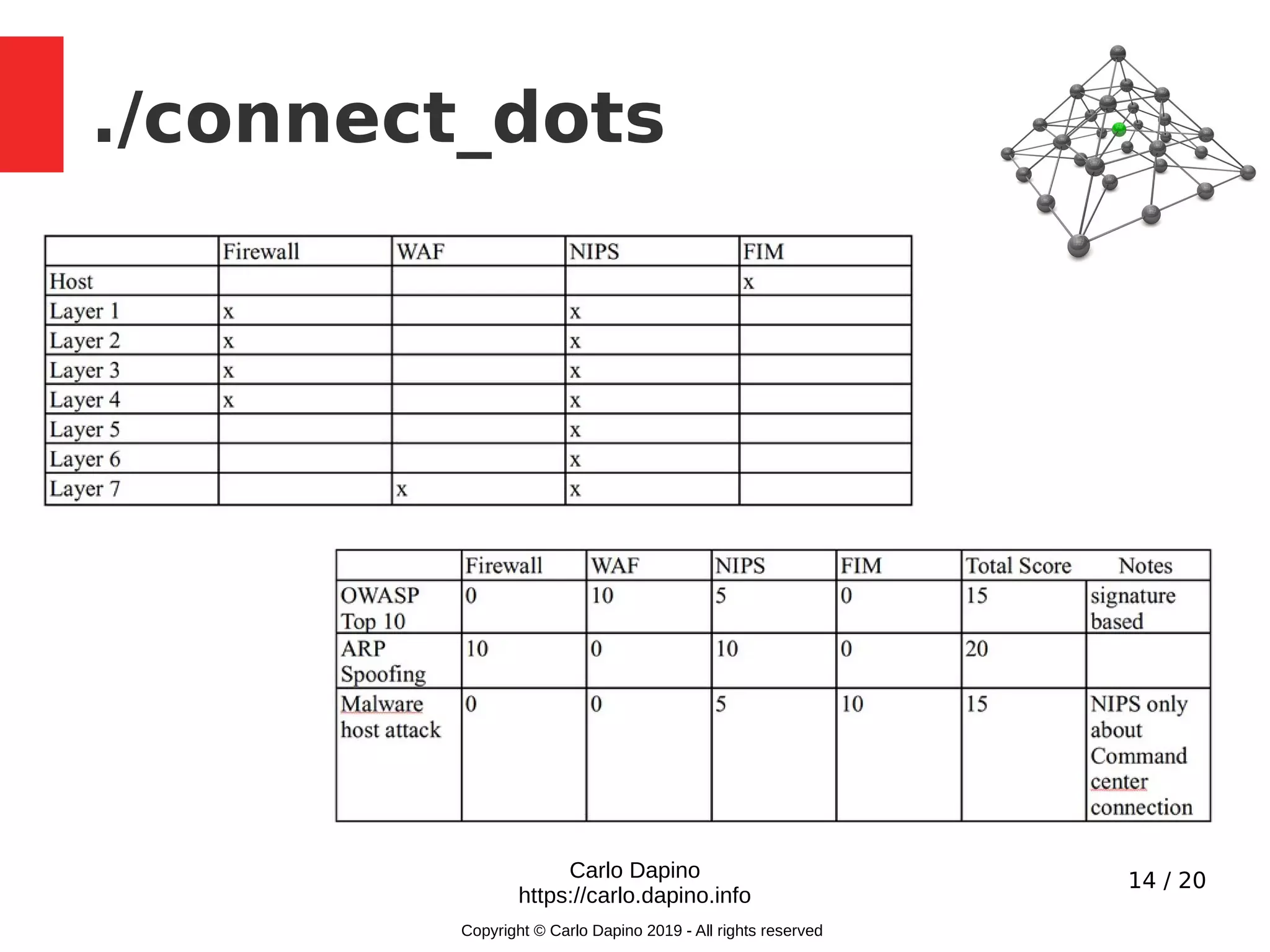
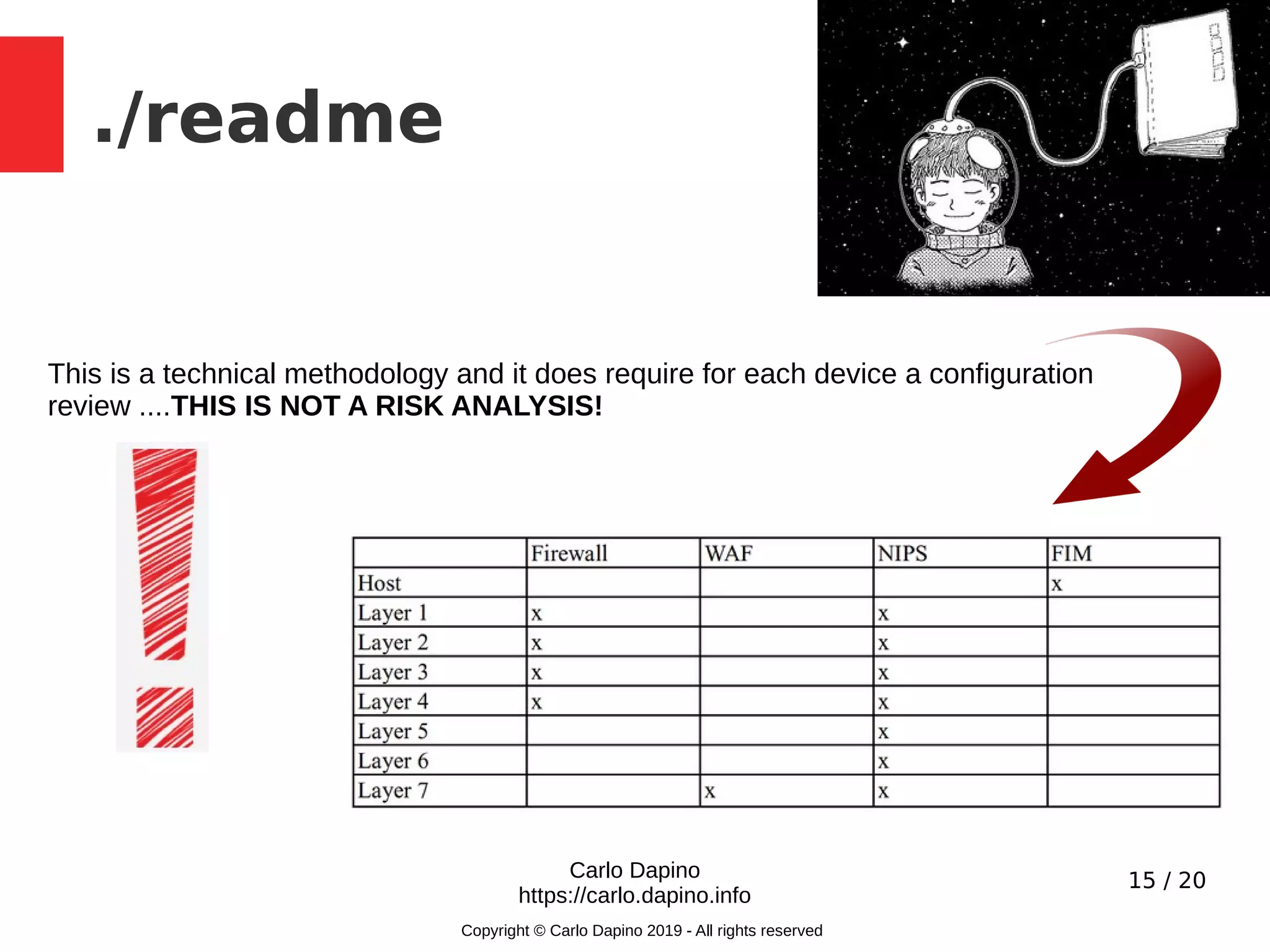
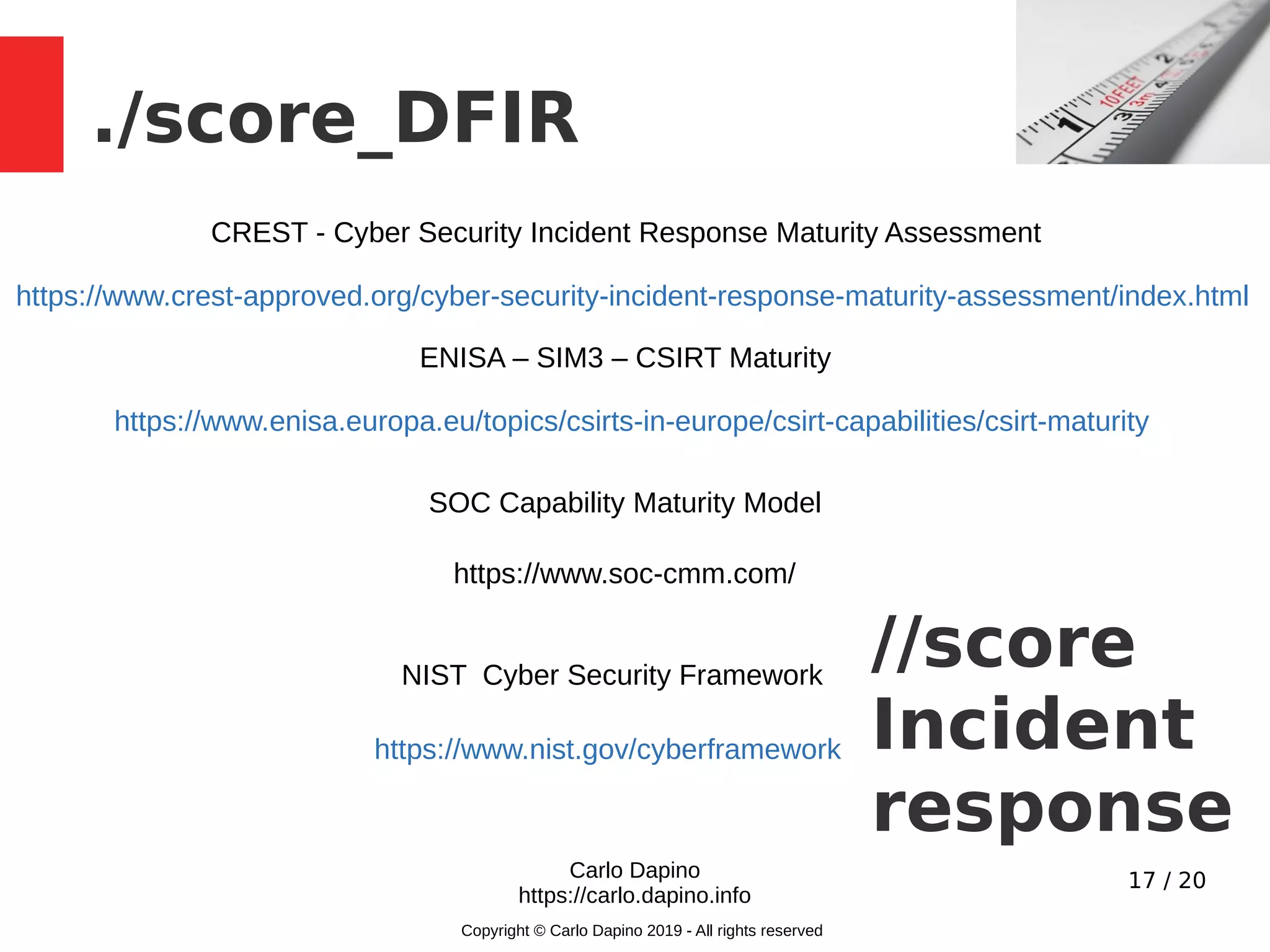
The document presents a methodology for conducting infrastructure security gap analysis tailored for CISOs and security professionals. It highlights challenges with existing analysis approaches and aims to provide actionable insights for improving security posture through threat modeling and incident response evaluation. The author emphasizes the importance of analyzing connectivity, identity management, and organizational maturity in cybersecurity practices.
![1 / 20
[How-To] Infrastructure
Security Gap Analysis
Carlo Dapino
https://carlo.dapino.info
Copyright © Carlo Dapino 2019 - All rights reserved](https://image.slidesharecdn.com/howtosecurityinfragapsanalysisbycarlodapino-200407171434/75/How-to-perform-an-Infrastructure-Security-Gap-Analysis-1-2048.jpg)