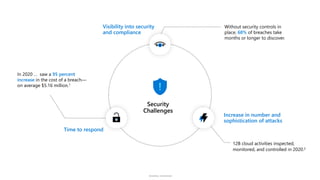
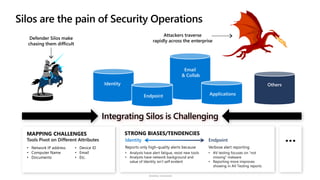
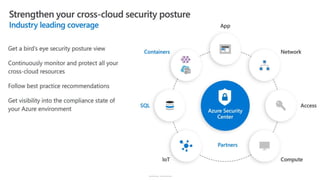
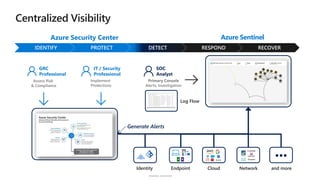
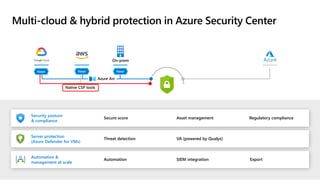
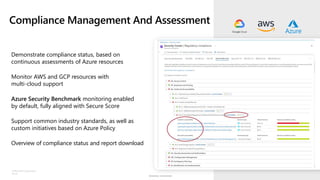
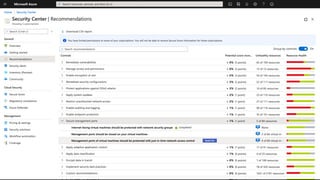
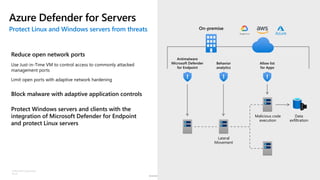
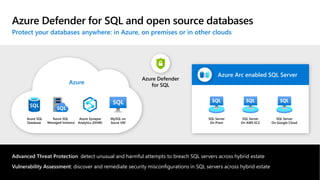
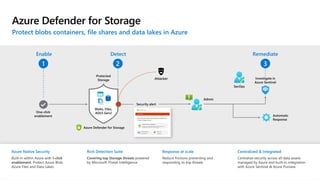
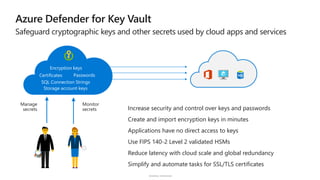
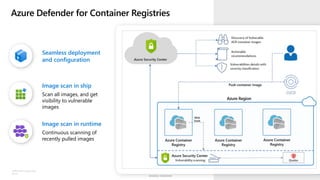
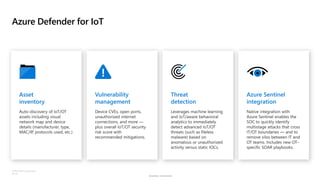
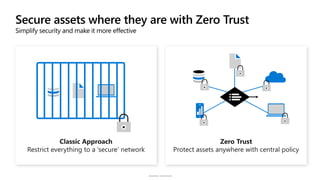
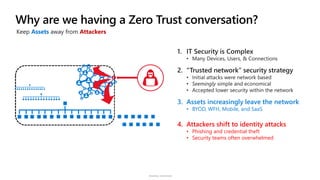
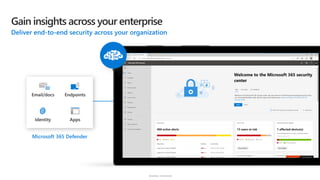
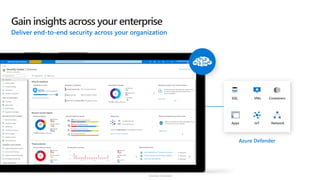
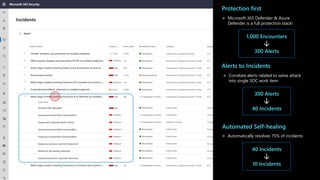
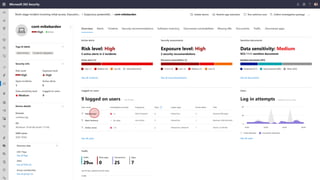
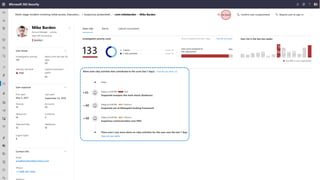
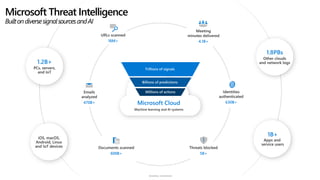
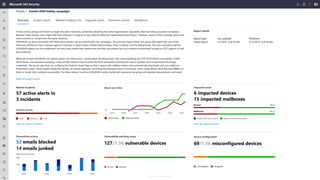
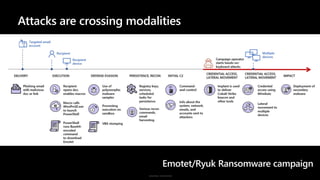
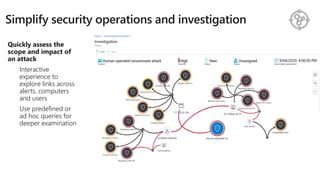
The document discusses security challenges and the increasing sophistication of cyberattacks, highlighting that 68% of breaches take months to discover, with the cost of a breach averaging $5.16 million. It outlines Azure's security offerings, including tools for monitoring, compliance, and protection across various environments such as on-premise and cloud. It emphasizes the importance of integrating security silos and adopting a zero trust approach, particularly due to the shift towards identity attacks and remote work.