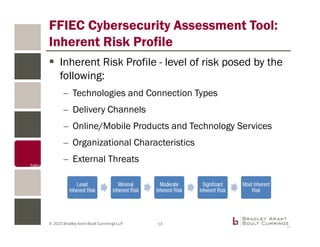
The document discusses cybersecurity planning and incident response strategies for organizations, emphasizing the development of comprehensive data breach response plans and risk assessment procedures. It outlines the roles of Information Sharing and Analysis Centers (ISACs) and details regulatory requirements from the FTC and HIPAA for consumer data protection. Key recommendations include pre-incident preparation, measures for addressing incidents, and ongoing monitoring and assessment to enhance cybersecurity resilience.