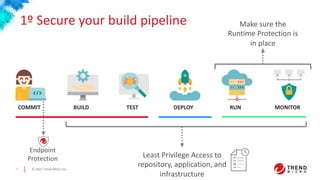
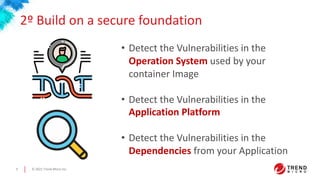
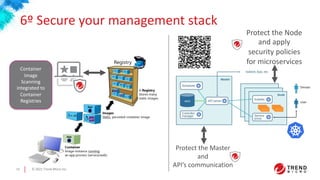
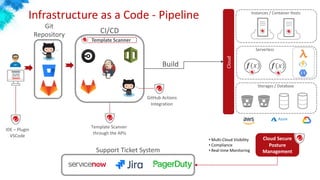
This document discusses container and Kubernetes security. It notes that Gartner predicts more than 75% of organizations will be running containerized applications by 2022. It outlines some recent Kubernetes vulnerabilities and common container security concerns. It then provides recommendations for securing the build pipeline, building on a secure foundation, securing applications, securing container hosts, securing networking environments, and securing management stacks. It discusses how to validate infrastructure created or that will be created in the cloud for applications. It concludes that containers offer benefits if the right policies, practices, and security tools are used to protect against vulnerabilities and attacks.