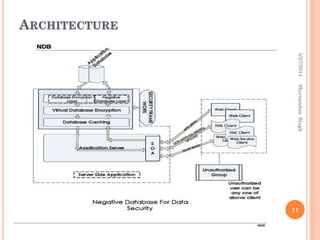
The document proposes a framework called a negative database to help prevent data theft. The negative database framework manipulates and stores original data in an encrypted form. It consists of four main modules: database caching, virtual database encryption, a database encryption algorithm, and a negative database conversion algorithm. The goal is to make the actual data difficult to understand if the encrypted database is accessed without authorization.