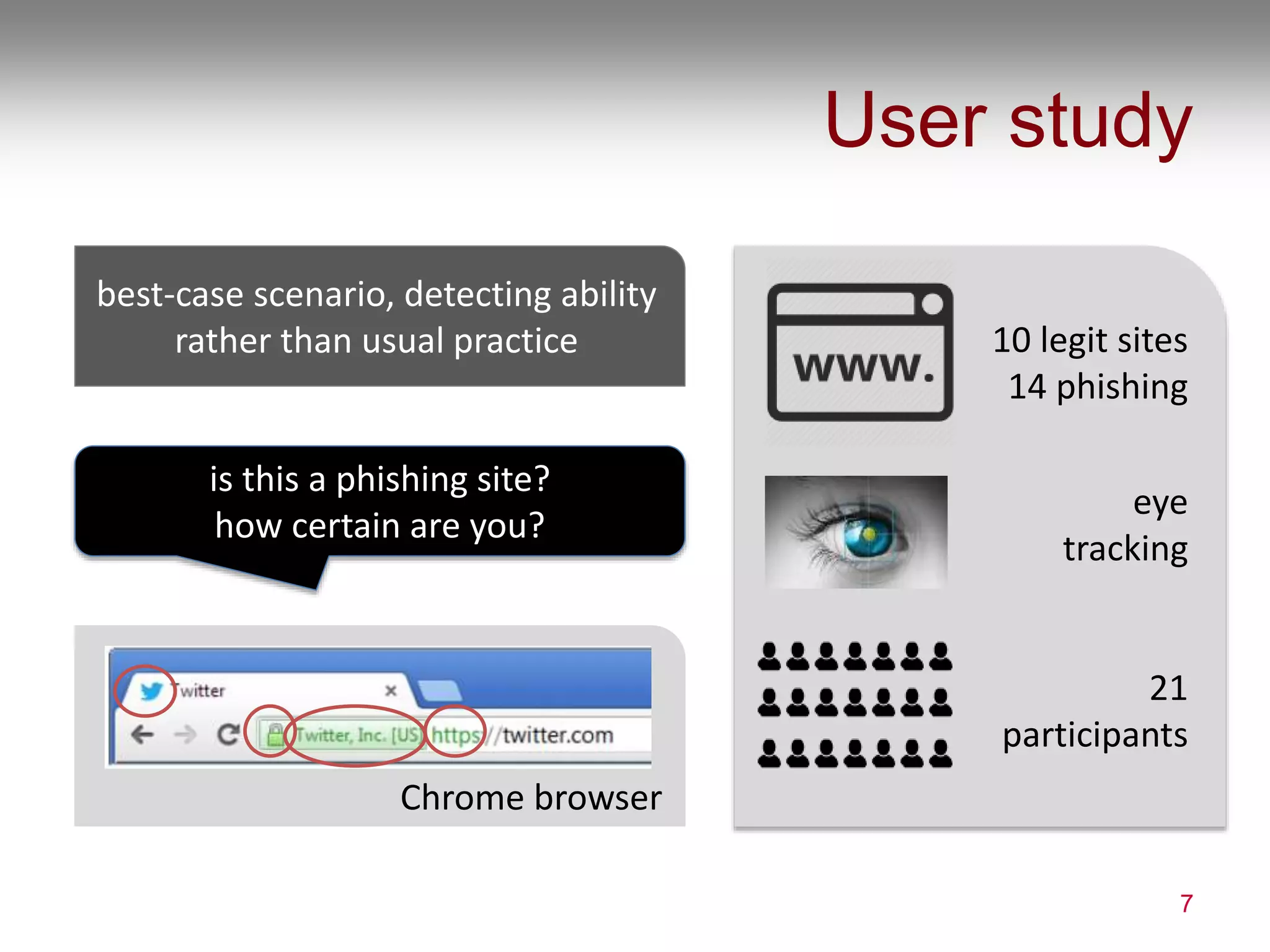
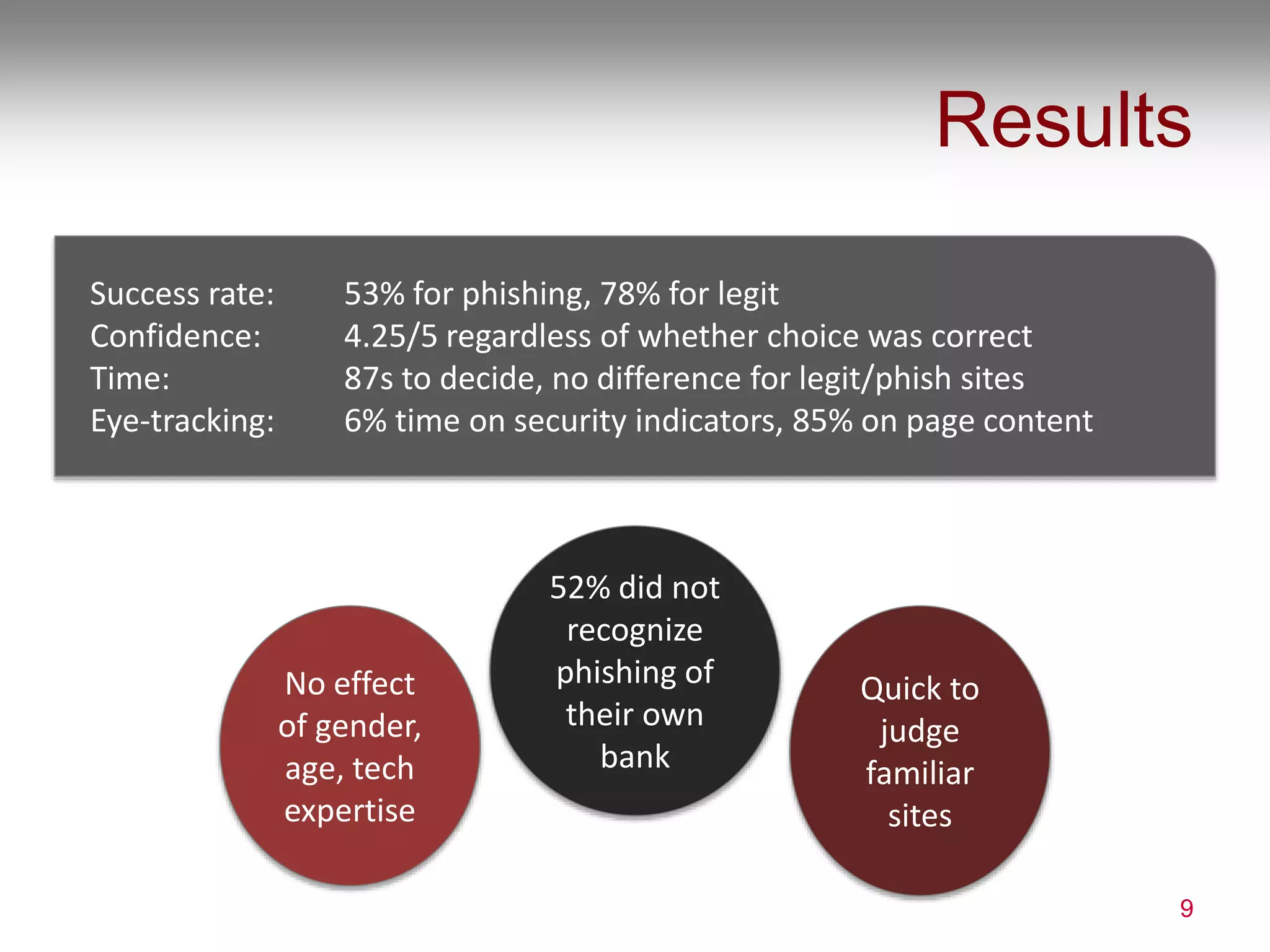
1) The document summarizes a user study on phishing detection that found users still struggle to accurately identify phishing sites, being successful only 53% of the time on phishing sites and 78% on legitimate sites.
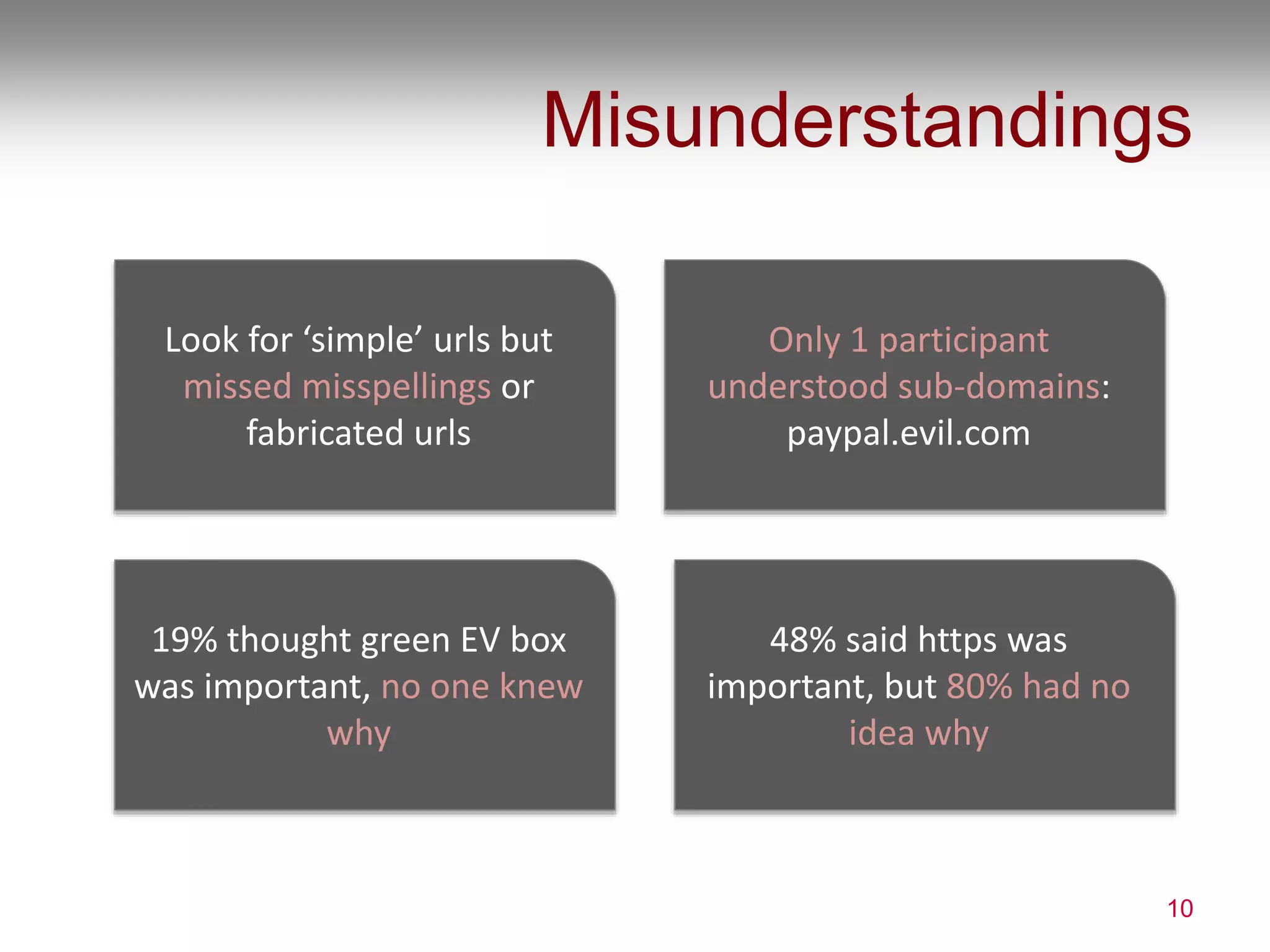
2) The study also found that users have only a shallow understanding of security indicators and place more attention on page content than security cues. Nearly half did not recognize a phishing version of their own bank site.
3) The presentation argues that common password policies may do more harm than good by placing unreasonable demands on human memory and behavior. It suggests rethinking such policies and advice to consider human capabilities and provide more practical and beneficial guidance.