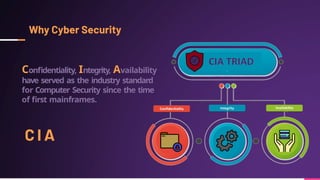
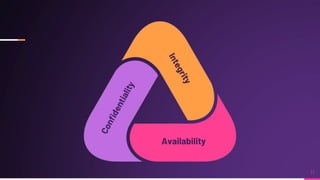
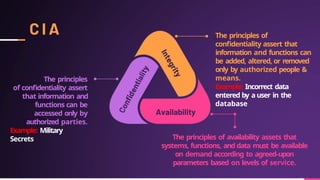
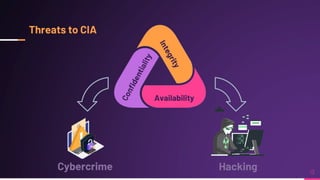
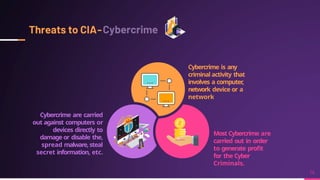
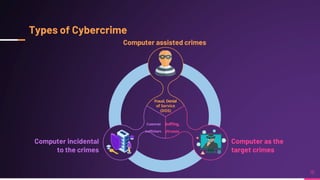
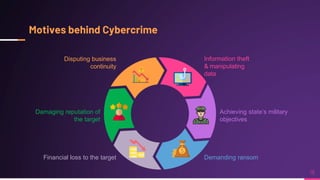
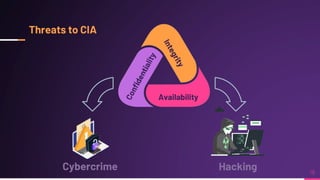
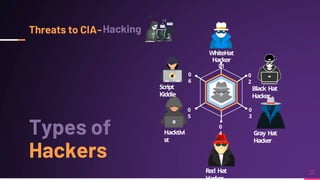
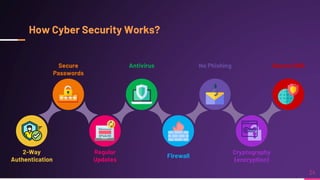
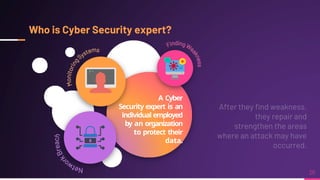
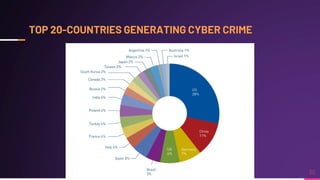
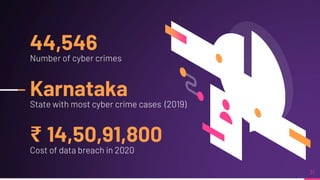
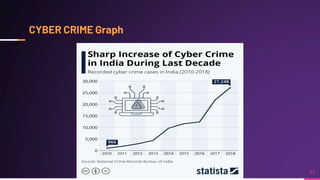
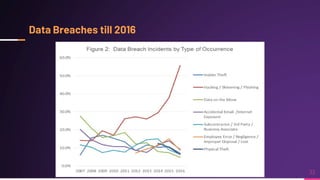
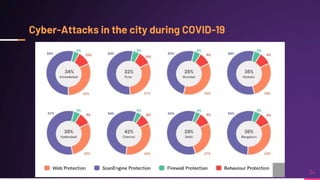
Cyber security involves protecting networks and devices from attacks and unauthorized access to ensure confidentiality, integrity, and availability of information. Cybercrime encompasses illegal activities using computers or networks, often for profit, including fraud, malware dissemination, and data theft. Cybersecurity experts are critical in safeguarding organizations against these threats.