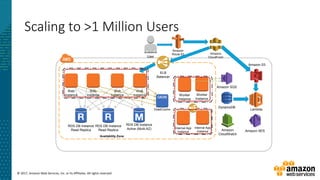
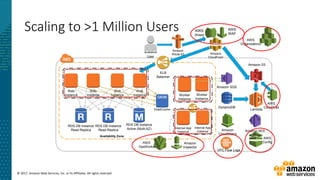
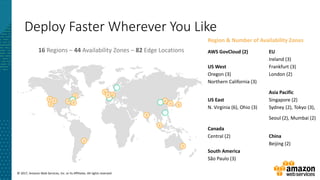
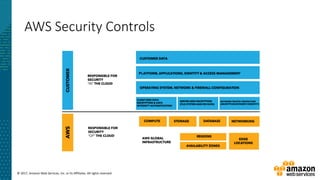
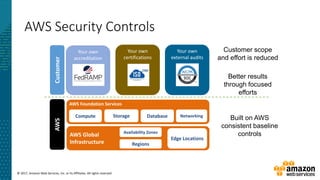
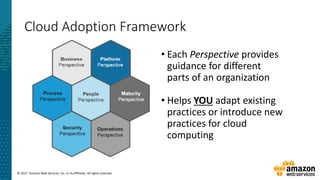
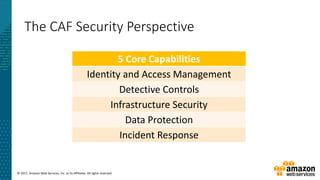
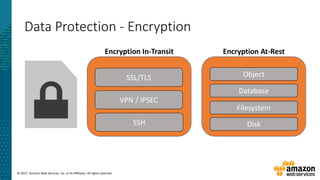
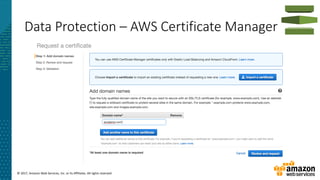
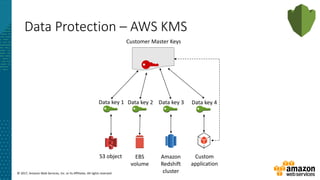
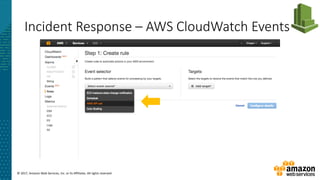
This document summarizes a presentation about security at scale on AWS. It discusses AWS security controls that customers don't need to manage themselves. It also outlines the AWS Cloud Adoption Framework for adapting security practices to the cloud. Finally, it provides examples of how to implement security capabilities like identity and access management, detective controls, infrastructure security, data protection, and incident response on AWS.

















![© 2017, Amazon Web Services, Inc. or its Affiliates. All rights reserved.
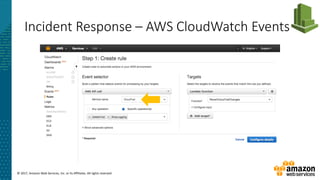
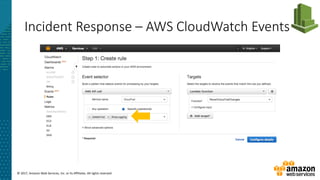
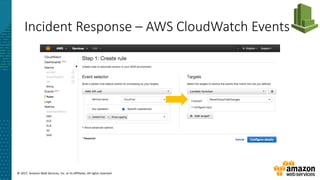
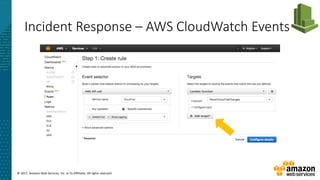
Incident Response – Lambda Respond
cloudtrail = boto3.client('cloudtrail')
trail_arn =
event["detail"]["requestParameters"]["name
"]
ct_response = cloudtrail.start_logging(
Name = trail_arn
)](https://image.slidesharecdn.com/securityatcloudscaledeepdive-2017-170817224438/85/Security-Cloud-Scale-Deep-Dive-39-320.jpg)
![© 2017, Amazon Web Services, Inc. or its Affiliates. All rights reserved.
Incident Response – Lambda Notify
sns_topic = "arn:aws:sns:us-east-1:123459227412:reporter-topic"
subject = 'EVENT: ' + event["detail"]["eventName"]
message = "What happened? " + event["detail"]["eventName"] + "n"
"What service? " + event["detail"]["eventSource"] + "n"
"Where? " + event["detail"]["awsRegion"] + "n"
"When? " + event["detail"]["eventTime"] + "n"
"Who? " + str(json.dumps(event["detail"]["userIdentity"], indent=2))
sns = boto3.client('sns')
sns_response = sns.publish(
TopicArn = sns_topic,
Message = message,
Subject = subject,
MessageStructure = 'string'
)](https://image.slidesharecdn.com/securityatcloudscaledeepdive-2017-170817224438/85/Security-Cloud-Scale-Deep-Dive-40-320.jpg)