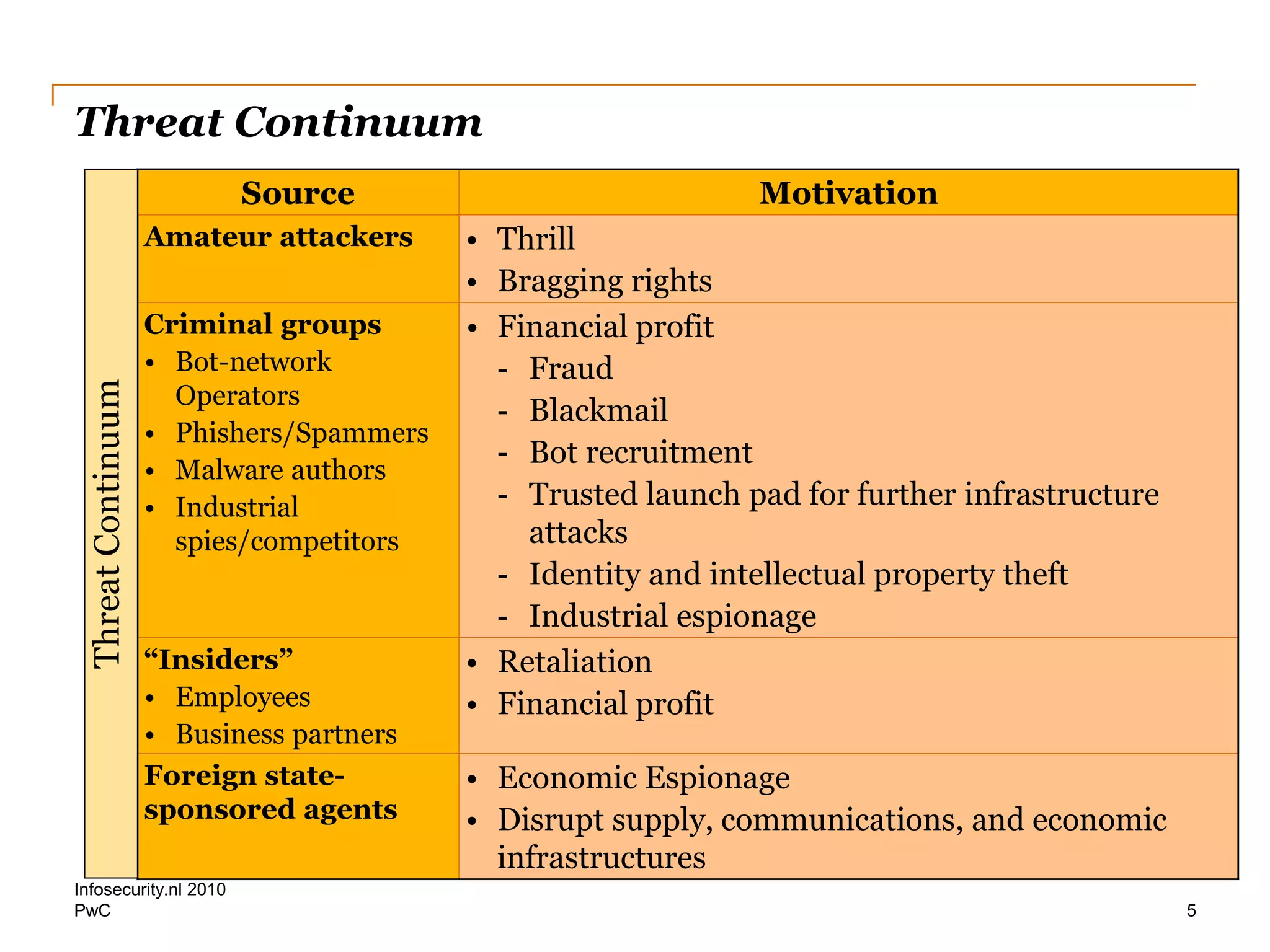
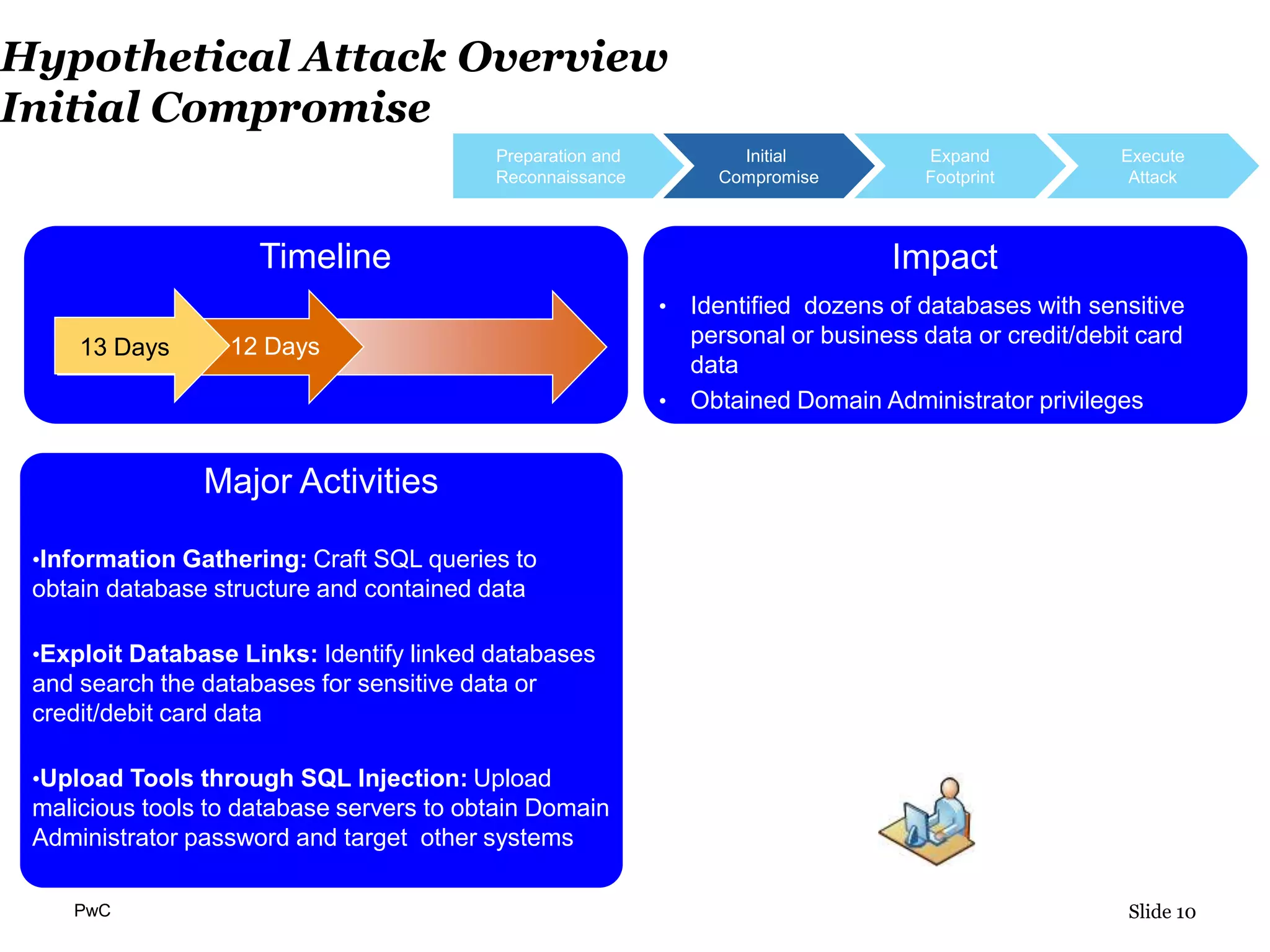
This document discusses current cyber threats and challenges. It describes a hypothetical attack scenario carried out by sophisticated attackers over several weeks. The attackers were able to compromise sensitive databases, obtain privileged access, monitor network activity, exfiltrate data, and manipulate financial account values to enable fraudulent transactions. The document calls for organizations to better inventory sensitive data, increase technical monitoring and audits, and ensure cybersecurity has independence and business insight. Public-private partnerships for threat information sharing are also recommended.