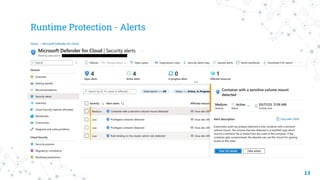
Microsoft Defender for Containers provides security for container workloads running on Kubernetes. It monitors clusters for misconfigurations and vulnerabilities, provides runtime threat detection, and generates alerts. It works across multiple clouds by deploying agents and daemons to collect security signals from the API server, nodes, and images. A demonstration showed Microsoft Defender in action monitoring container workloads.








![Environment Hardening
9
◎ Continuous monitoring of your Kubernetes clusters
○ Wherever they're hosted [AWS - EKS, Azure - AKS, GCP - GKE, On-Premise (using
ARC)]
○ Continuously assess clusters to provide visibility of misconfigurations
○ Provide Guidelines to mitigate the issues
◎ Kubernetes data plane hardening
○ Azure Policy add on
◉ Extends Gatekeeper v3, required to apply at-scale auditing, enforcements and
safeguards on clusters in a centralized, consistent manner.
○ Defender Daemonset
◉ Deployed to each worker node, collects security-related data and sends it to
Defender for analysis. Required for runtime protections and security
capabilities](https://image.slidesharecdn.com/container-security-using-msft-defender-230320050142-e998ab46/85/Container-Security-Using-Microsoft-Defender-9-320.jpg)



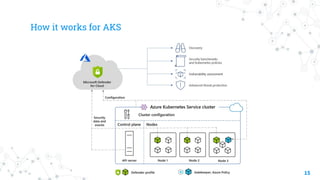
![How it works
14
◎ Defender for Containers receives and analyzes:
○ Audit logs and security events from the API server
○ Cluster configuration information from the control plane
○ Workload configuration from Azure Policy
○ Security signals and events from the node level
◎ Components deployed
○ Azure Policy add on
◉ Extends Gatekeeper v3, required to apply at-scale auditing, enforcements and
safeguards on clusters in a centralized, consistent manner. [azure-policy,
azure-policy-webhook]
○ Defender Profile Daemonset
◉ Deployed to each node provides the runtime protections and collects signals
from nodes using eBPF technology. [Microsoft-defender-collector-ds,
microsoft-defender-publisher-ds, microsoft-defender-collector-misc]](https://image.slidesharecdn.com/container-security-using-msft-defender-230320050142-e998ab46/85/Container-Security-Using-Microsoft-Defender-14-320.jpg)