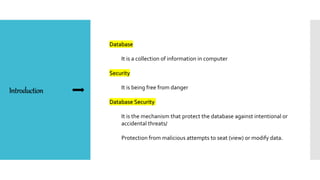
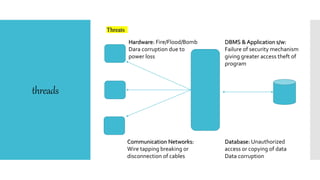
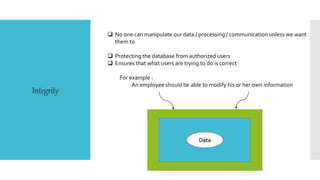
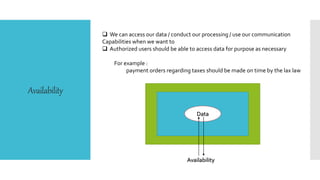
This document discusses database security. It defines database security as protecting database data from intentional or accidental threats. It identifies security risks to databases like bank accounts and grades. It covers database security concepts like confidentiality, integrity, and availability. It also discusses threats, security controls like access control and flow control, and methods to secure databases like authorization and encryption. The goal of database security is to protect critical data from unauthorized access according to an organization's security policy.