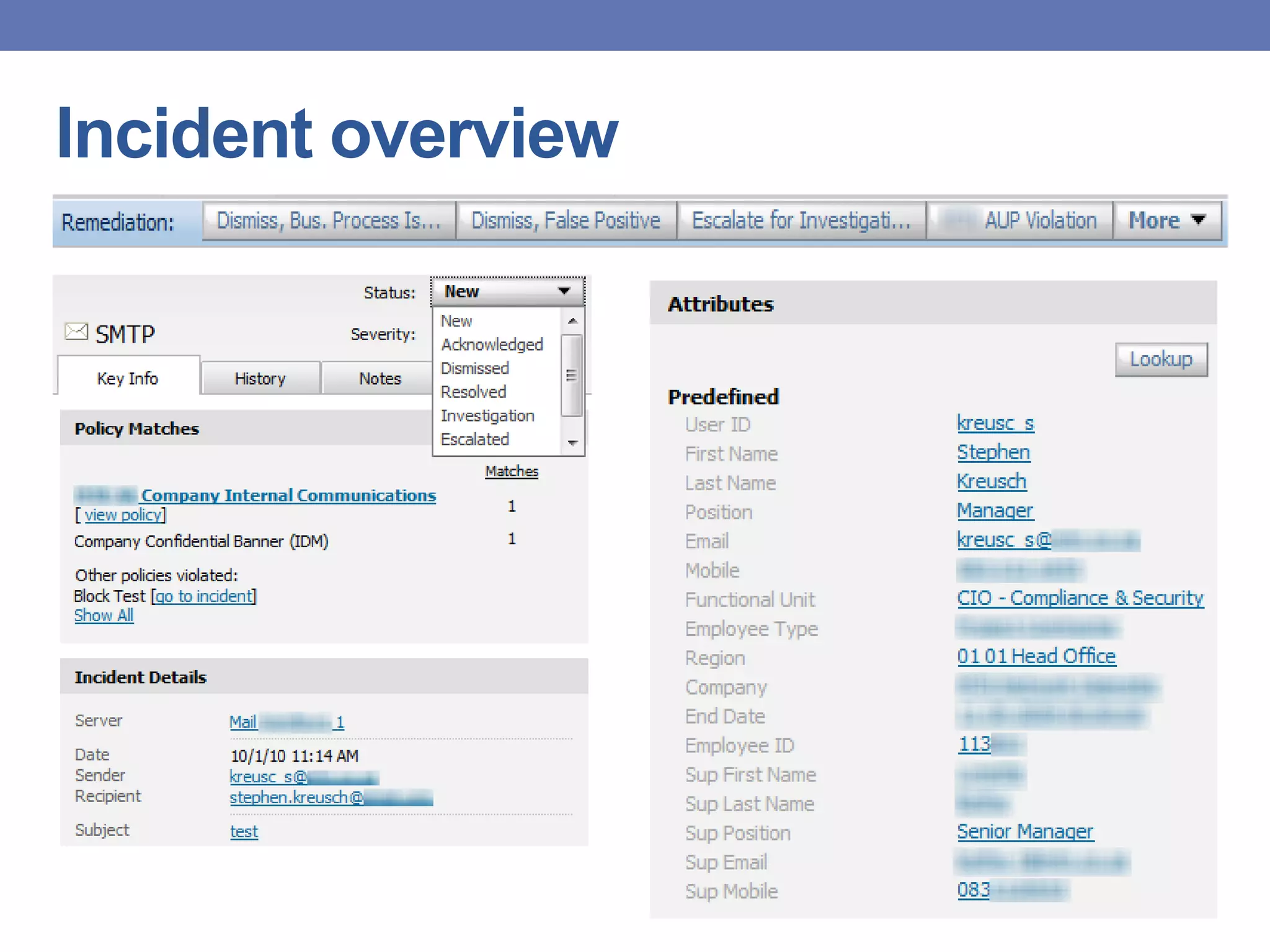
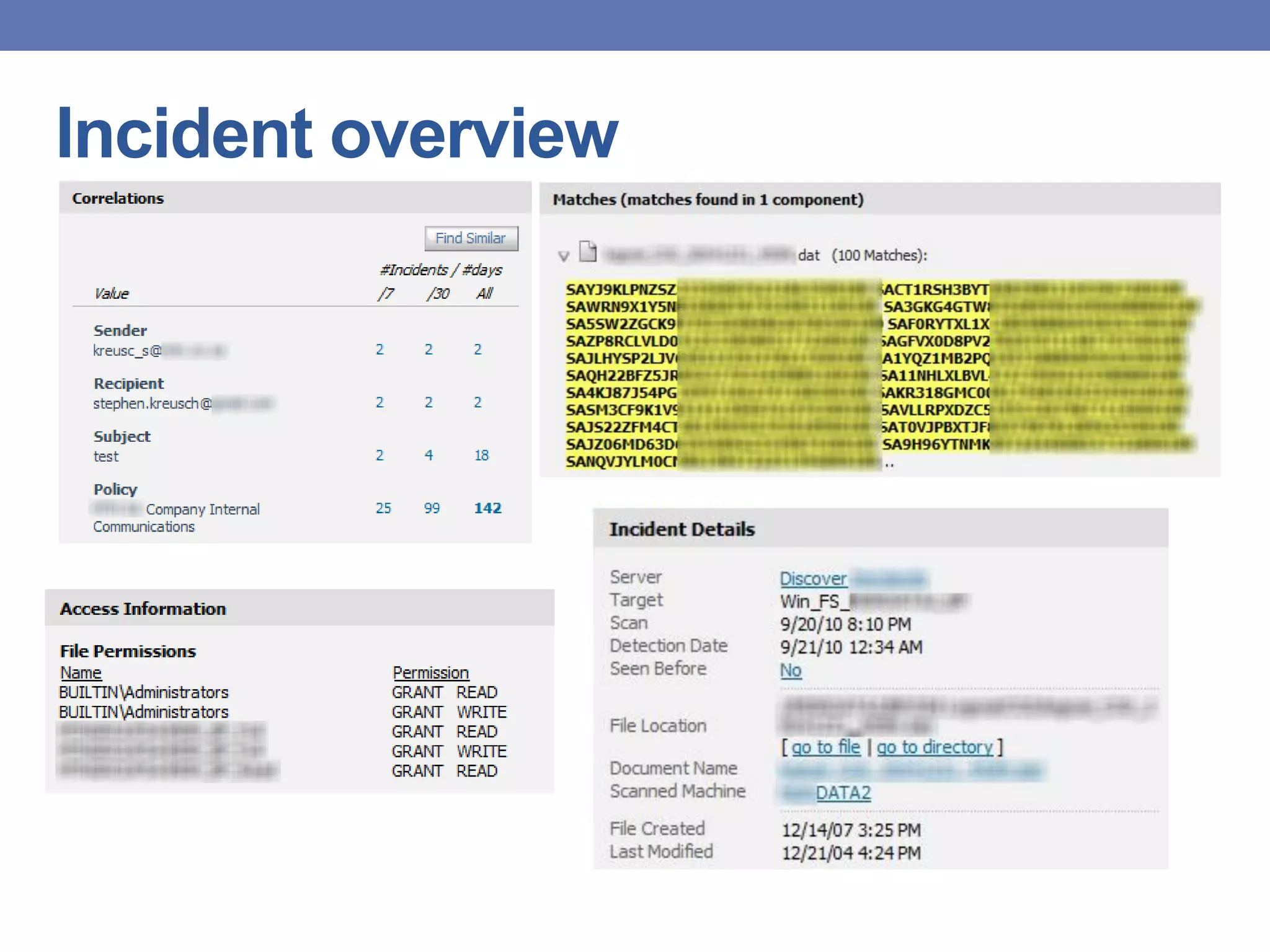
This document provides an overview of data loss prevention (DLP) systems. It defines DLP and describes how it can identify, monitor, and protect data in use, in motion, and at rest. It discusses typical DLP implementations for networks and endpoints/storage and how policies are defined. Common criticisms of DLP are outlined as well as the value it can provide by focusing on data security and improving communication between security and business teams. Lessons learned emphasize the importance of people, process, and technology in DLP deployments.