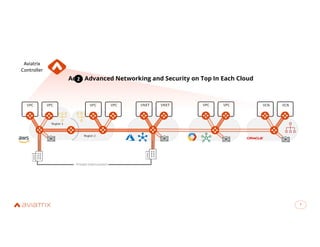
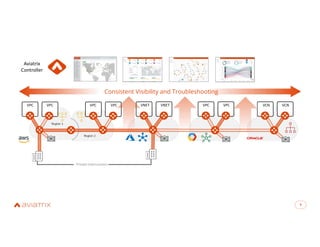
The document discusses Aviatrix's secure cloud networking solutions, emphasizing advanced networking capabilities and embedded security for multi-cloud environments. It highlights the business value of Aviatrix, including increased operational efficiency and reduced risks, and outlines the functionality of its cloud network platform. The agenda includes an introduction to Aviatrix, a demo of Aviatrix Copilot, and a deep dive on its features and benefits.