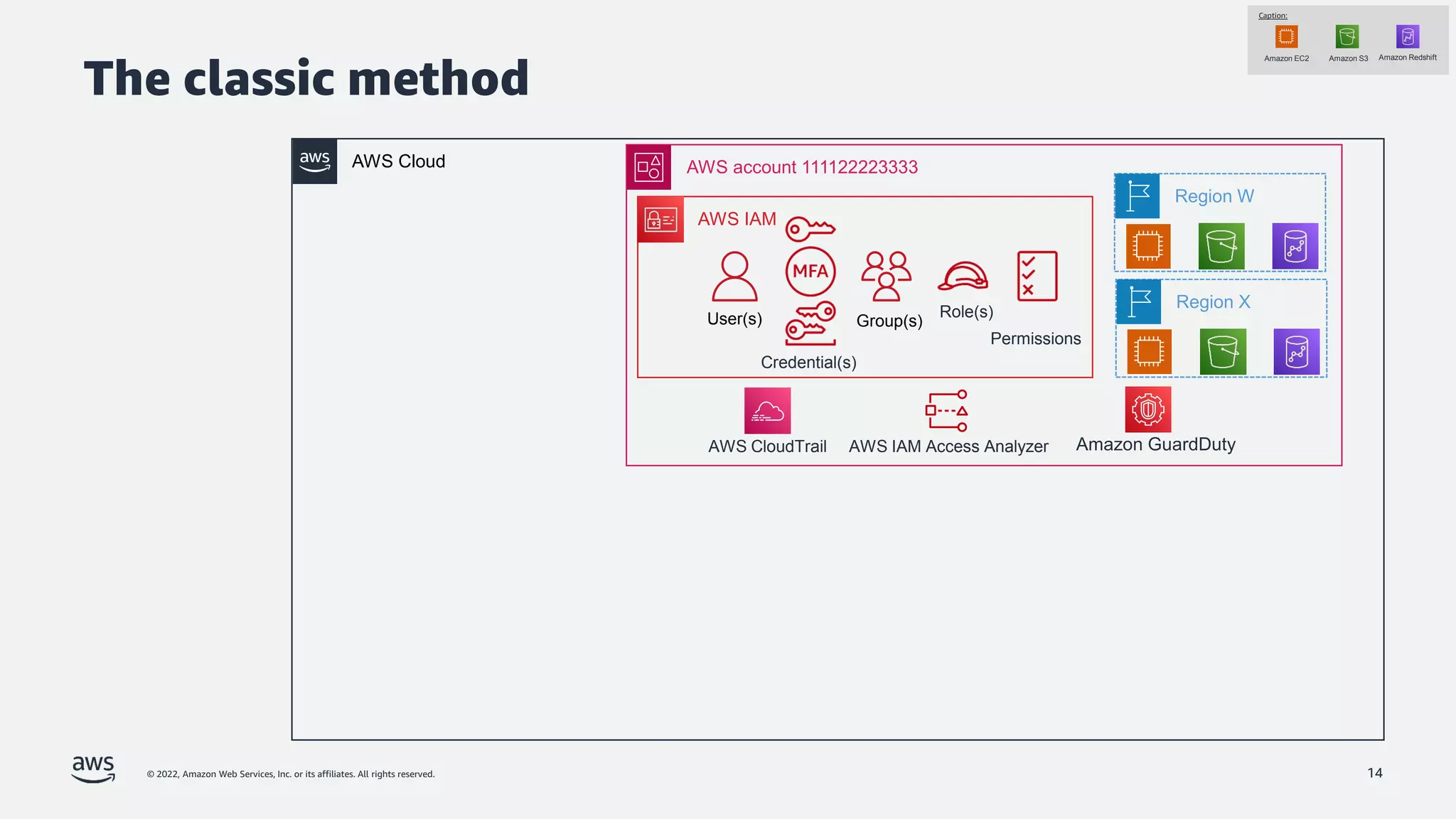
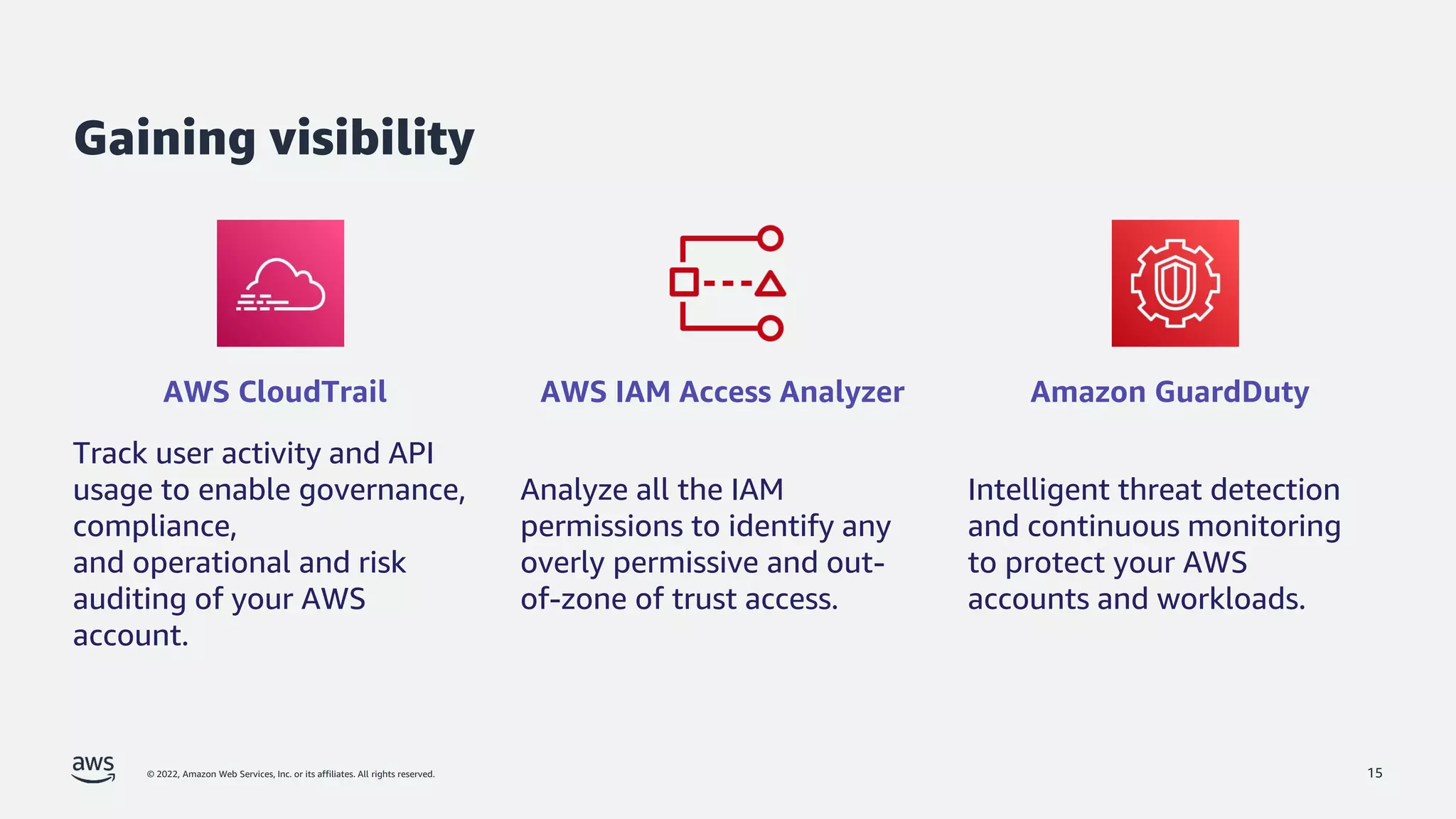
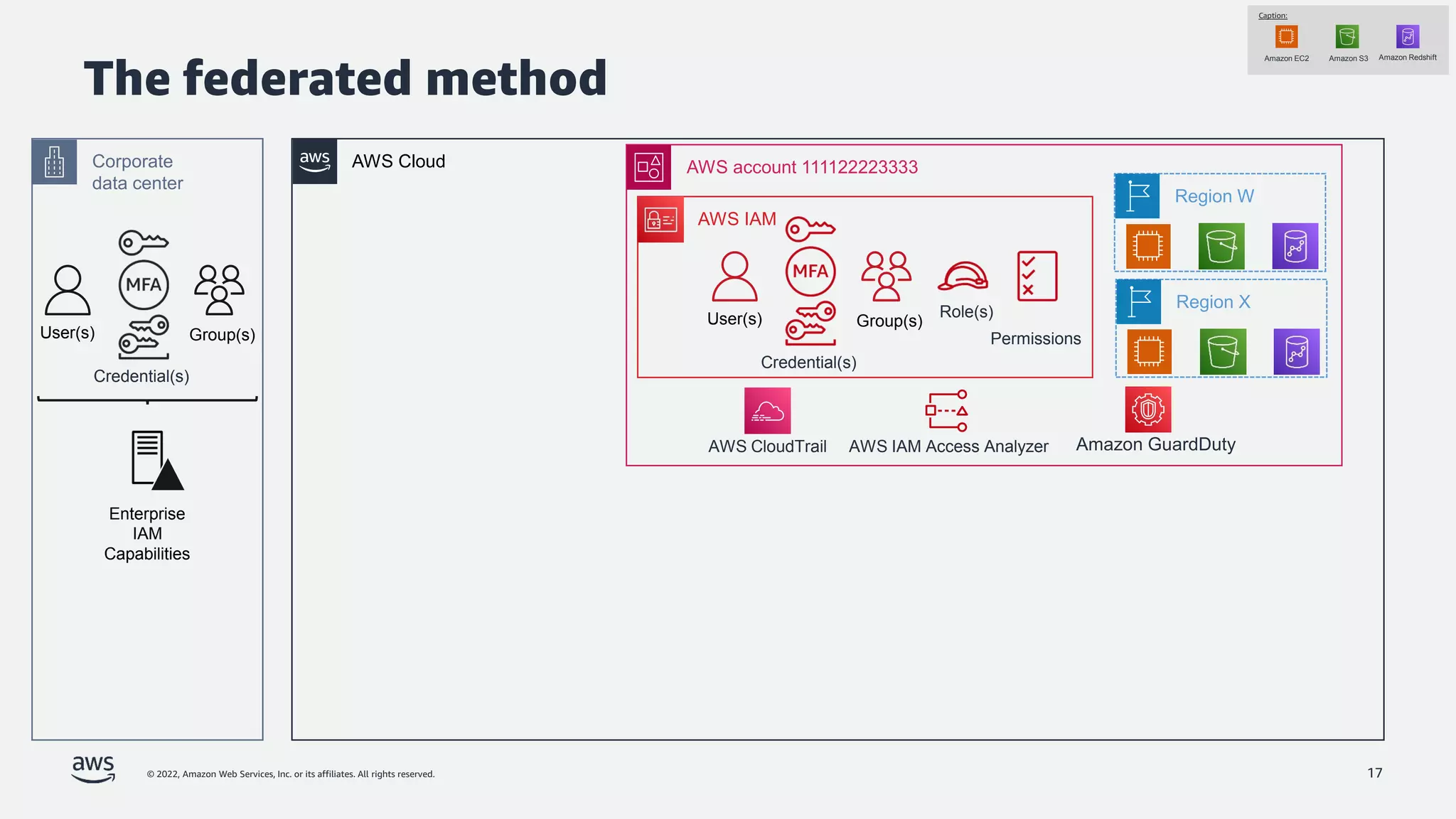
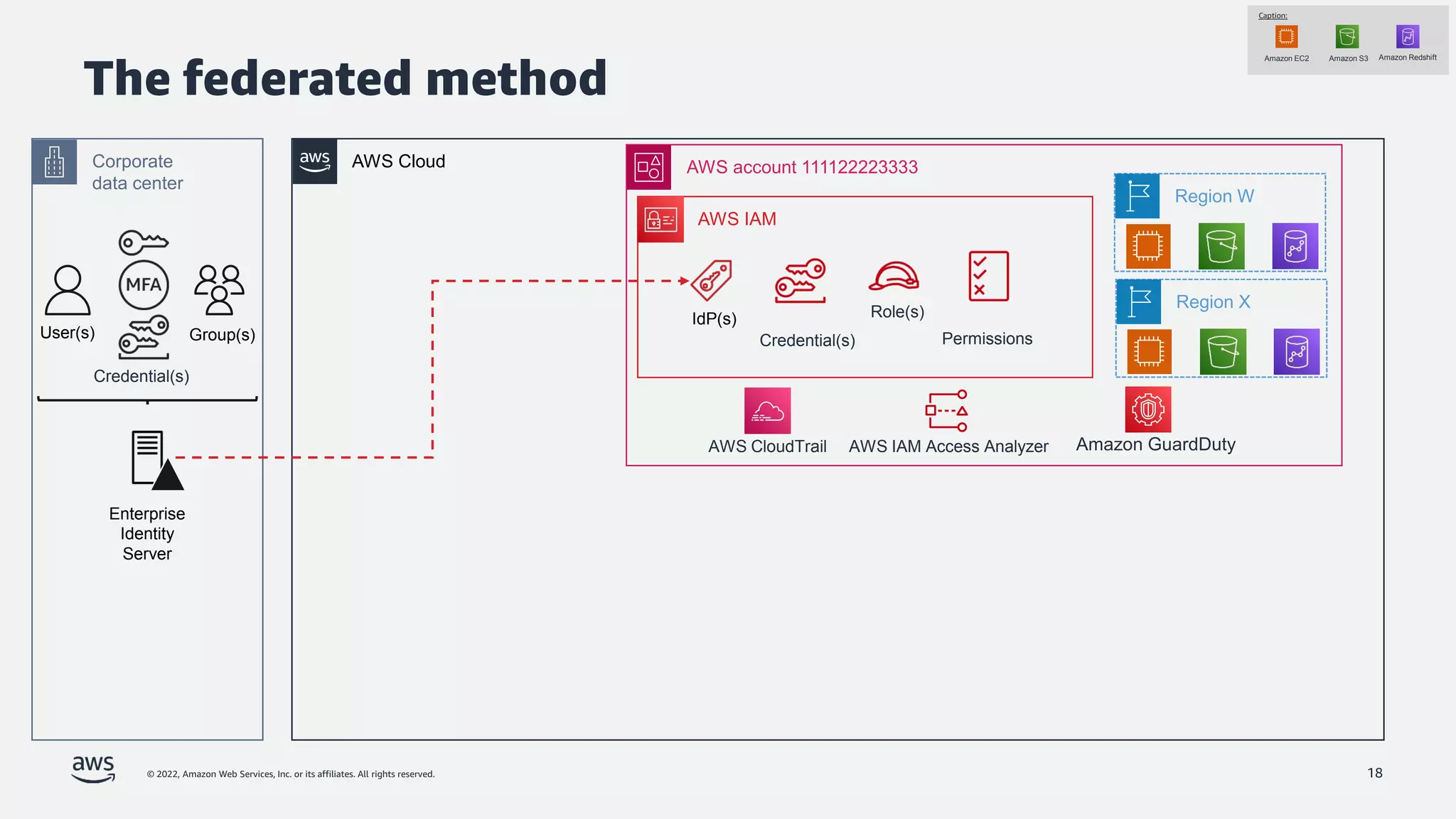
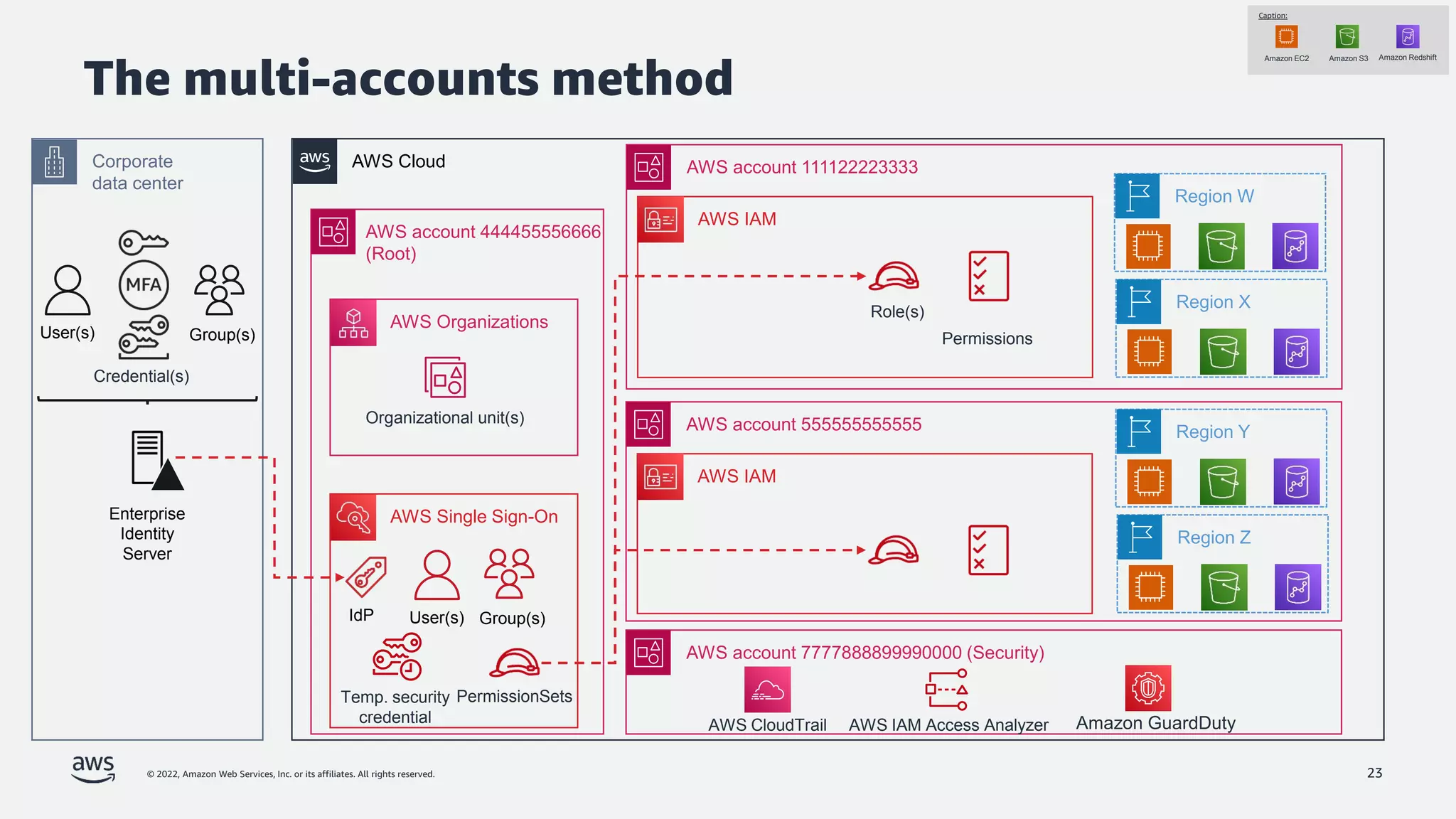
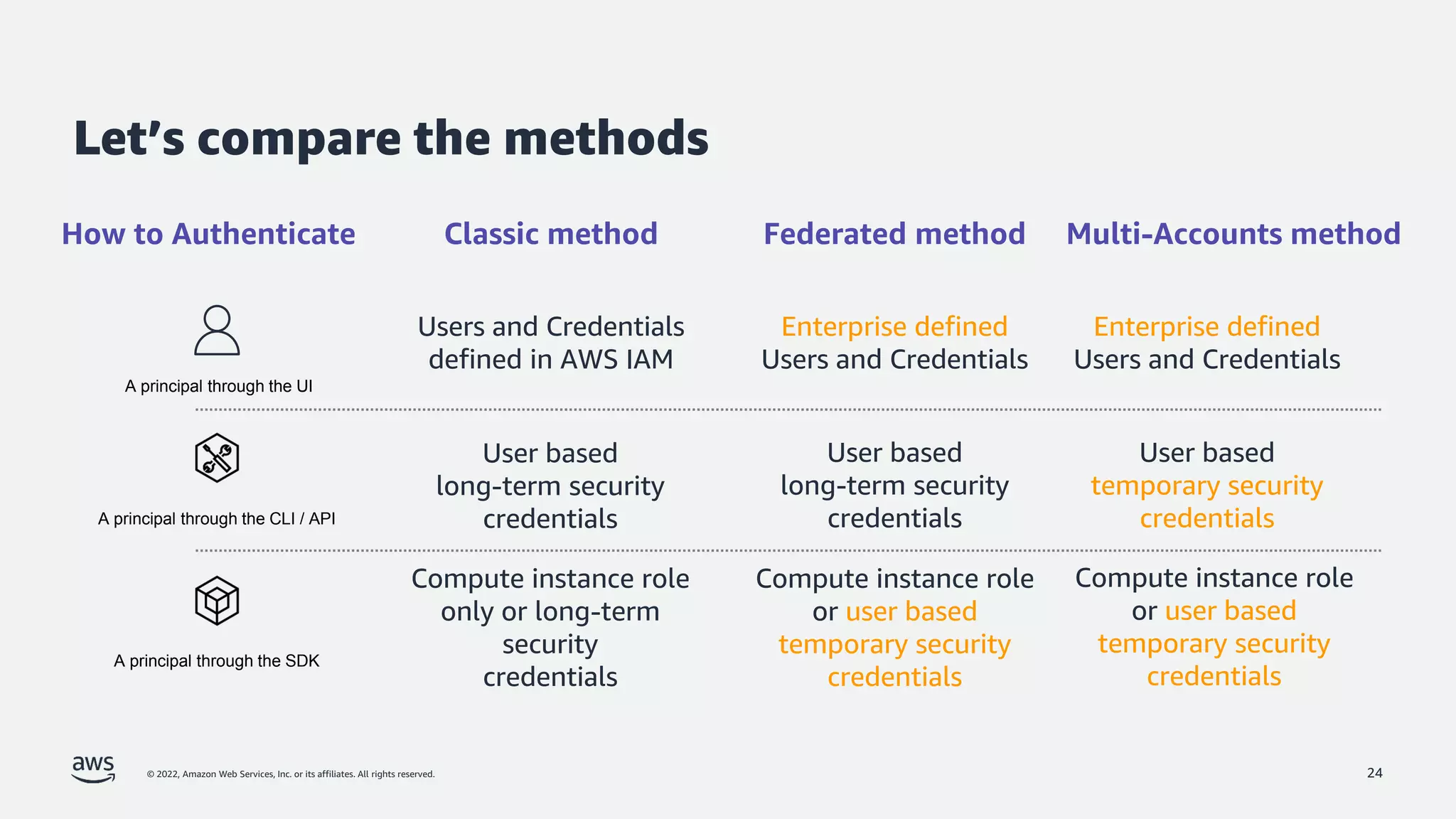
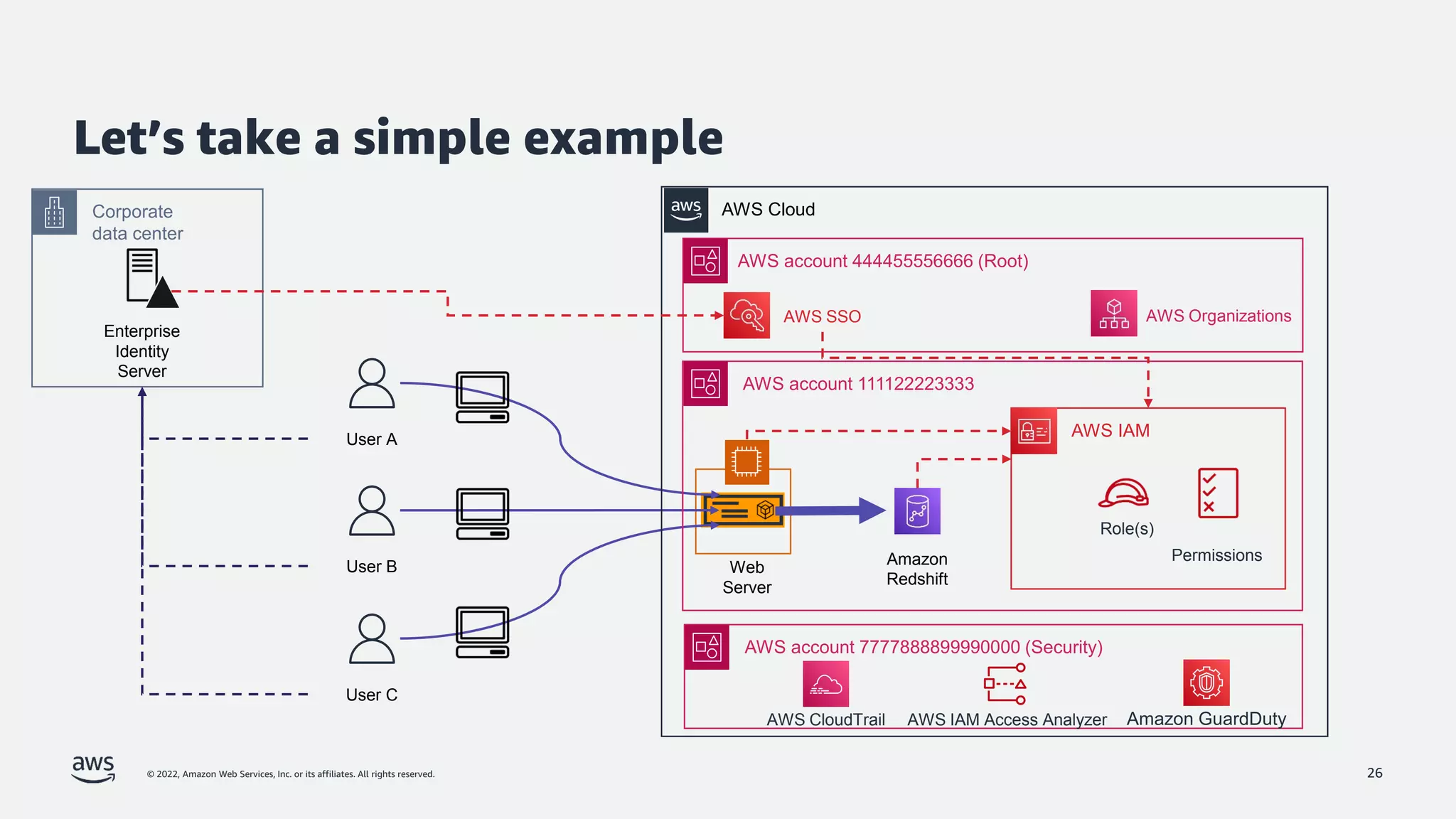
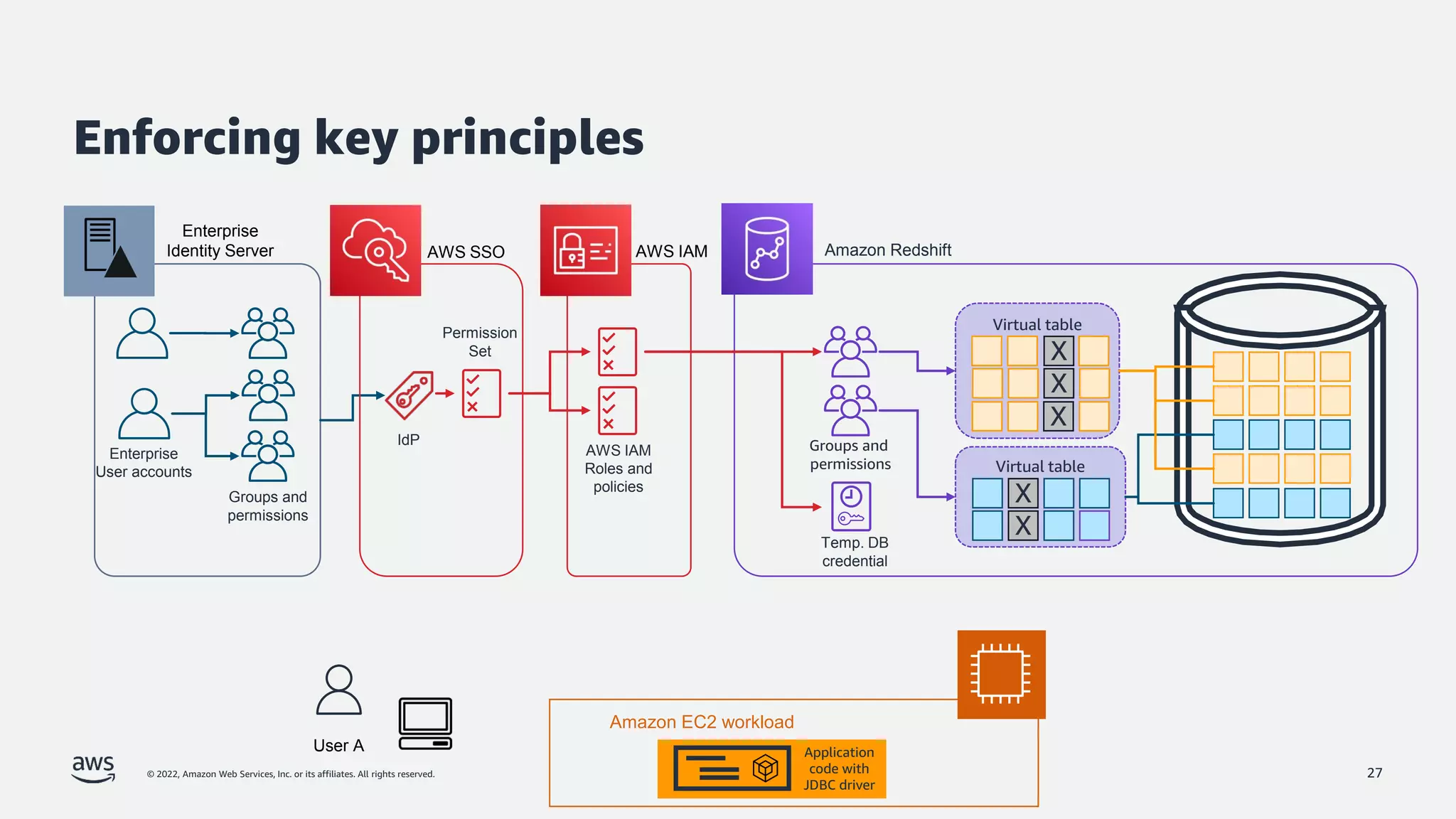
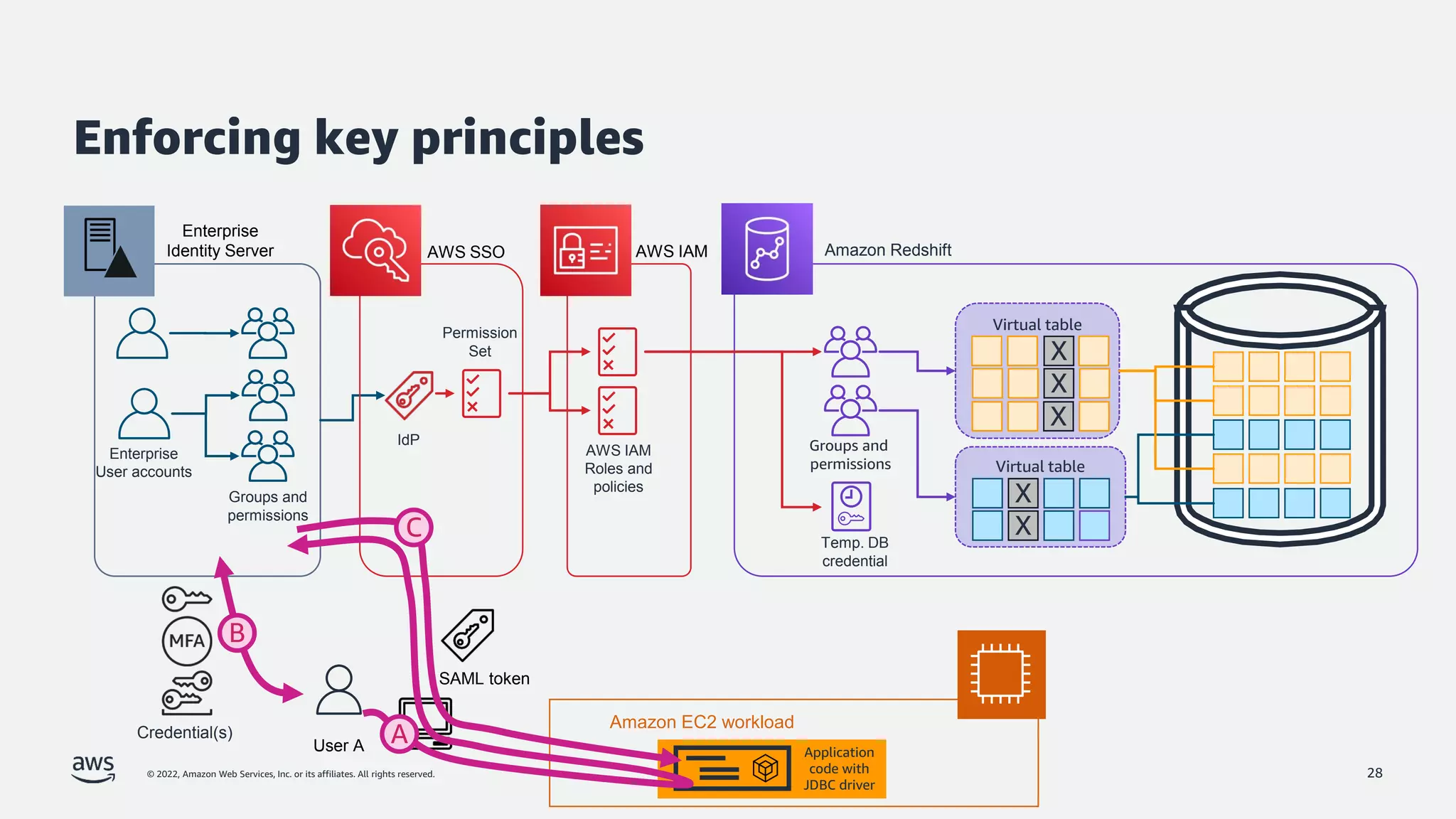
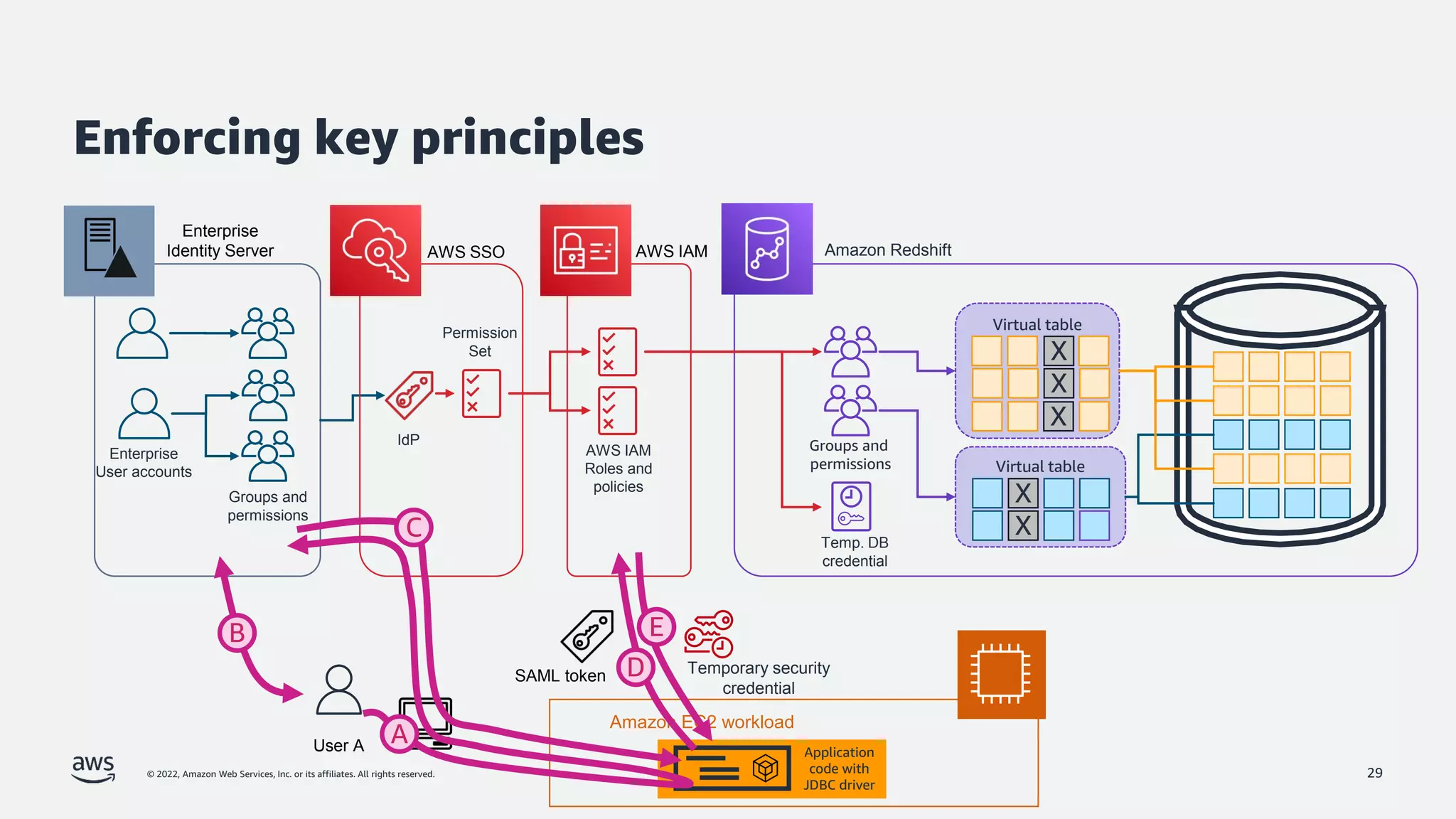
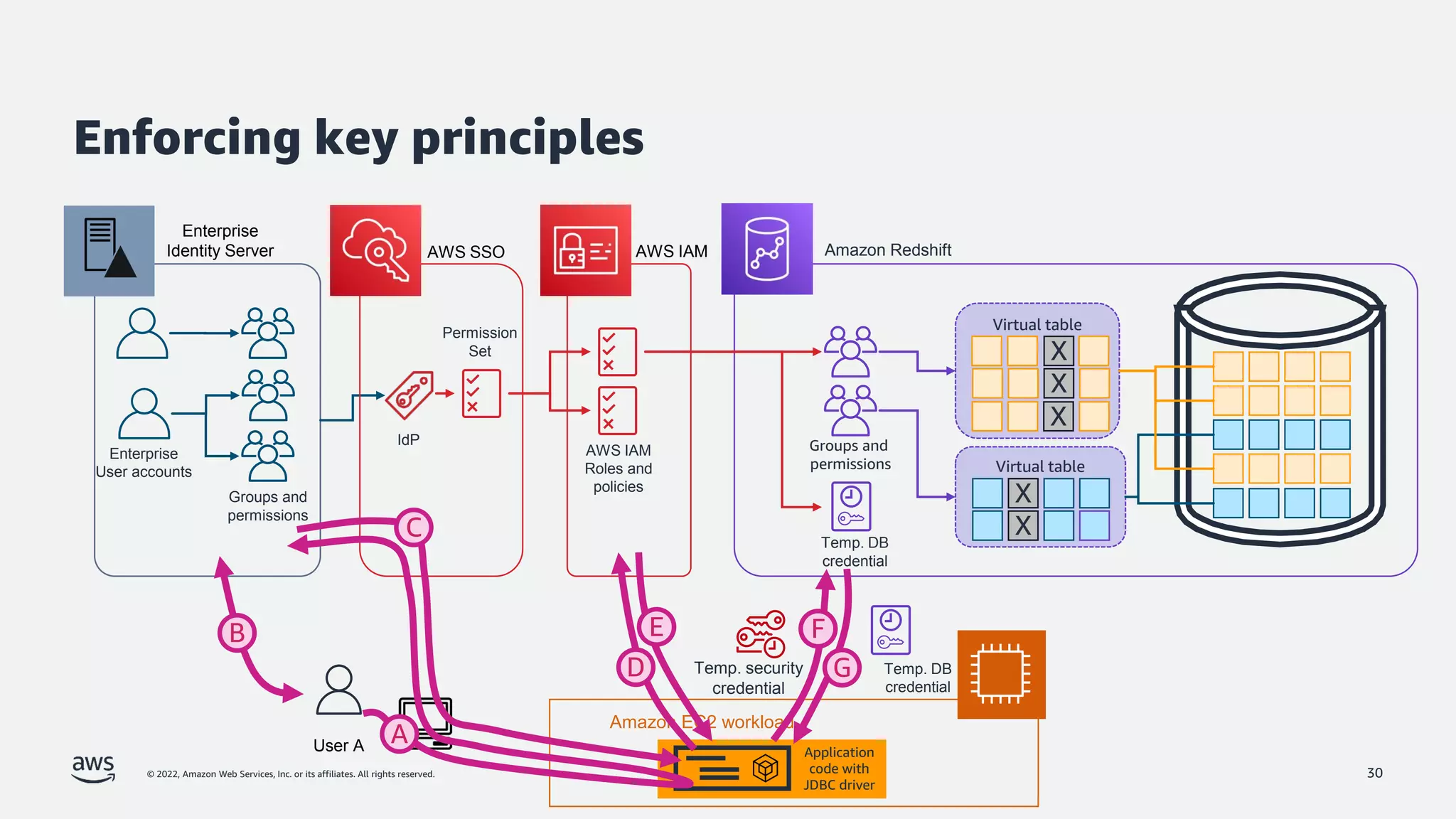
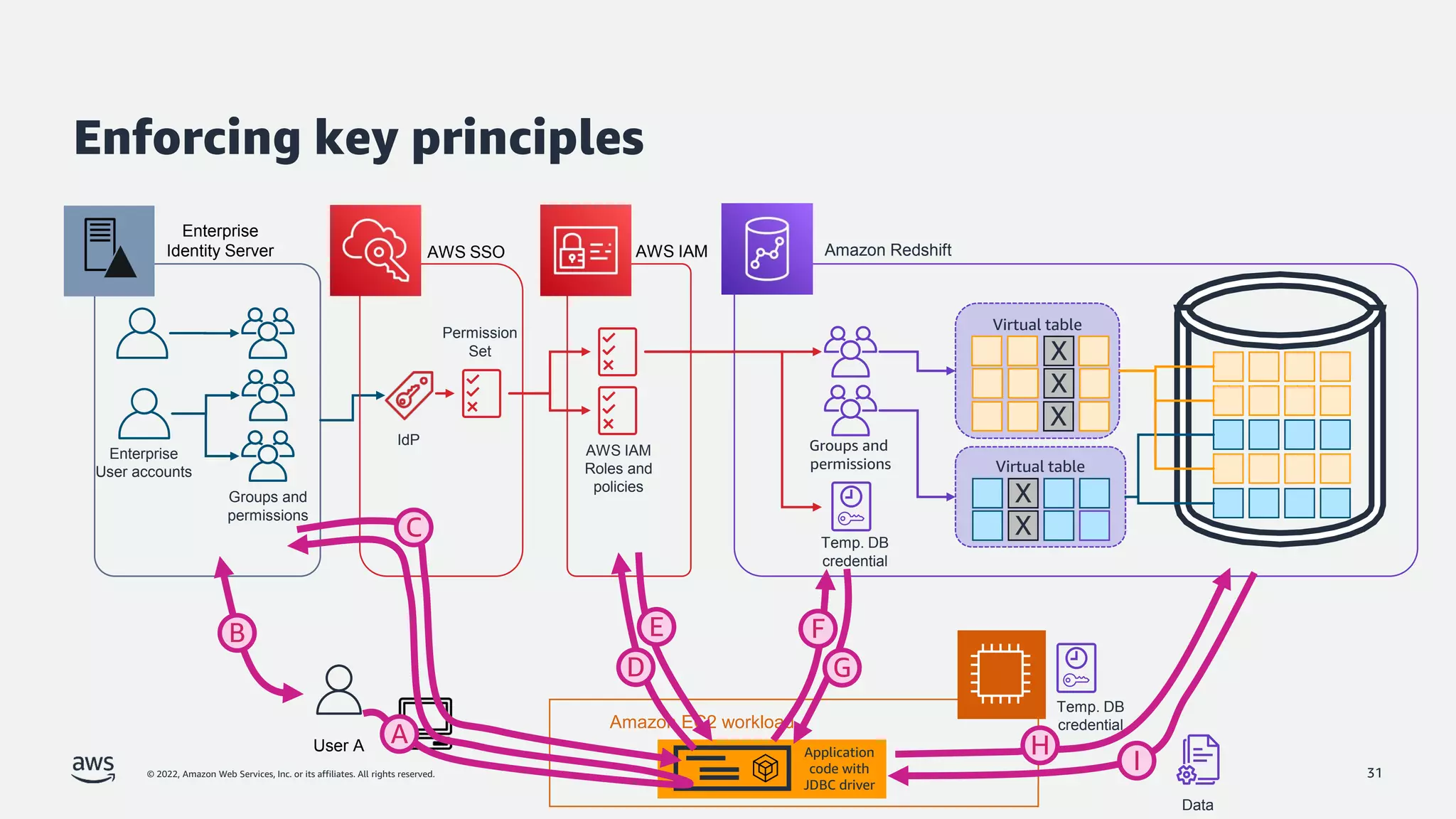
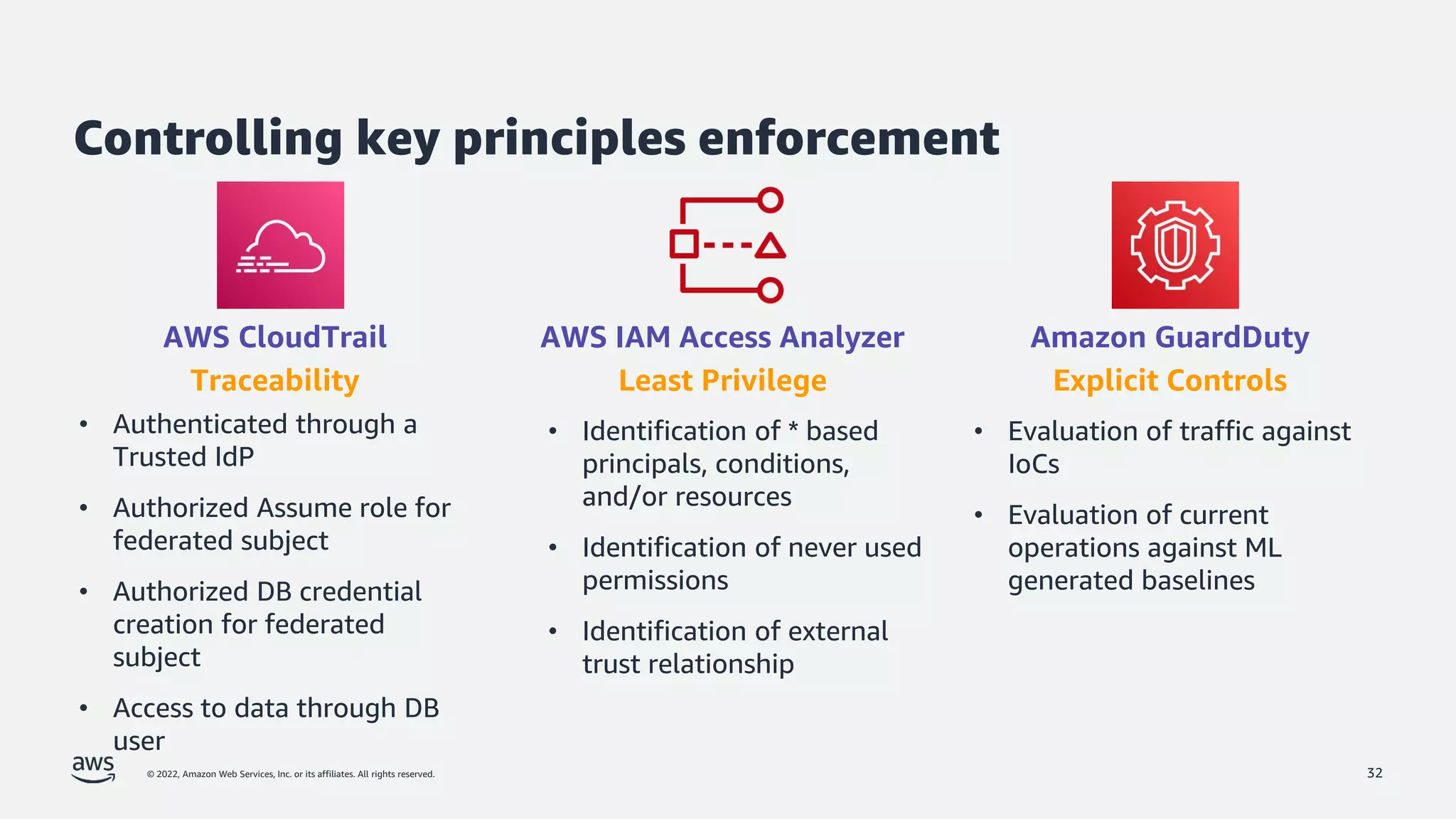
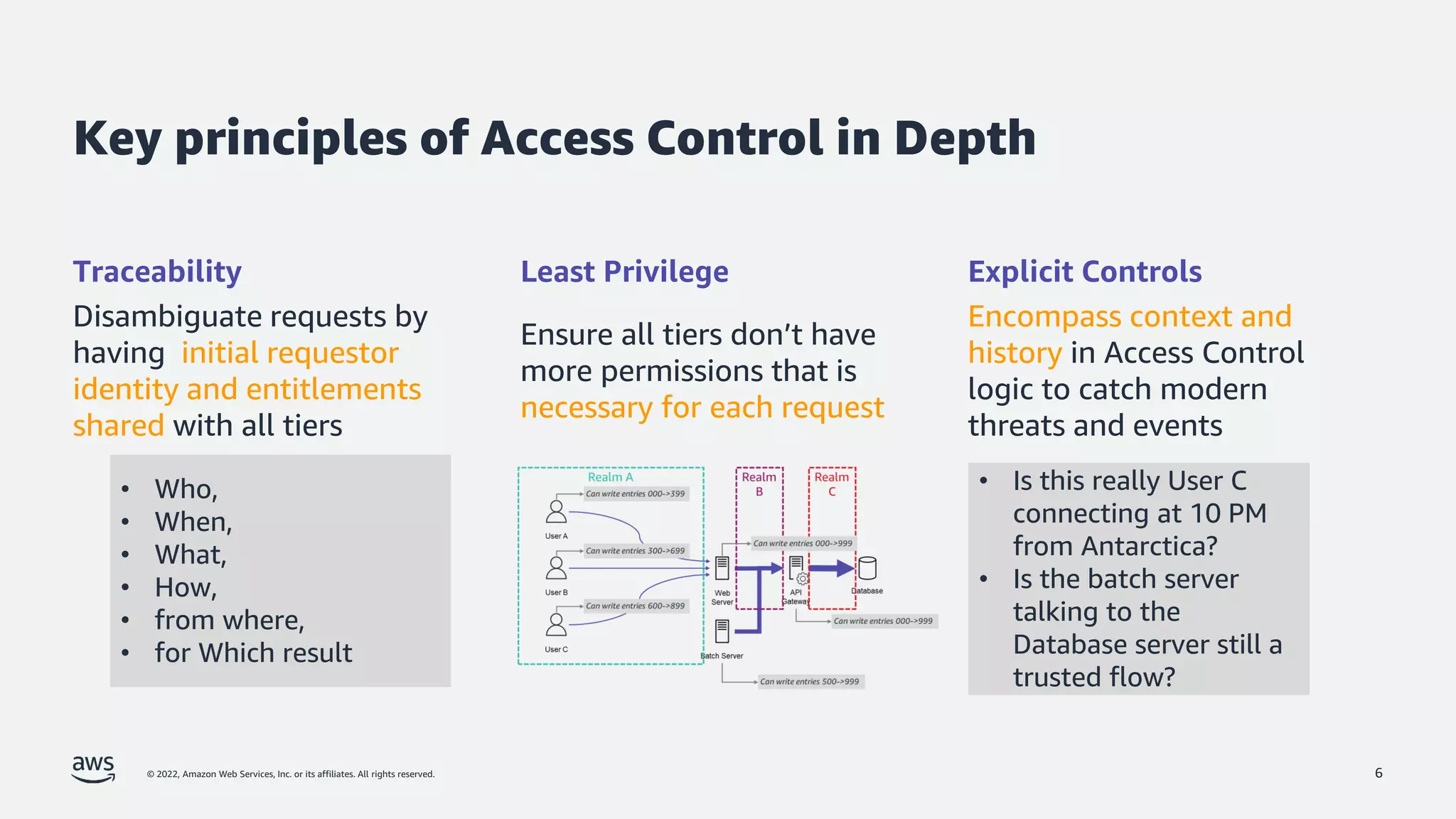
The document is a presentation by Jeff Lombardo from AWS discussing the principles and methods of enforcing access control in depth using AWS services. It outlines key access control principles, AWS access control capabilities, and emphasizes the importance of traceability and explicit controls to enhance security. Additionally, it includes practical examples and resources for learning more about building secure applications on AWS.






![© 2022, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Example
13
{
"Version": "2012-10-17",
"Statement": [{
"Sid": "1",
"Effect": "Allow",
"Principal": {"AWS": ["arn:aws:iam::111111111111:root"]},
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::mybucket",
"arn:aws:s3:::mybucket/*“
] ,
"Condition": {"Bool": {"aws:MultiFactorAuthPresent": "true"}}
}]
}](https://image.slidesharecdn.com/jefflombardo-enforcingaccesscontrolindepthwithaws-v1-220411145128/75/Jeff-Lombardo-Enforcing-access-control-in-depth-with-AWS-v1-2-pdf-13-2048.jpg)