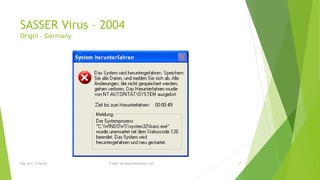
Computer viruses have existed since the late 1980s, beginning with the Brain virus created in Pakistan in 1986. Viruses spread primarily through floppy disks in the early years. Over time, viruses increased in sophistication and ability to spread over networks and email. Some notable early viruses include Michelangelo in 1991, which overwrote data on March 6th, and ILOVEYOU in 2000, one of the first major email viruses. Viruses continue to evolve with different transmission methods as technology changes.