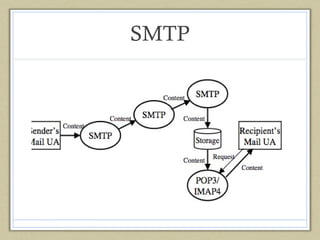
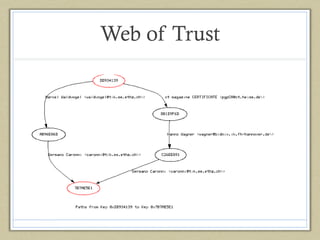
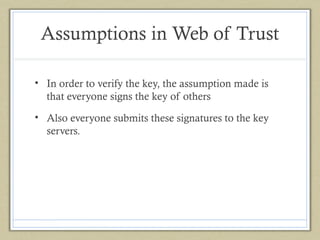
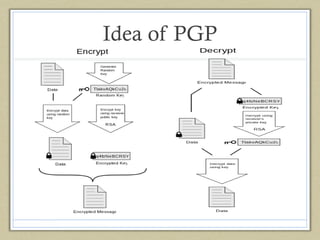
This document summarizes Bitmessage, an anonymous and encrypted messaging protocol. Some key points:
- Bitmessage is based on the Bitcoin protocol and uses a "Everyone Gets Everything" model where all active users receive and try to decrypt messages.
- It aims to anonymize both message content and metadata like sender/receiver addresses.
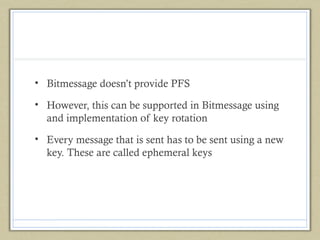
- Issues include a lack of perfect forward secrecy and questions around scalability with high message volumes.
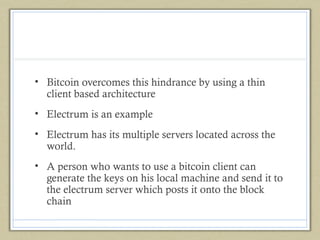
- The document proposes a thin client architecture like Bitcoin's Electrum to help address scalability by avoiding downloading the full blockchain locally.