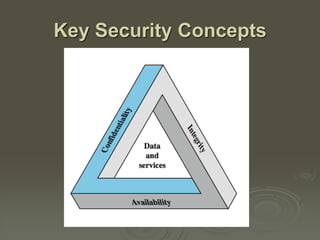
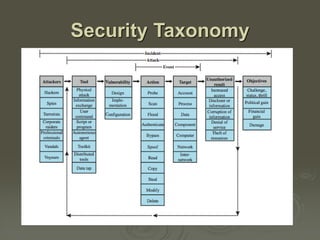
The document provides an overview of computer security principles and practices, emphasizing the importance of protecting information system resources to maintain integrity, availability, and confidentiality. It outlines key security challenges, types of attacks, countermeasures, and the necessity for regular monitoring and risk management. Additionally, it discusses security requirements, architecture, and strategies to ensure effective management of computer security.