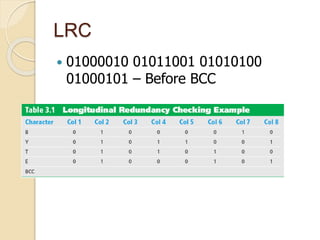
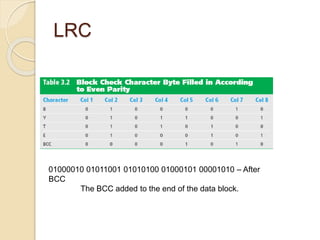
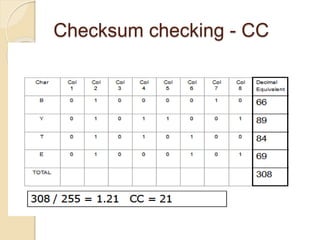
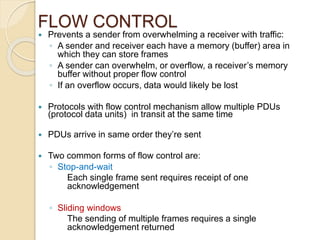
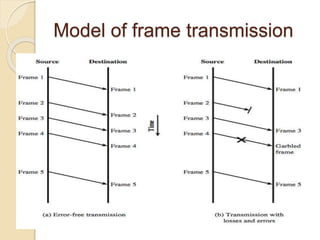
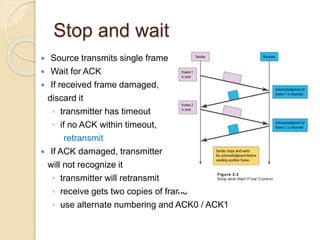
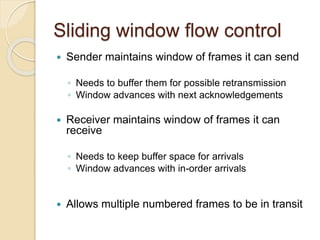
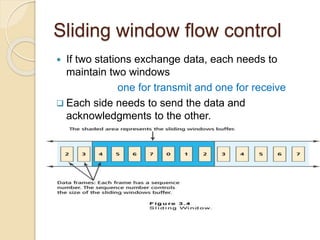
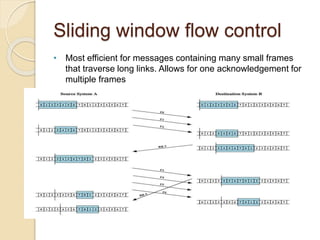
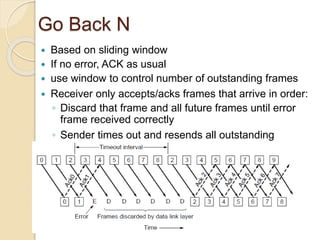
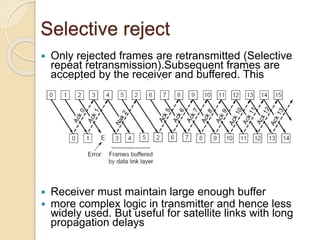
This document discusses error detection and correction techniques used in data communication networks. It describes common types of transmission errors like single bit errors and burst errors. It then explains different error detection methods including parity checking, longitudinal redundancy checking (LRC), and checksum checking. It also covers error correction techniques like Go-Back-N and Selective Repeat that allow retransmission of only corrupted frames. Flow control mechanisms like stop-and-wait and sliding window protocols are also summarized.