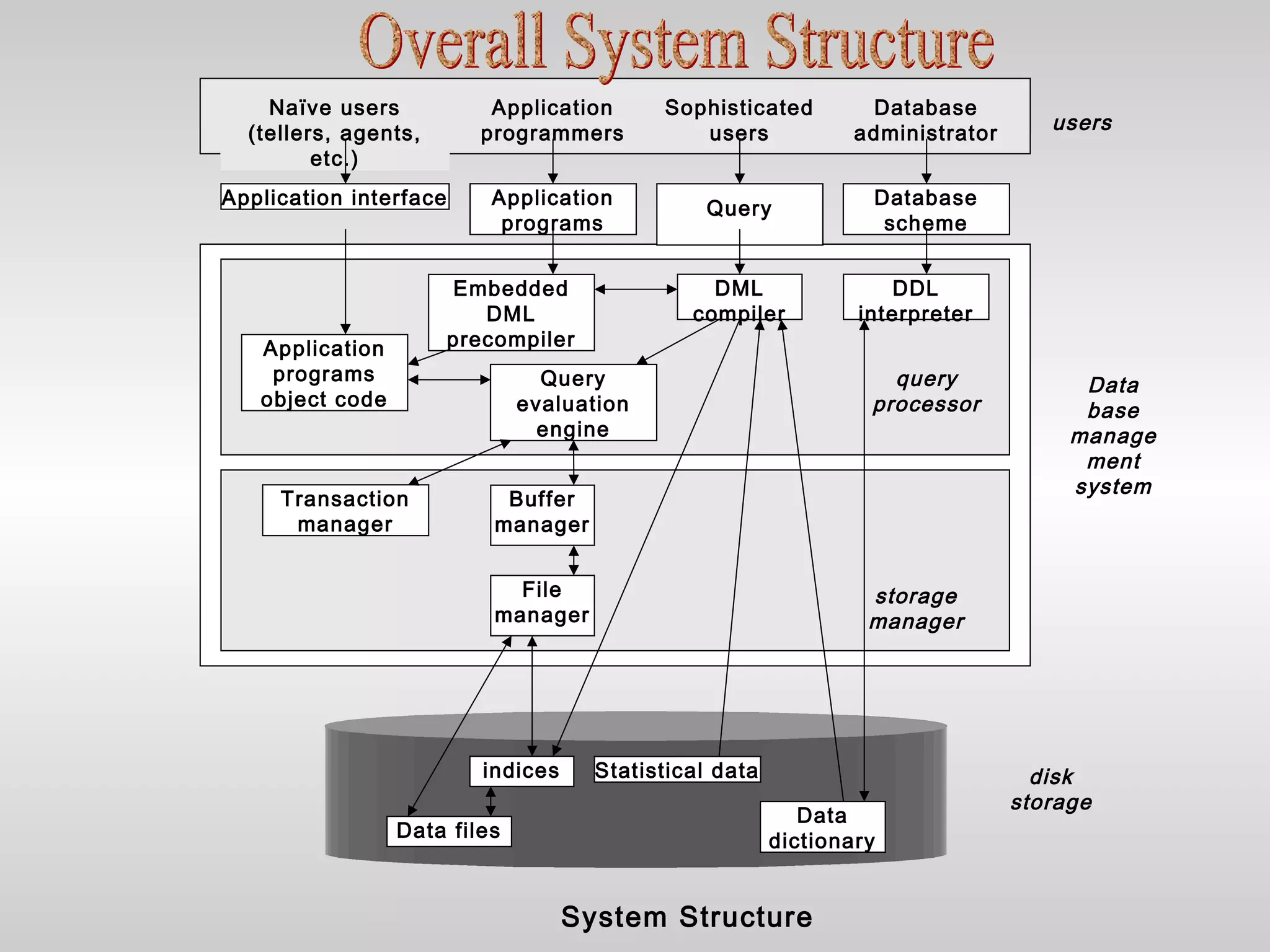
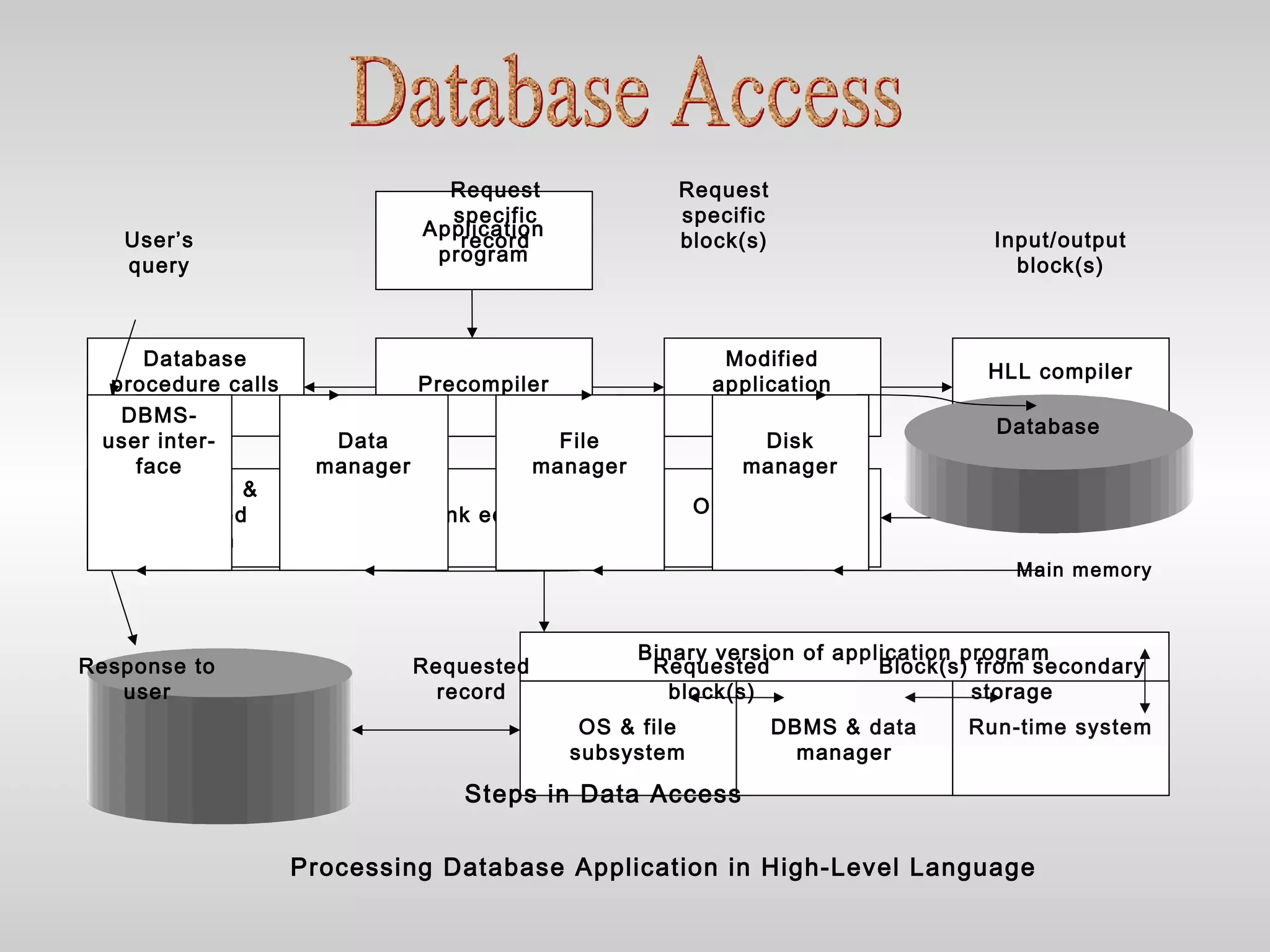
This document discusses database management systems (DBMS) and their key characteristics and components. It covers three main points:
1) It describes the main functions of a DBMS, including maintaining data integrity, enforcing access rules, providing backup/recovery procedures, and allowing shared data access across applications.
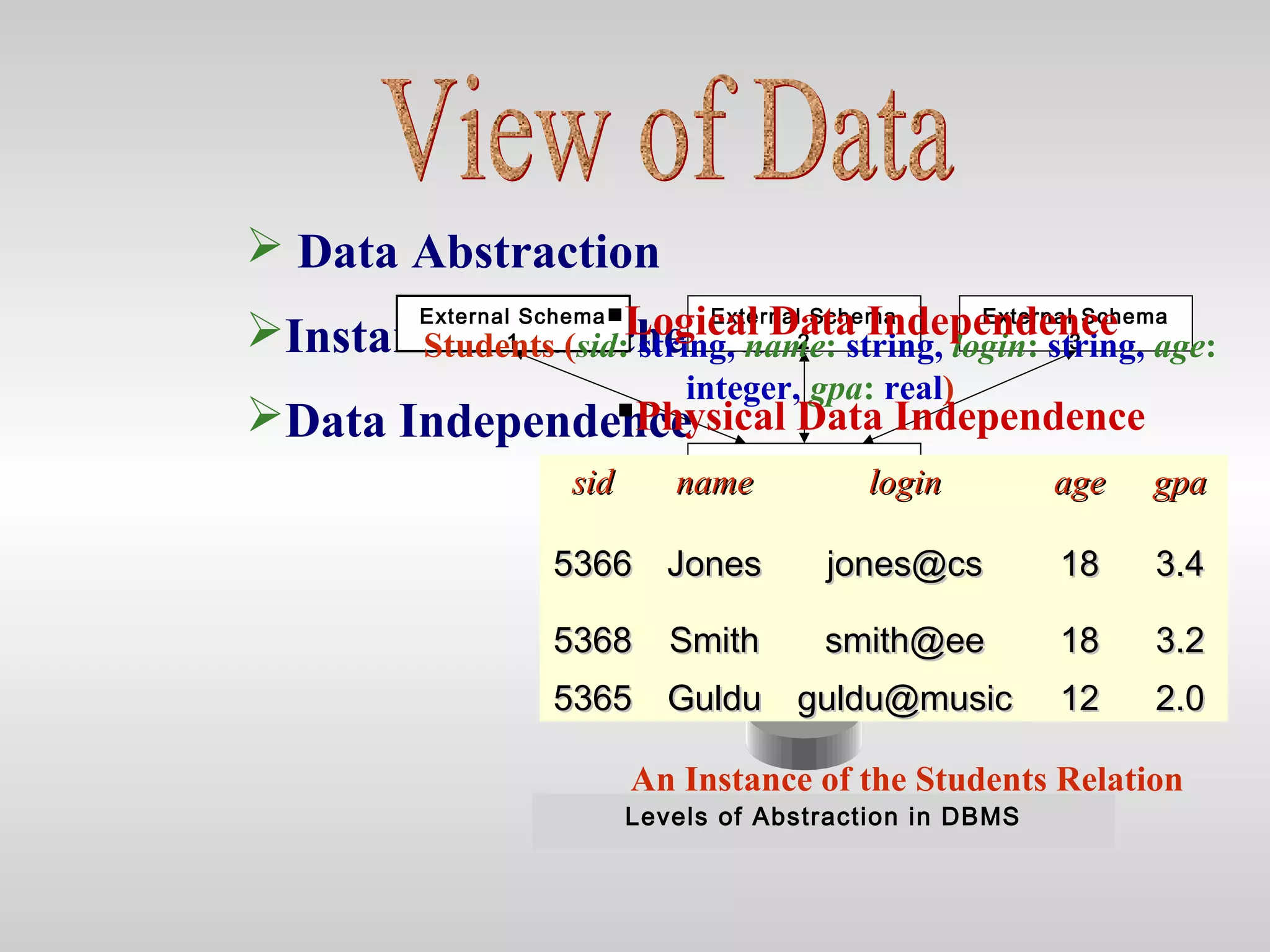
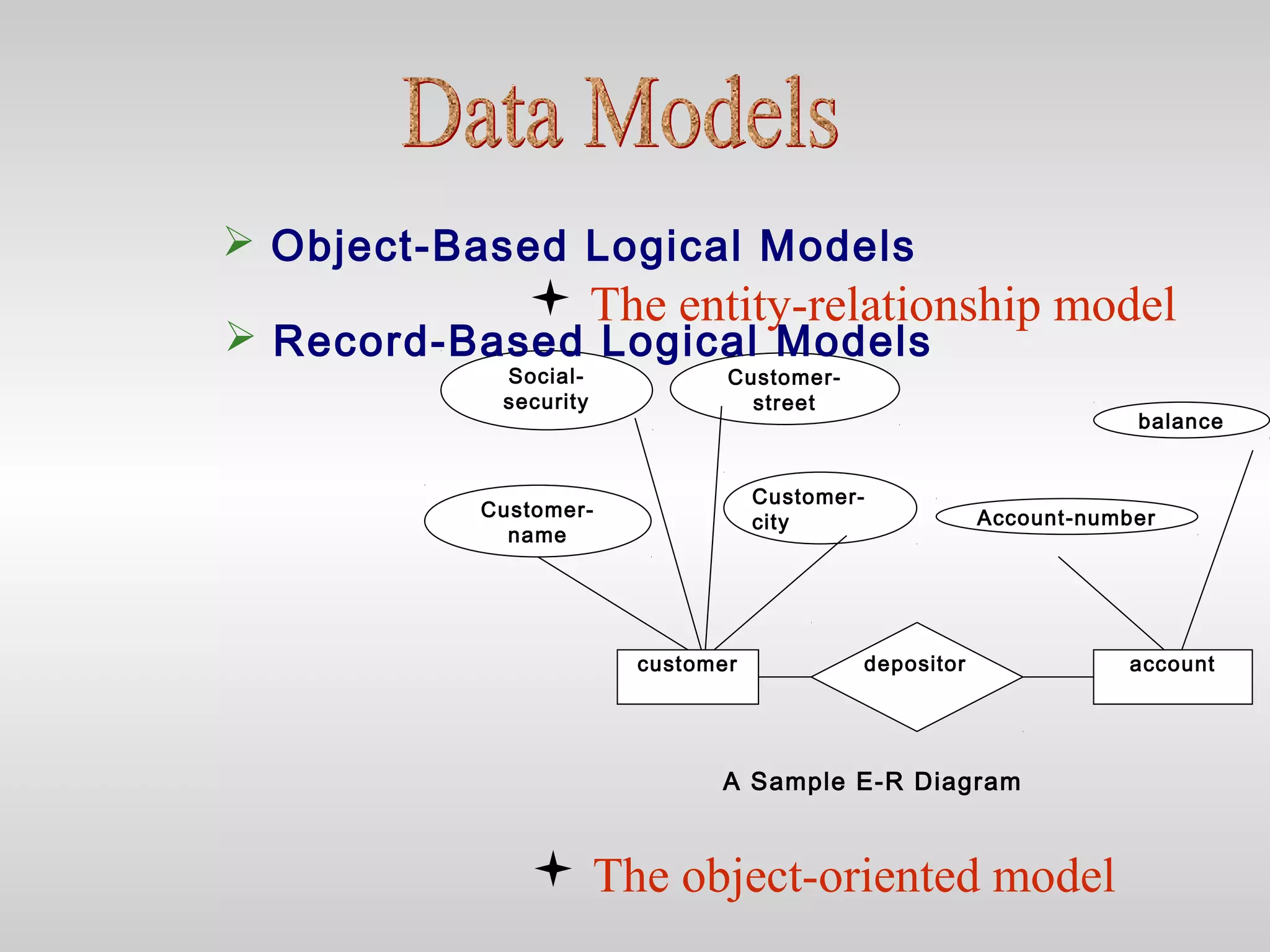
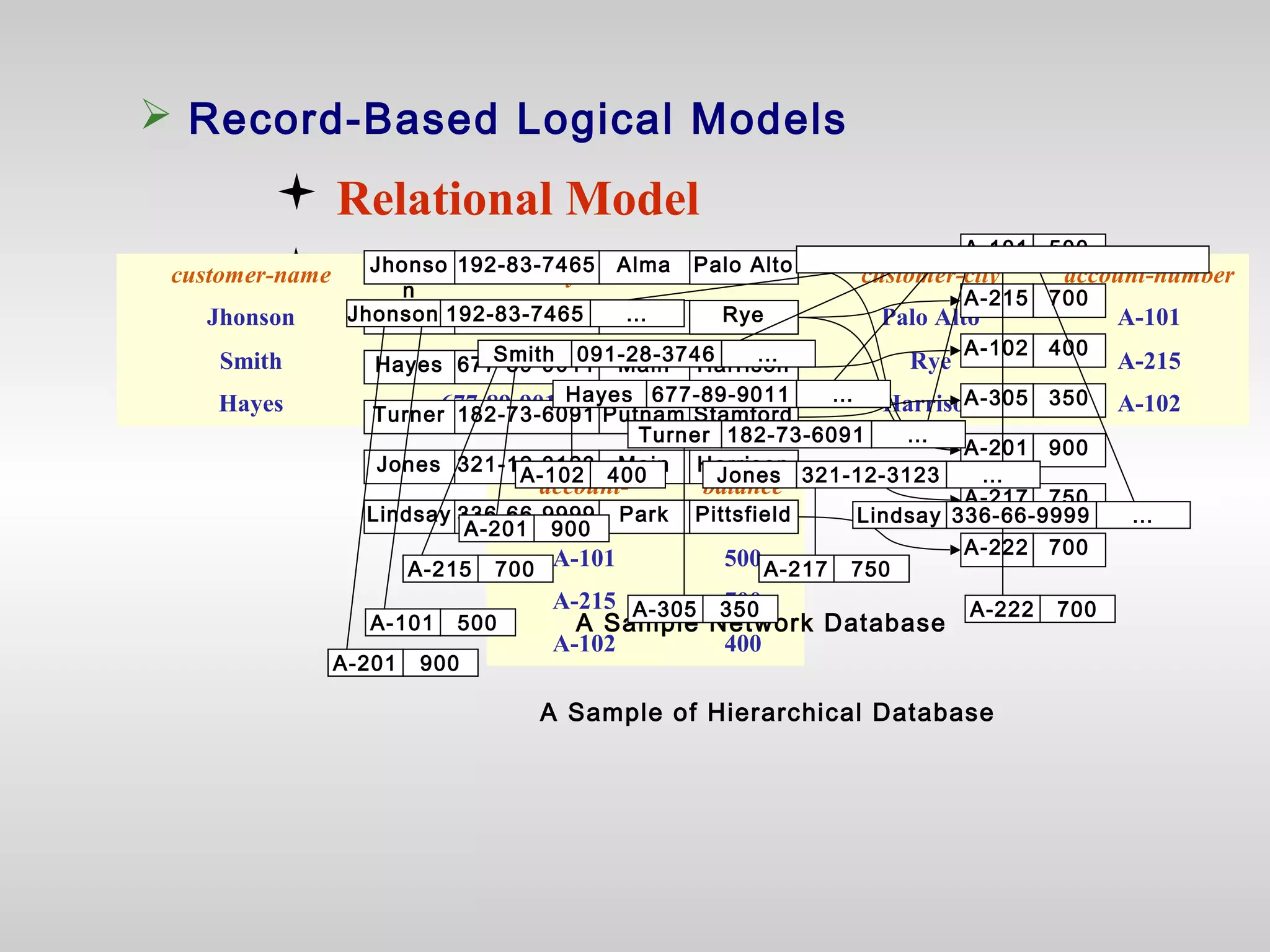
2) It outlines different database models like relational, network, and hierarchical and discusses logical and physical data independence.
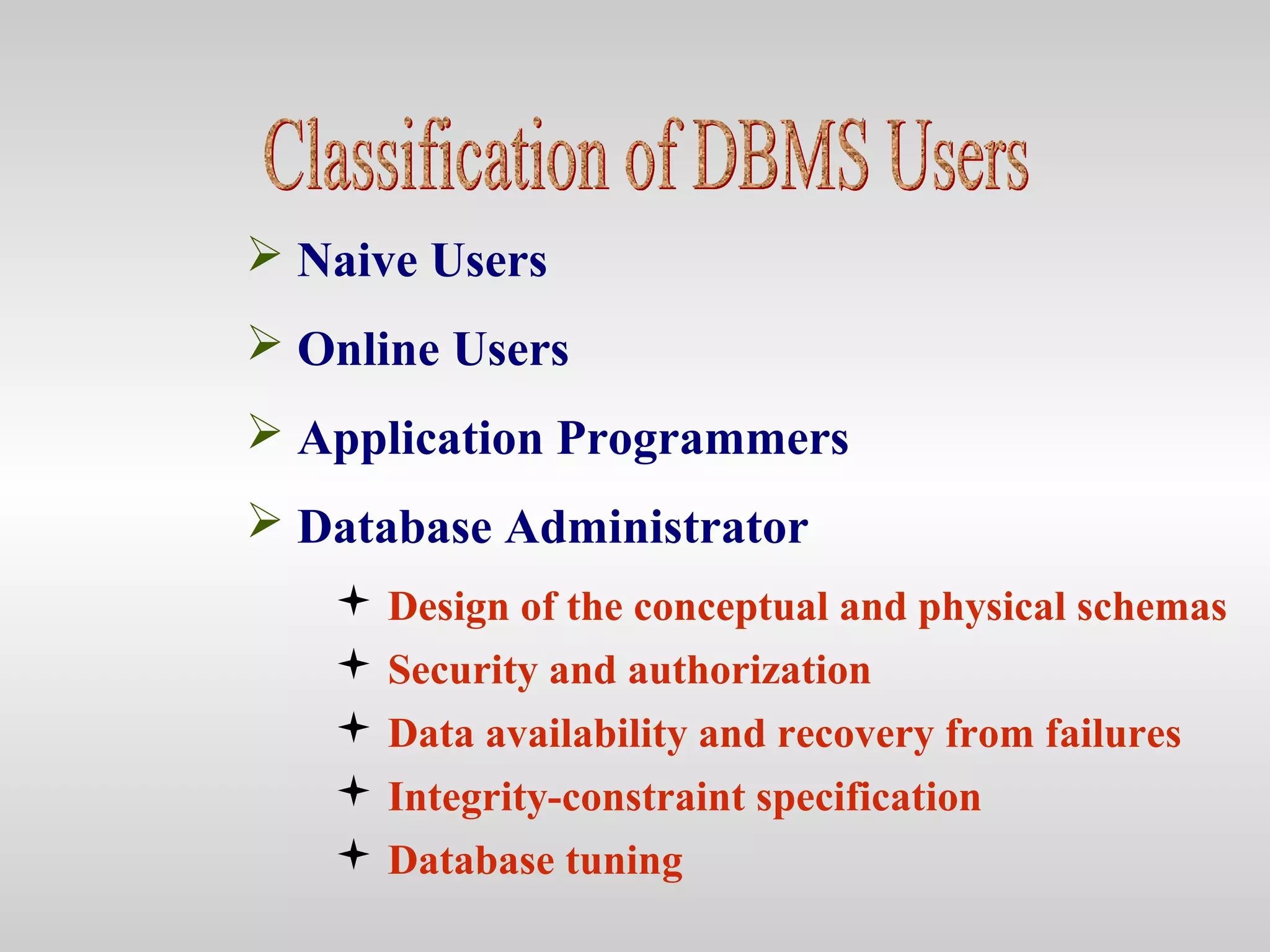
3) It explores the architecture of a DBMS and how users and programs interact with the database through a DBMS interface to perform queries, updates, and other data management tasks.