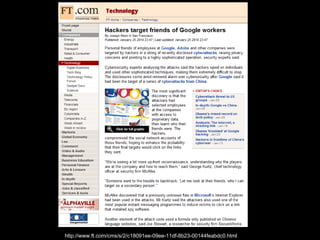
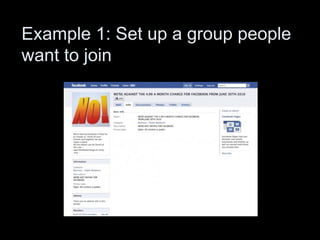
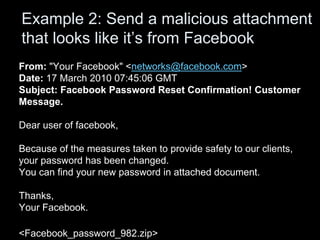
This document discusses how social engineers exploit social networking sites for malicious purposes such as gathering sensitive information, distributing malware, and executing attacks. It provides examples of common social engineering techniques used over social networks, including impersonating individuals to gain their trust, hijacking accounts to target friends, and setting up fake groups or sending malicious attachments disguised as coming from trusted sources like Facebook. The document also explains how social networks are used for reconnaissance by revealing personal details that can help social engineers craft more convincing phishing attacks.