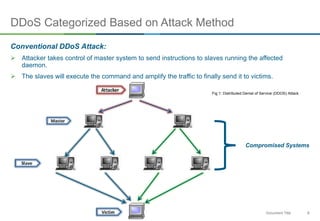
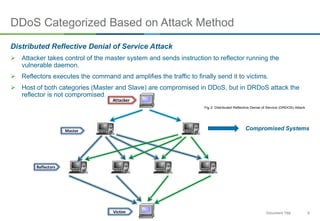
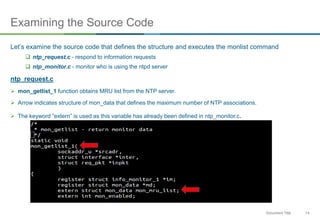
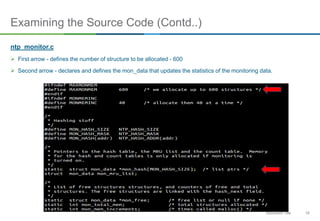
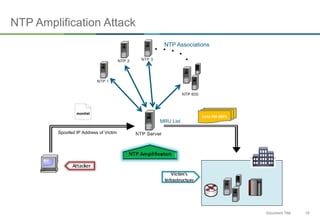
The document discusses NTP amplification attacks and their implications for various industries, detailing the nature of DDoS attacks, including definitions and classifications. It highlights the vulnerabilities of NTP protocols, particularly the monlist command, which can be exploited to generate excessive traffic towards targeted networks. The document also outlines countermeasures, such as upgrading NTP versions and implementing response rate limitations to mitigate these types of attacks.