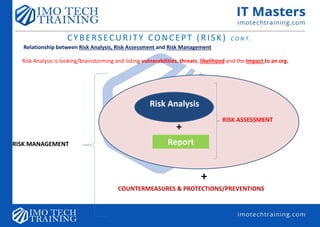
This document provides an overview and introduction to cybersecurity concepts. It discusses key topics such as risk, common attack types and vectors, security architecture principles including defense in depth and cryptography. Specifically, it defines cybersecurity and its objectives of confidentiality, integrity and availability. It also explains common cybersecurity concepts like vulnerabilities, threats and risk analysis and assessments. Various attack types are outlined including malware, advanced persistent threats, man-in-the-middle attacks and SQL injection.




























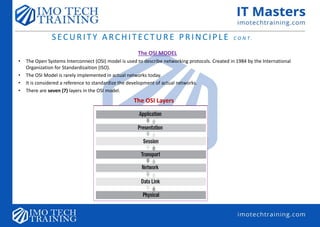
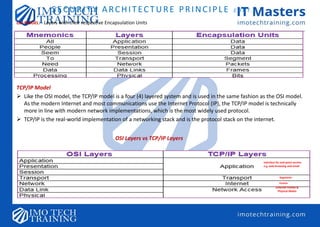
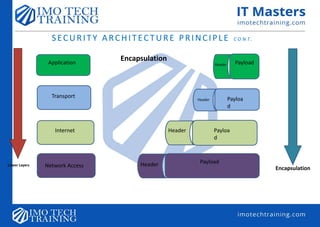
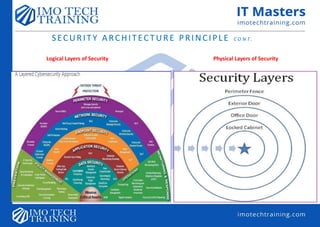
![Overview of Security Architecture
Security architecture—describes the structure, components, connections and layout of security controls within an
organization’s IT infrastructure.
• It shows how defense in depth is implemented.
• It also shows how layers of control are linked.
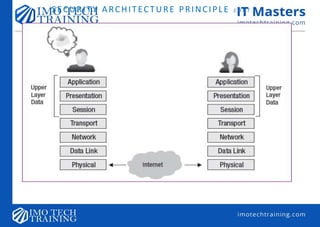
Security Perimeter—a well-defined boundary between the organization and the outside world.
In cybersecurity, the focus of security perimeter is Network or System-Centric where the emphasis is on placing
controls at the network and system levels to protect the information stored within.
Unlike the Data-Centric which emphasizes the protection of data regardless of its location.
With the advent of the Internet, outsourcing, mobile devices, cloud and other hosted services, the perimeter has expanded
considerably. Consequently, there are significant new risk and vulnerabilities to confront in this hyper-connected and
extended environment. The perimeter, is an important line of defense that protects the enterprise against external threats.
On the contrary, the degree of control over deperimeterized environments has been significantly reduced, especially in
enterprises permitting partial or full integration of user-owned mobile devices (i.e., bring your own device [BYOD]. These
changes have important ramifications for security architecture.
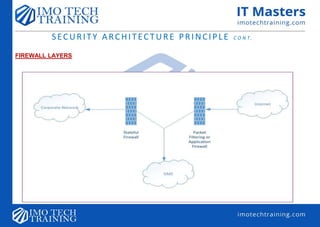
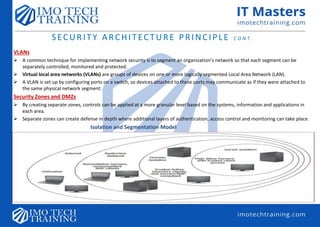
SECURITY ARCHITECTURE PRINCIPLE](https://image.slidesharecdn.com/week12introv2-upload-190810045237/85/Week-1-amp-2-intro_-v2-upload-30-320.jpg)