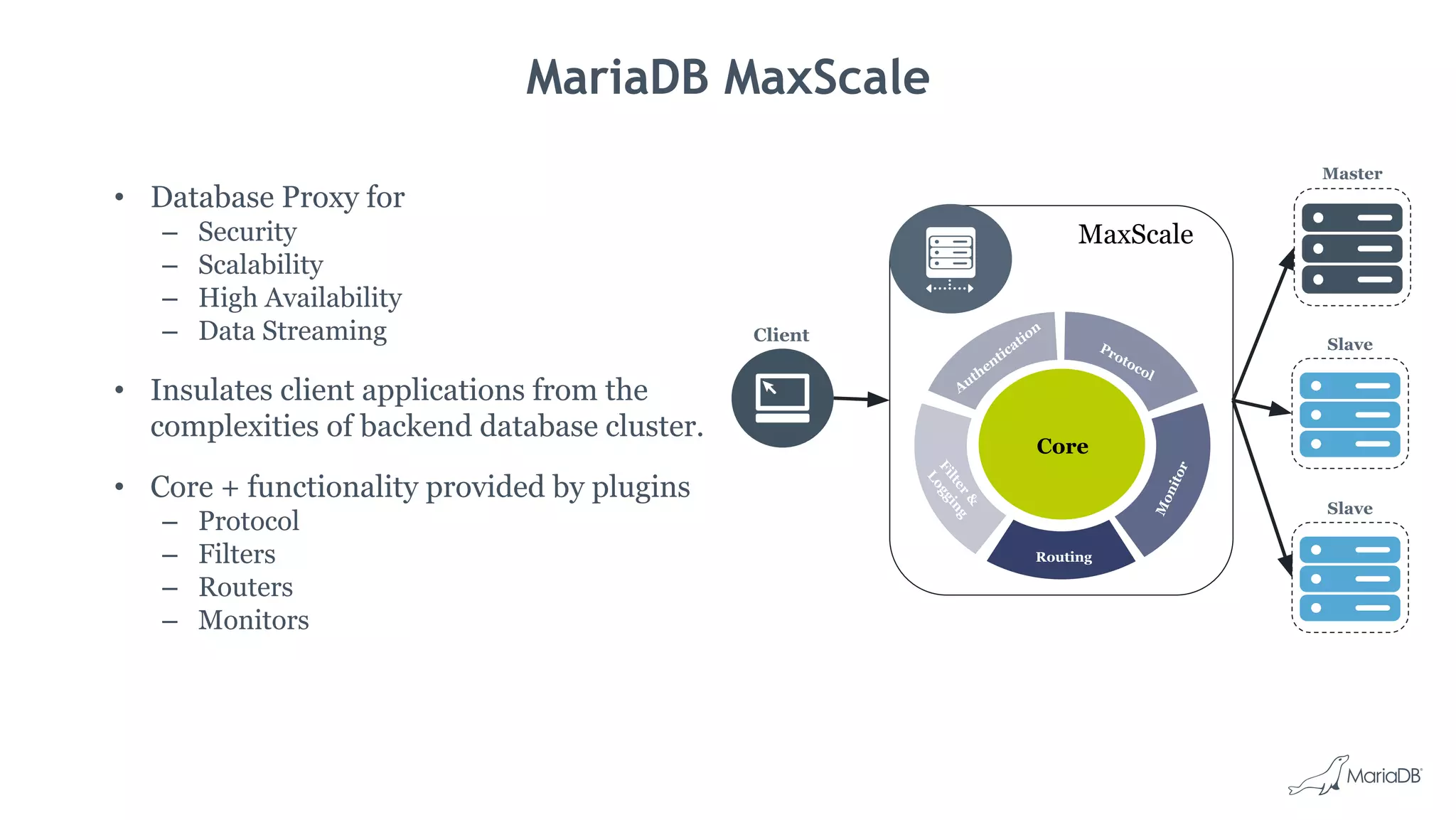
The document discusses database security best practices for MariaDB, including threats from the internet, applications, excessive trust, and recommendations for defense. It provides guidance on encryption, using a database proxy like MaxScale, user management, auditing, and security features of MariaDB and MaxScale such as authentication, encryption, attack protection, and data masking.













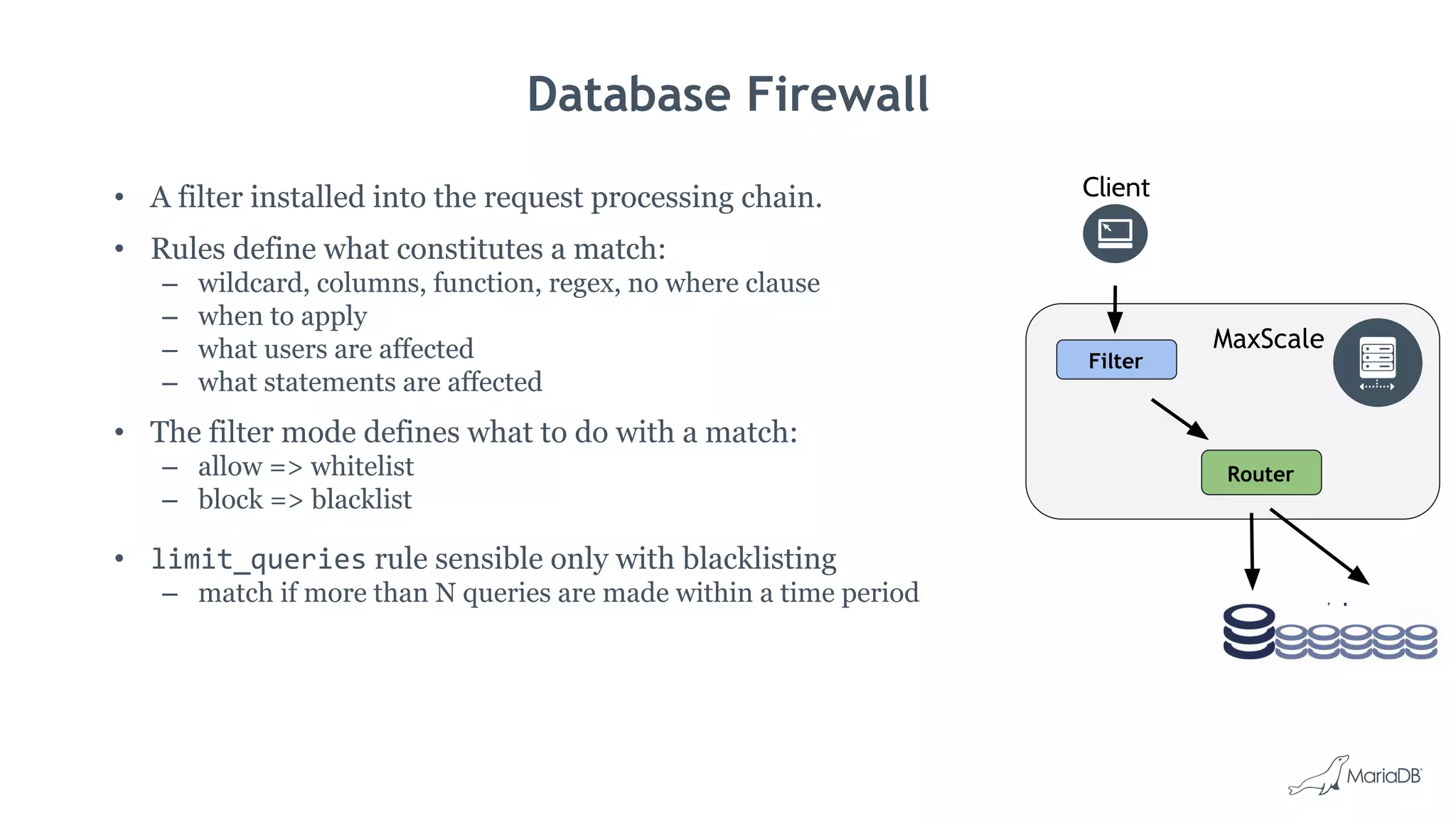
![Database Firewall Example
[TheFirewall]
type=filter
module=dbfwfilter
action=block
rules=firewall-rules.txt
[TheService]
type=service
...
filters=TheFirewall
MaxScale configuration file.
rule require_where_clause deny no_where_clause on_queries select
users %@% match all rules require_where_clause
Only defines what constitutes a match.
● wildcard
● columns col1-name col2-name …
● regex regular expression
● no_where_clause
● ...
on_queries [select|update|...]
MySQL [testdb]> select * from table;
ERROR 1141 (HY000): Access denied for user 'johan'@'127.0.0.1': Required WHERE/HAVING
clause is missing.
MySQL [testdb]>](https://image.slidesharecdn.com/roadshowdatabasesecuritythreats-mariadbsecuritybestpractices-171106093829/75/Database-Security-Threats-MariaDB-Security-Best-Practices-23-2048.jpg)
![DDoS: Server Overload Protection
• Persistent connections to backend.
– When server connections are logically closed, keep them
in pool for reuse.
• Client connection limitation.
– Specify the maximum number of connections for a
particular service.
• Limit rate of queries using the firewall.
[SomeService]
...
max_connections=100
maxscale.cnf[SomeServer]
...
maxpersistpoolmax=30
maxscale.cnf
rule prevent_overload deny limit_queries 15 5 10
firewall.txt
Client Client Client Client
If more than 15 queries are received in 5 seconds, block all queries for 10 seconds.](https://image.slidesharecdn.com/roadshowdatabasesecuritythreats-mariadbsecuritybestpractices-171106093829/75/Database-Security-Threats-MariaDB-Security-Best-Practices-24-2048.jpg)
![DDoS: Network Overload Protection
• Cap the amount that can be returned.
– By rows or by size.
– Data will be returned to MaxScale, but MaxScale will not
necessarily forward to client.
• Limit rate of queries using the firewall.
[LimitSize]
type=filter
module=maxrows
max_resultset_rows=500
firewall.txt
Client Client Client Client
rule prevent_overload deny limit_queries 15 5 10](https://image.slidesharecdn.com/roadshowdatabasesecuritythreats-mariadbsecuritybestpractices-171106093829/75/Database-Security-Threats-MariaDB-Security-Best-Practices-25-2048.jpg)

![MaxRows Configuration Example
[TheLimitations]
type=filter
module=maxrows
max_resultset_rows=1000
max_resultset_size=262144
max_resultset_return=error
[TheService]
type=service
...
filters=TheLimitations
At most 1000 rows may be returned.
At most 256 kilobytes may be returned.
That could also be expressed as 256Ki.
If either the rows or size limit is reached,
return an error packet containing the
offending statement.
MariaDB [(test)]> select * from table;
ERROR 1415 (0A000): Row limit/size exceeded for query: select * from table](https://image.slidesharecdn.com/roadshowdatabasesecuritythreats-mariadbsecuritybestpractices-171106093829/75/Database-Security-Threats-MariaDB-Security-Best-Practices-27-2048.jpg)

![Selective Data Masking Configuration Example
{
"rules": [
{
"replace": {
"column": "ssn"
},
"with": {
"value": "XXX-XX-XXXX",
"fill": "Y"
},
"exempted": [ "'admin'" ]
}
]
}
[TheMasking]
type=filter
module=masking
warn_type_mismatch=always
large_payload=abort
rules=masking_rules.json
[TheService]
type=service
...
filters=TheMasking
Replace the value of all columns whose
name is “SSN” irrespective of which
table or database is in question.
Replace the value with
“XXX-XX-XXXX”. However, that will be
done only if the length of the database
value is exactly the same as the length
of the replacement string.
Should the length of the database value not
exactly match the length of the
replacement string, replace the value with
as many “Y” as needed.
The masking is applied to every user (no
applies_to key), except the user
“admin”.](https://image.slidesharecdn.com/roadshowdatabasesecuritythreats-mariadbsecuritybestpractices-171106093829/75/Database-Security-Threats-MariaDB-Security-Best-Practices-29-2048.jpg)