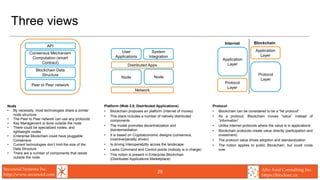
The document provides an overview of blockchain security considerations for designing and implementing blockchain technologies and applications. It discusses security architecture, threat modeling, smart contract security, privacy and data governance challenges, identity and access management, key management, security operations processes and monitoring. The document aims to educate those building blockchain systems on important cybersecurity best practices to consider.