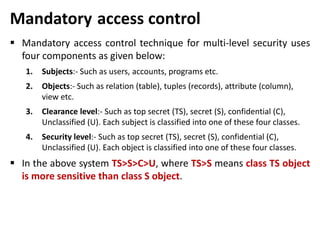
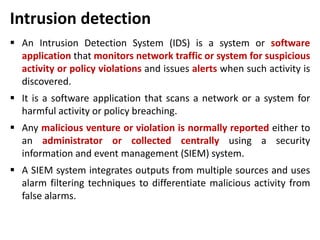
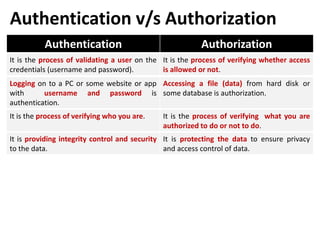
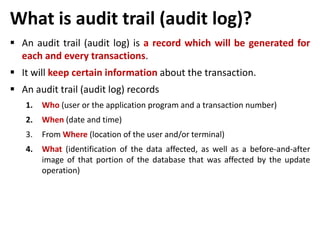
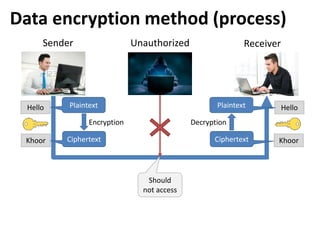
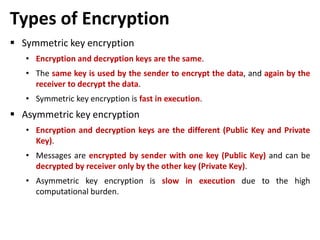
This document discusses various topics related to database security including authentication, authorization, access control methods, encryption, and intrusion detection. It defines data security as protecting data from unauthorized access and explains authentication verifies a user's identity while authorization verifies their access privileges. The document also distinguishes between discretionary access control which allows owners to specify access and mandatory access control which is system-enforced based on clearance levels. Symmetric and asymmetric encryption methods are overviewed along with the purpose of audit trails to log database transactions. Common attacks like SQL injection are also outlined.







![Discretionary access control
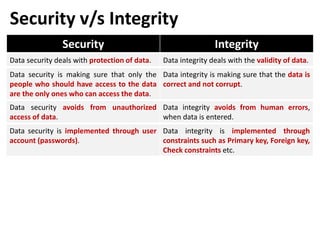
In discretionary access control (DAC), the owner of the object
specifies (decides) which subjects (user) can access the object.
In this method a single user can have different rights on different
objects, as well as different user can have different rights on the
same objects.
SQL support discretionary access control through the GRANT and
REVOKE commands.
GRANT
• This command gives rights to user for an object.
• Syntax:- GRANT privilege ON object TO user [WITH GRANT OPTION]
REVOKE
• This command takes back rights from user for an object.
• Syntax:- REVOKE privilege ON object FROM user {RESTRICT/CASCADE}](https://image.slidesharecdn.com/dbmsunit-7-240320035755-bd3fa2c8/85/Database-managementsystemes_Unit-7-pptxe-13-320.jpg)