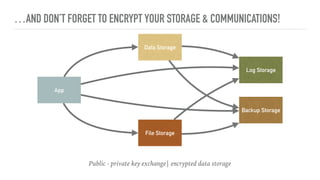
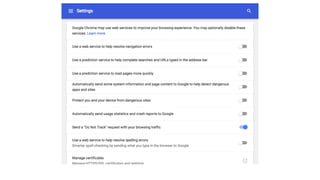
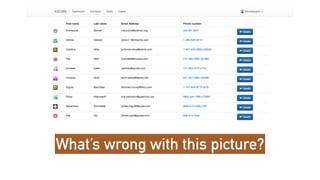
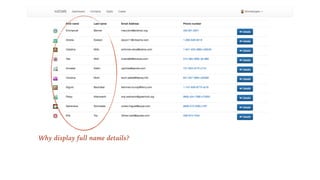
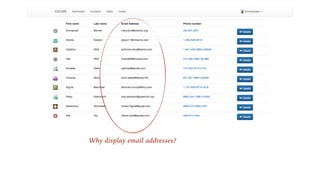
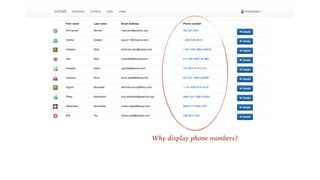
The document emphasizes the importance of privacy by design in software development, highlighting recent data breaches that resulted in significant personal and financial consequences for individuals. It offers practical advice for protecting user data, including minimizing data collection, implementing strong password management, and encrypting communication and storage. The document also stresses the need for transparency and respect for user trust, advocating for measures like anonymization and better access management to enhance data privacy.

































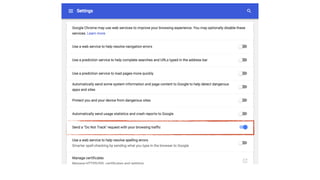
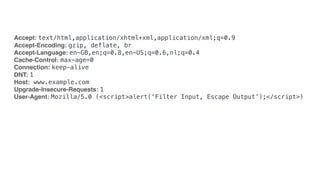
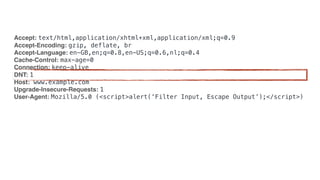


![INTERESTING FOR DISABLING GOOGLE ANALYTICS
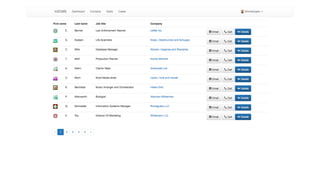
<?php if (!array_key_exists('HTTP_DNT', $_SERVER) || 1 !== (int) $_SERVER[‘HTTP_DNT’]): ?>
<!-- show your Google Analytics Script Here -->
<?php endif ?>](https://image.slidesharecdn.com/privacybydesign-171121142701/85/Privacy-by-design-46-320.jpg)






![REGULAR
EXPRESSIONS
cat server.log | sed -r 's/([0-9]+).([0-9]+)
.([0-9]+).([0-9]+)/1.xxx.xxx.4/g' -](https://image.slidesharecdn.com/privacybydesign-171121142701/85/Privacy-by-design-65-320.jpg)