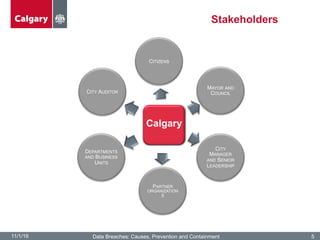
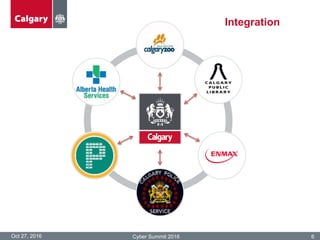
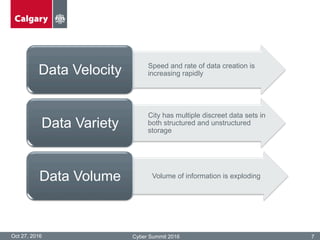
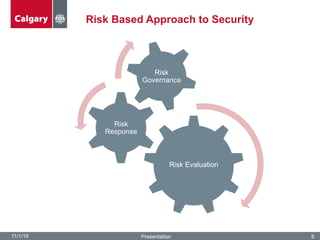
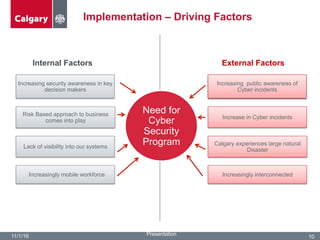
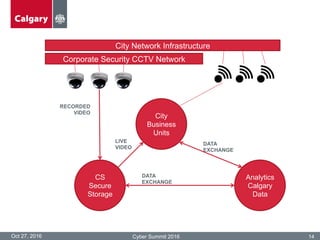
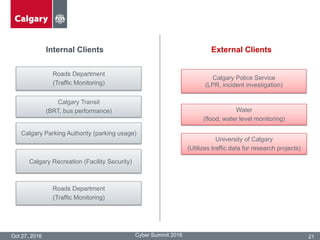
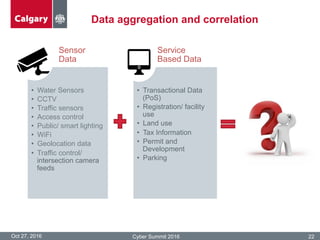
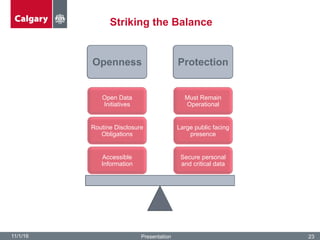
The City of Calgary's Corporate Security outlines the significant challenges and solutions related to data security, emphasizing the need for innovative risk management and integration of physical and cyber security measures. Key points include the rapid increase in data creation and the deployment of surveillance systems to enhance public safety while balancing privacy concerns. The document highlighted the strategies for effective monitoring, data protection, and the importance of adhering to legal privacy standards.