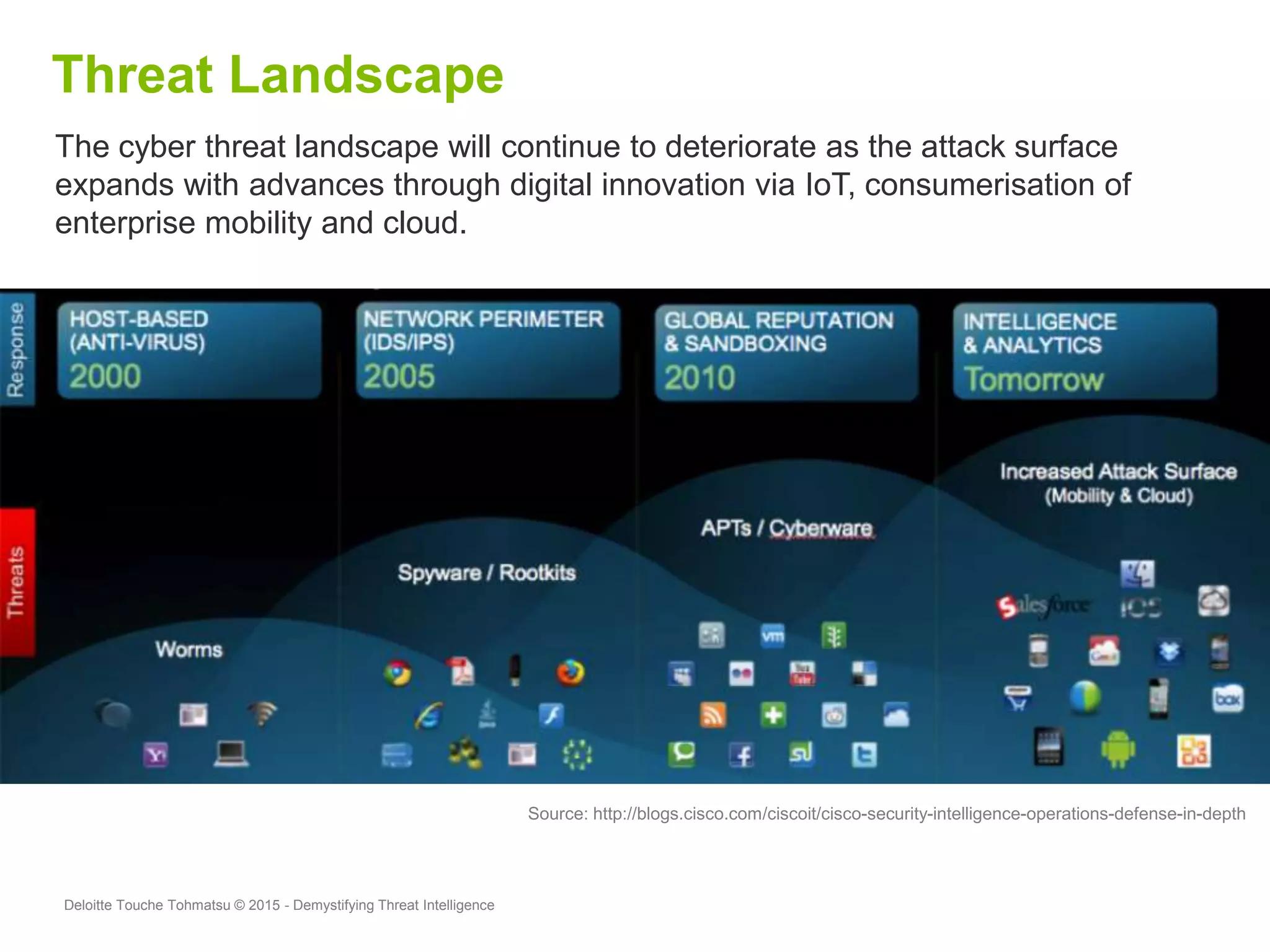
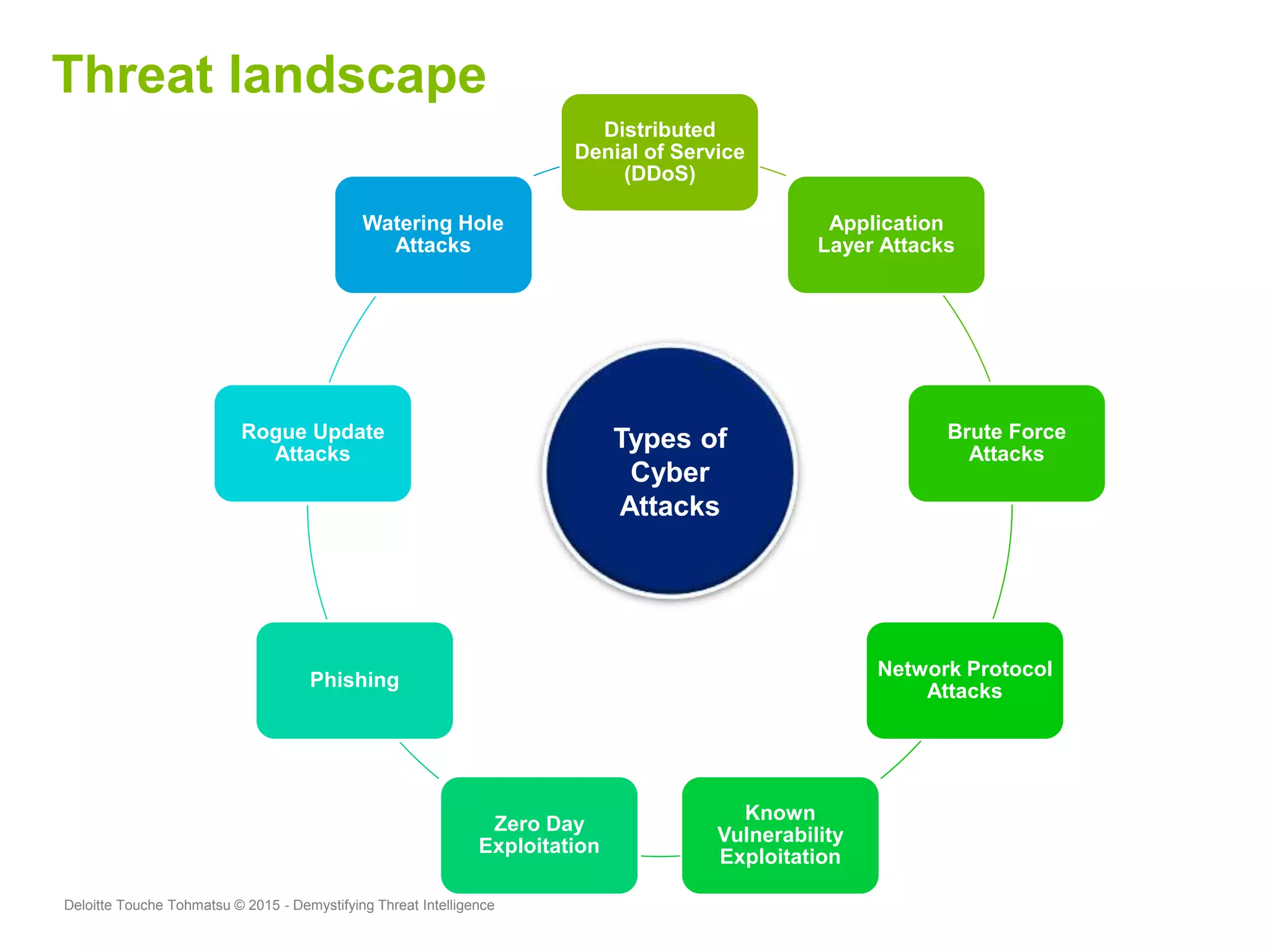
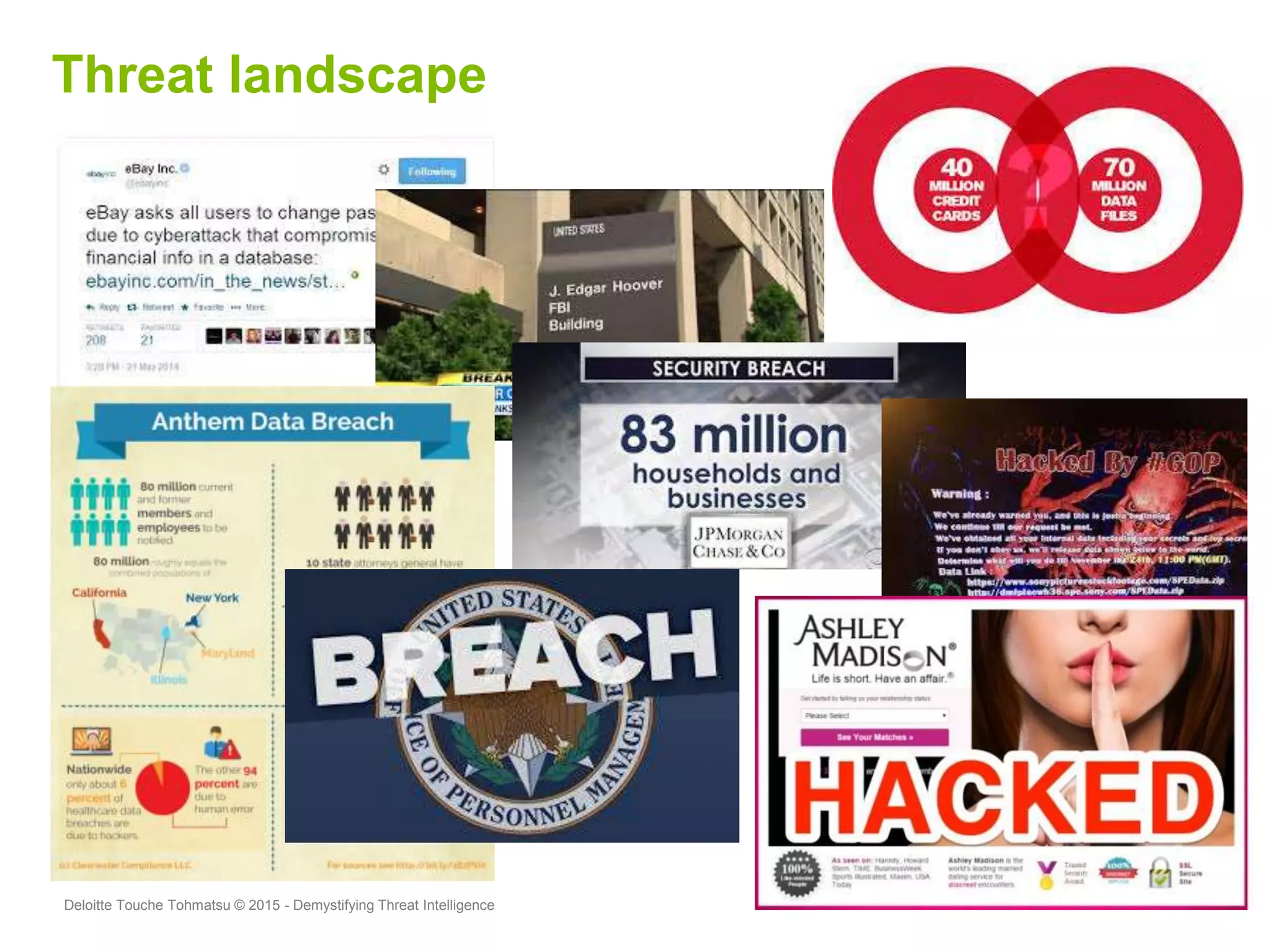
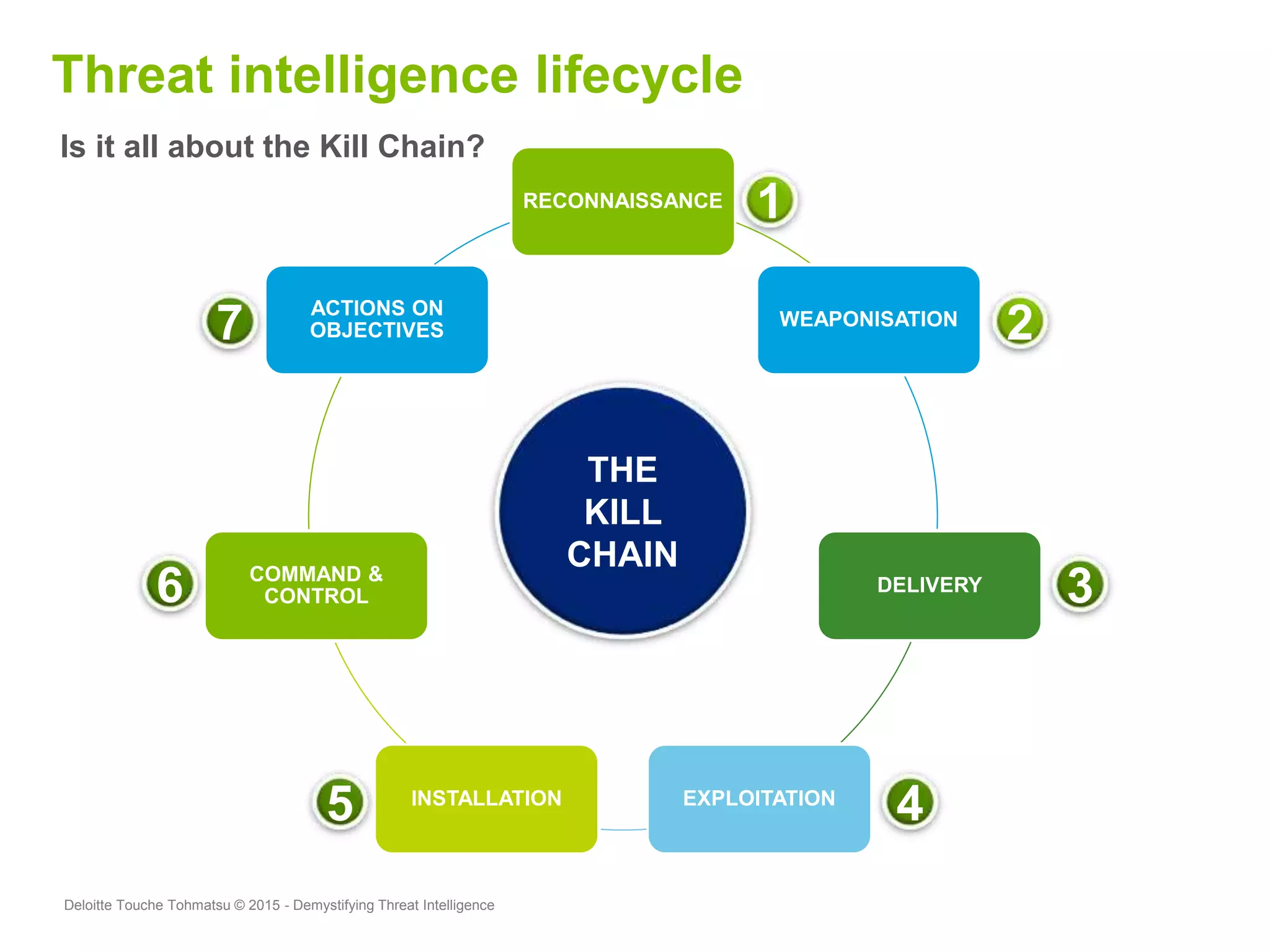
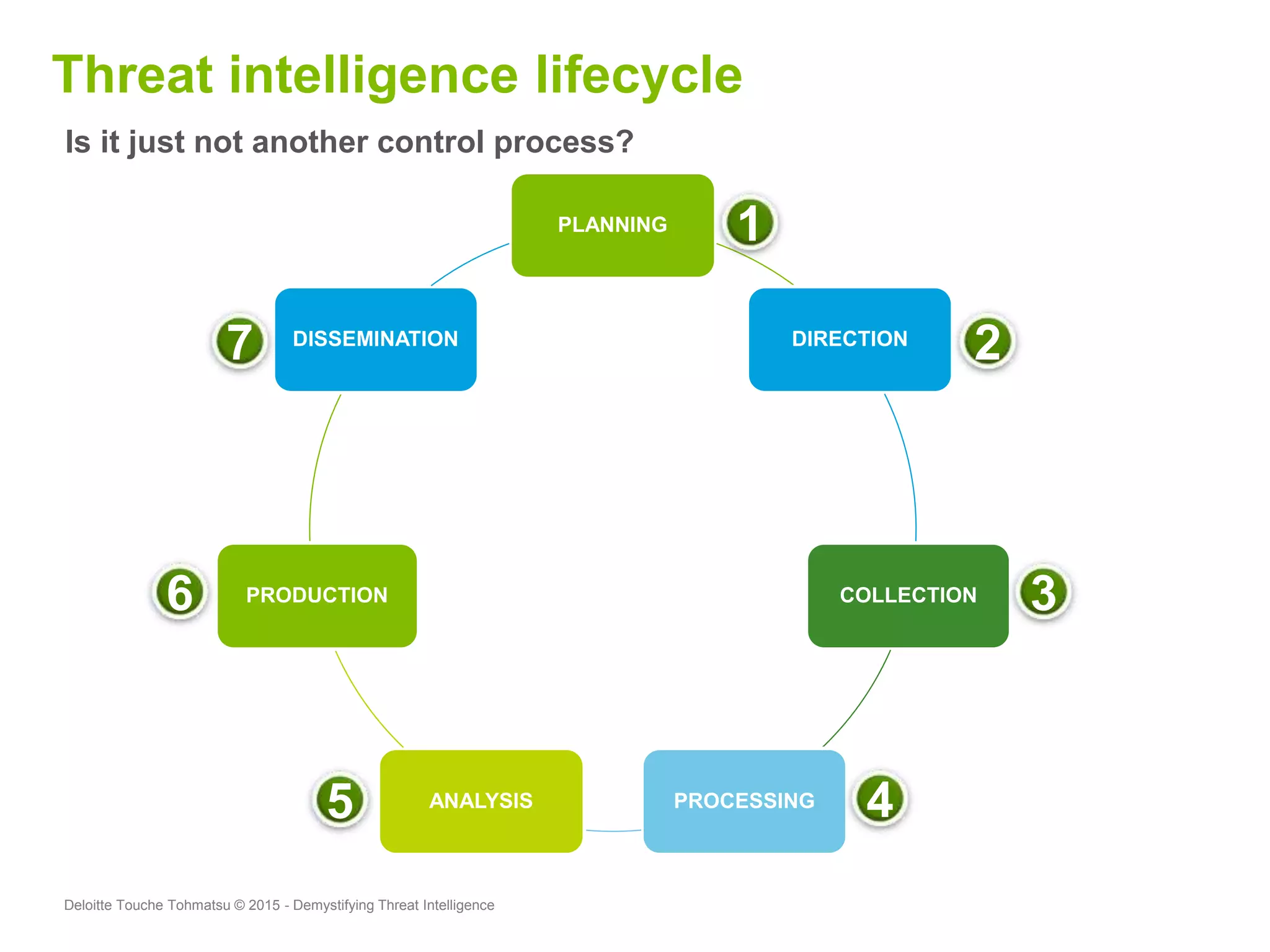
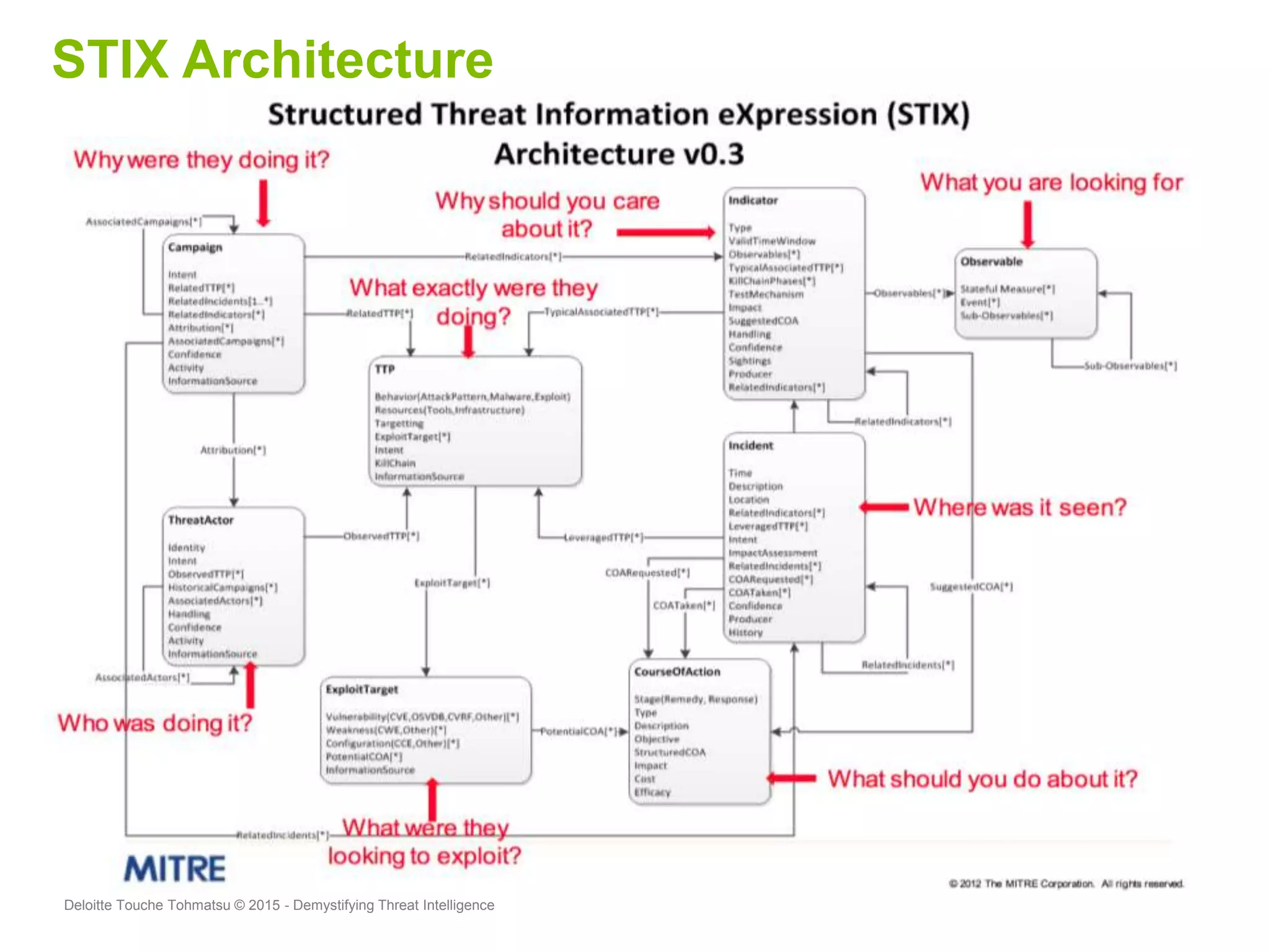
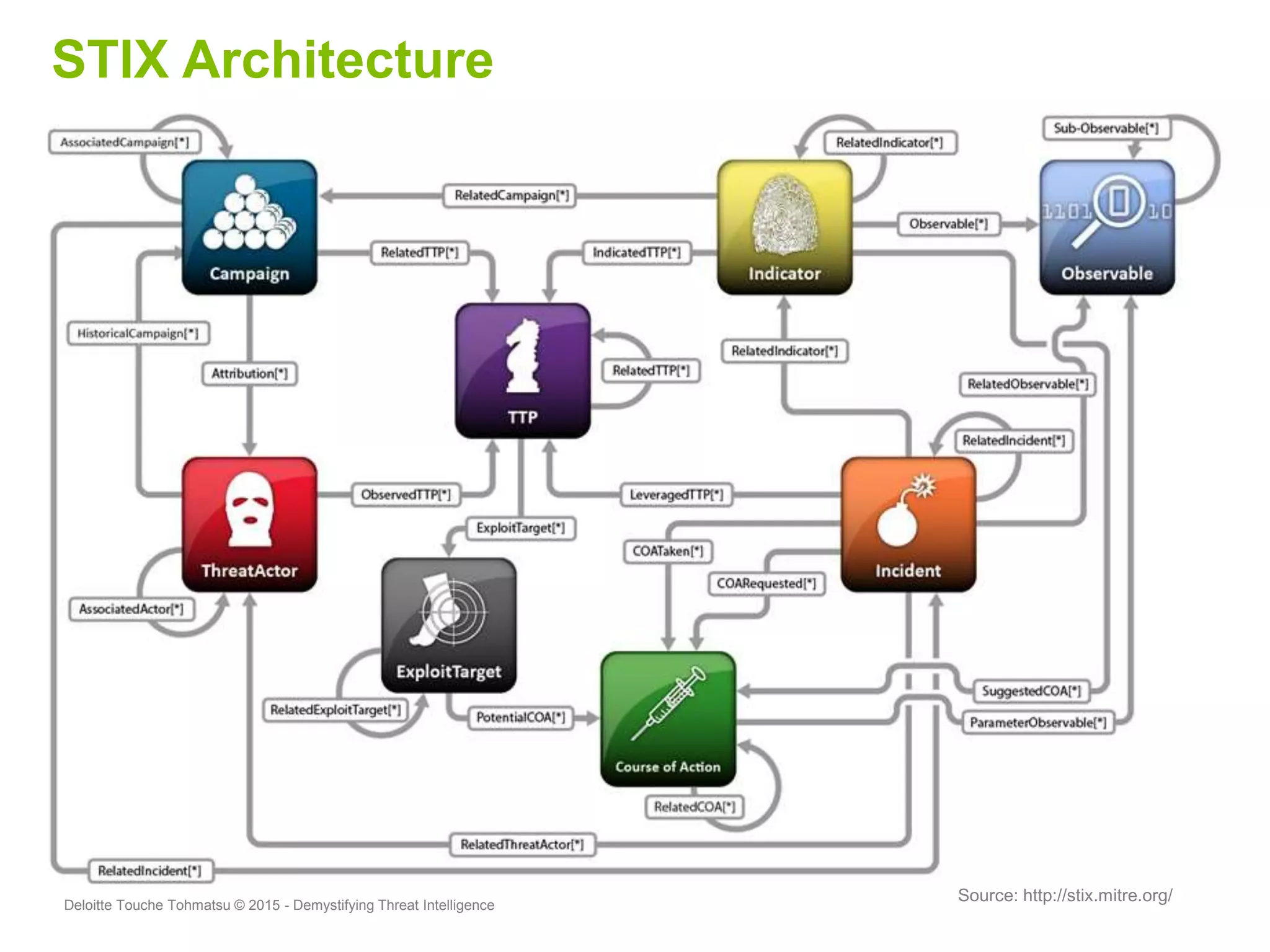
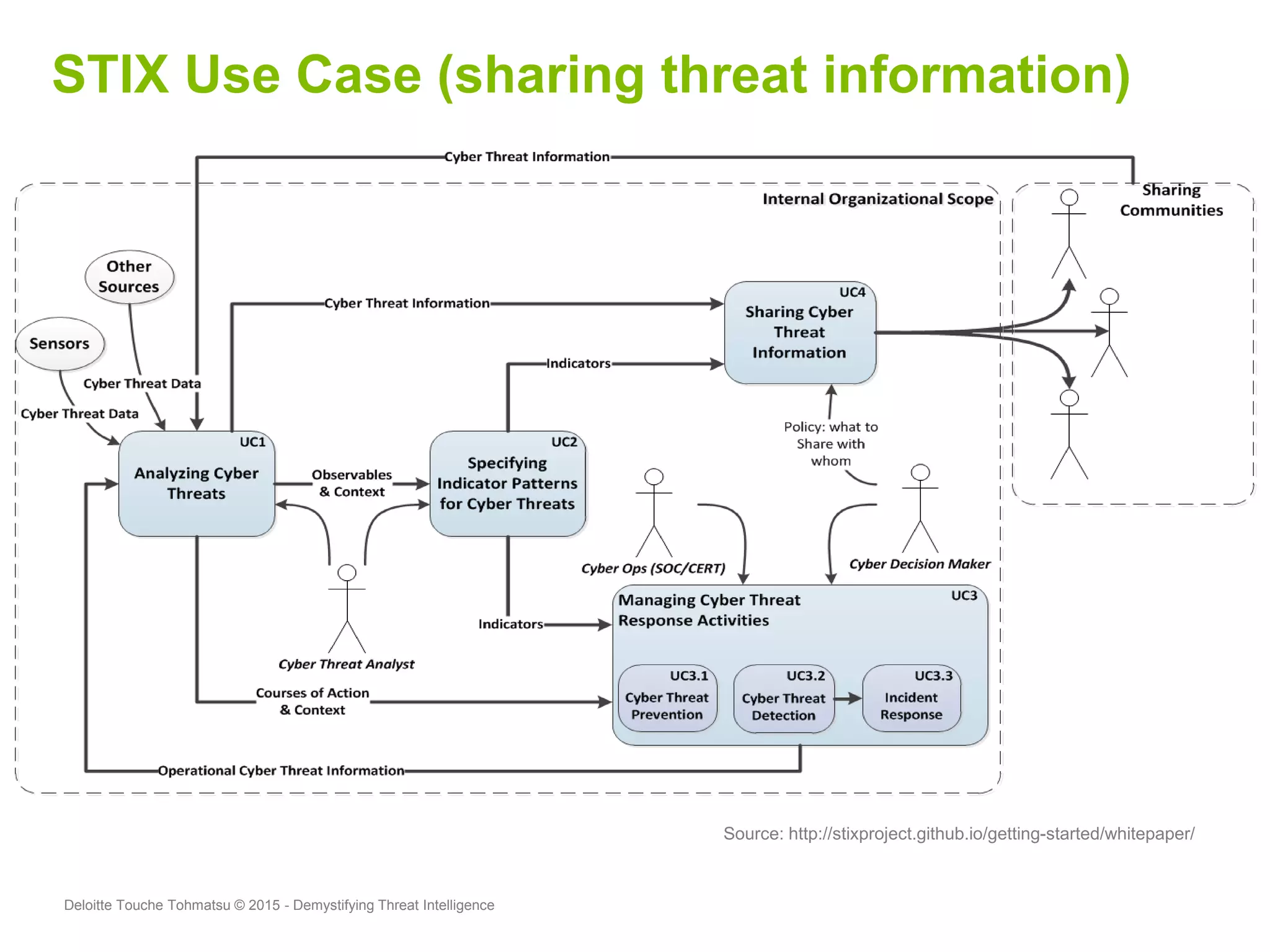
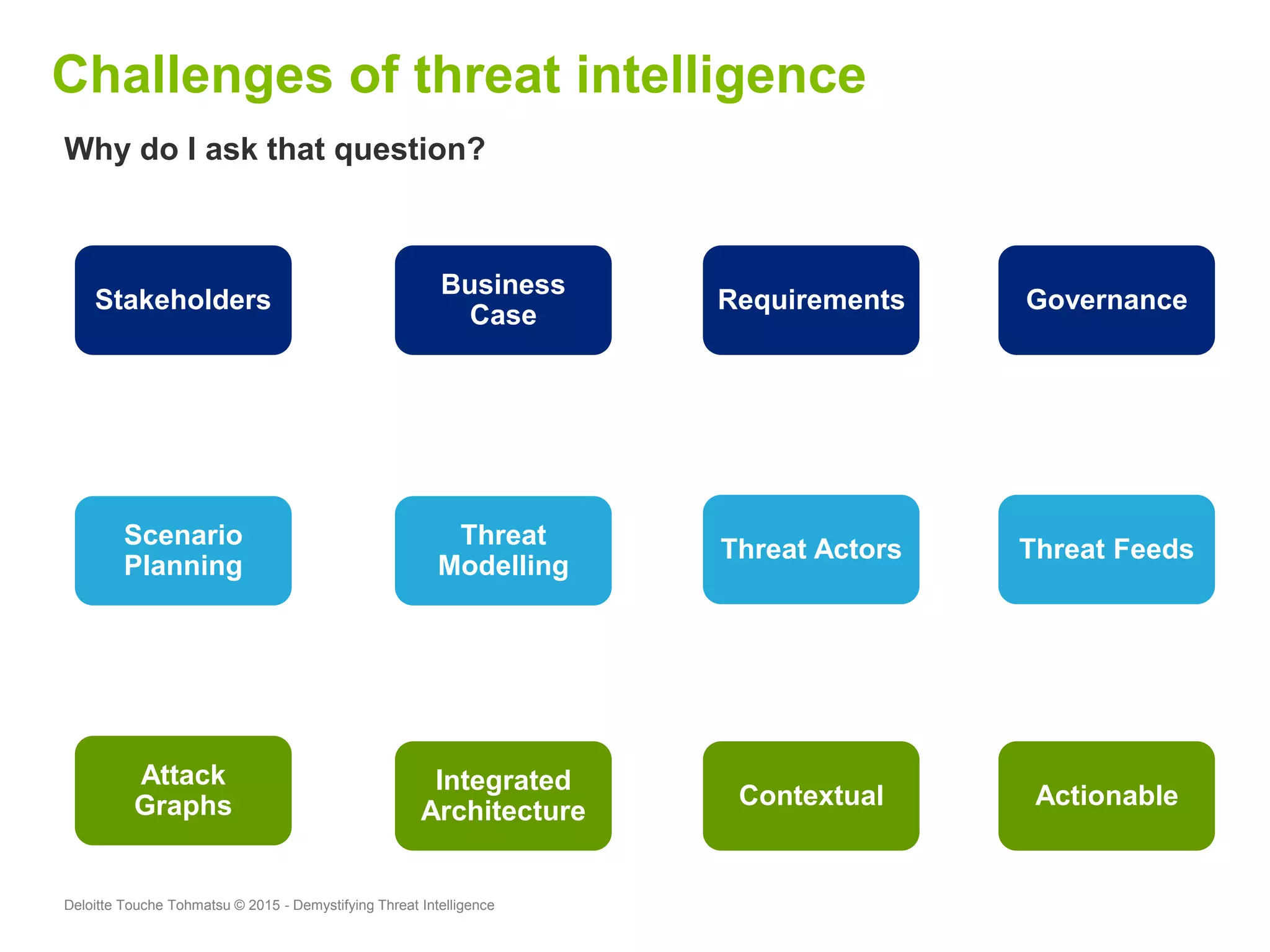
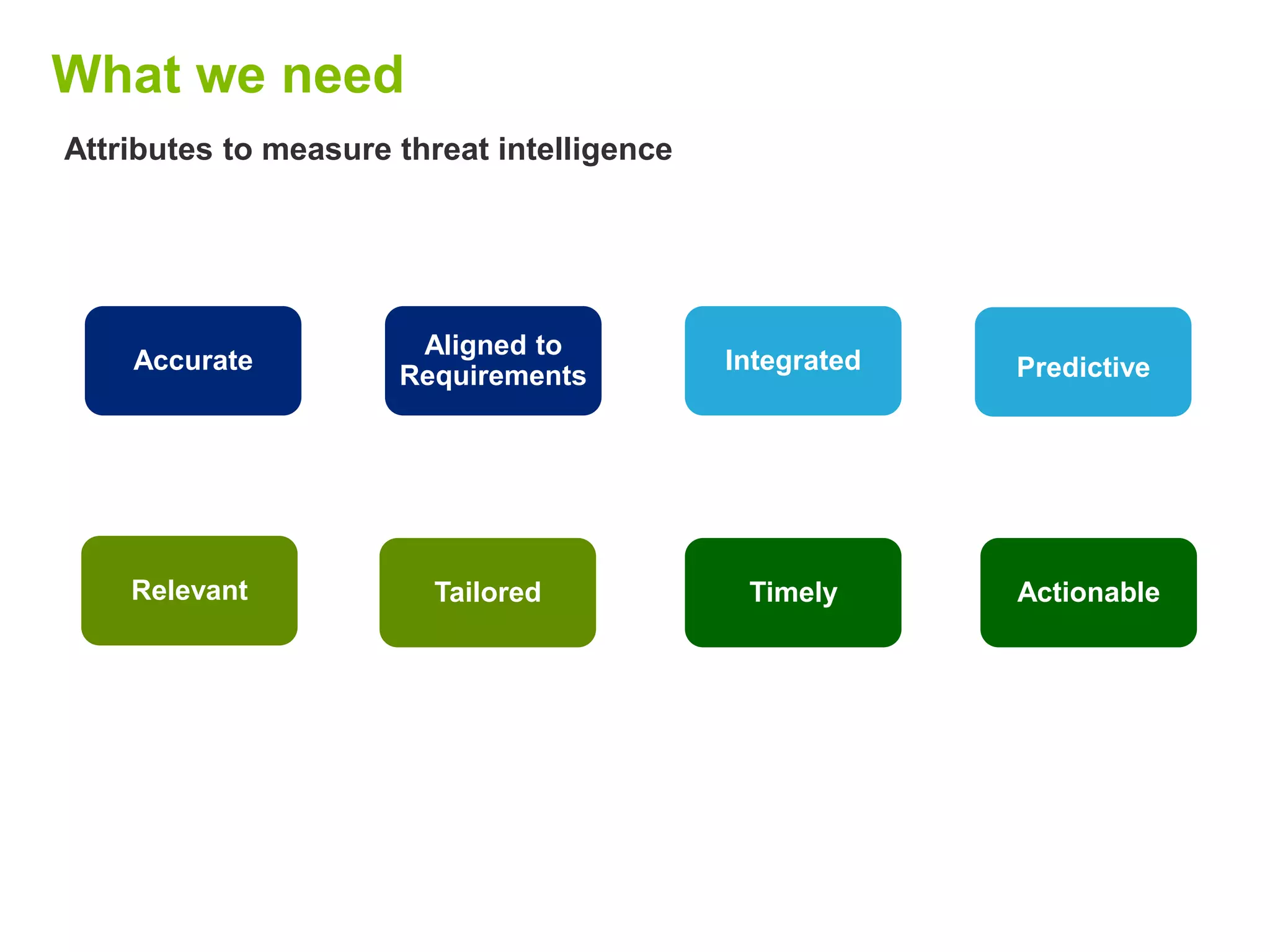
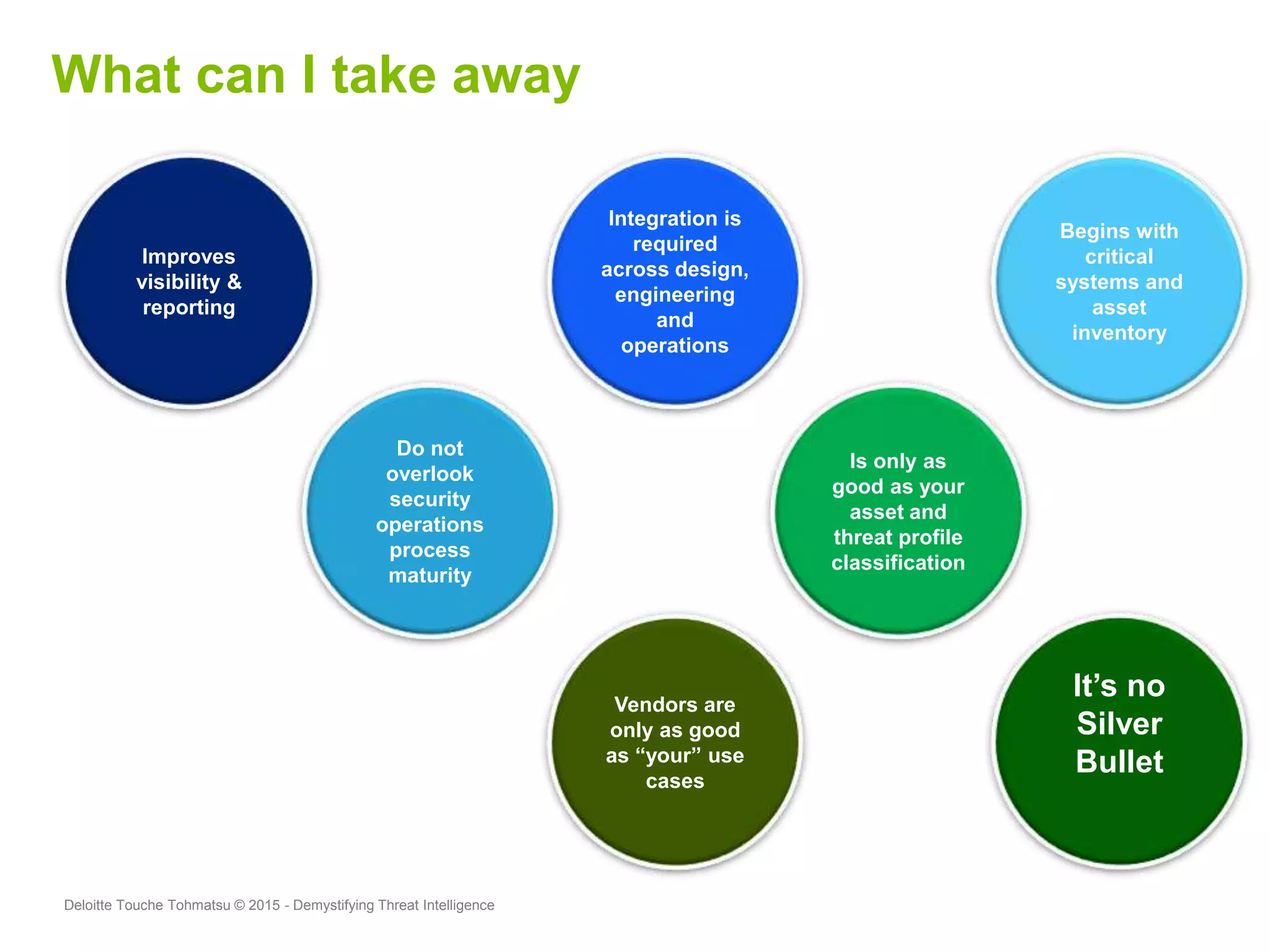
Puneet Kukreja of Deloitte gave a presentation at the ISF's 26th Annual World Congress on implementing threat intelligence systems. He discussed defining threat intelligence, the threat landscape facing organizations, and challenges in threat intelligence. Kukreja also covered the threat intelligence lifecycle, standards like STIX and TAXII, using cases studies and attributes to measure threat intelligence effectiveness. The presentation emphasized that threat intelligence requires integration across security operations and is one part of an overall security strategy.