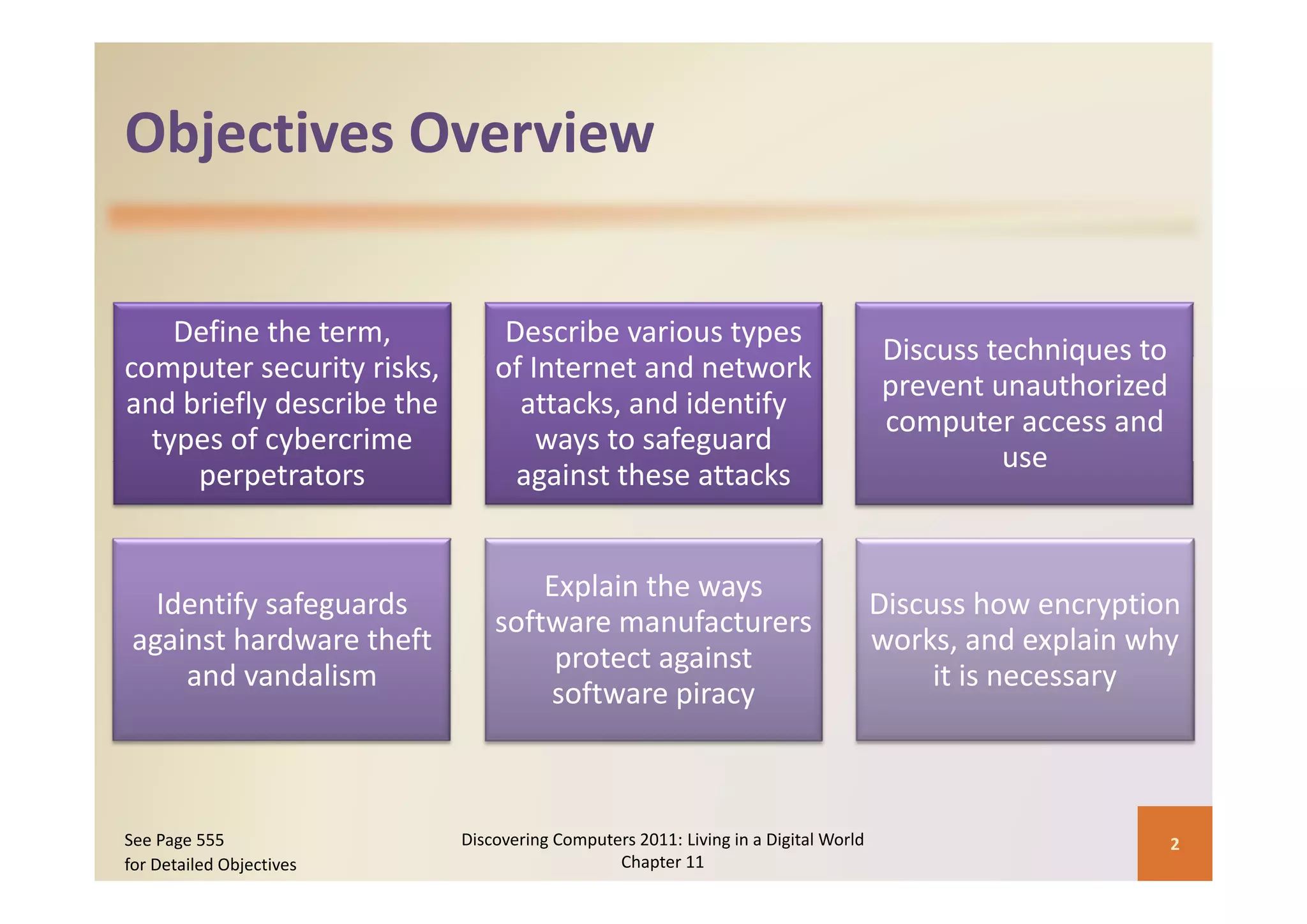
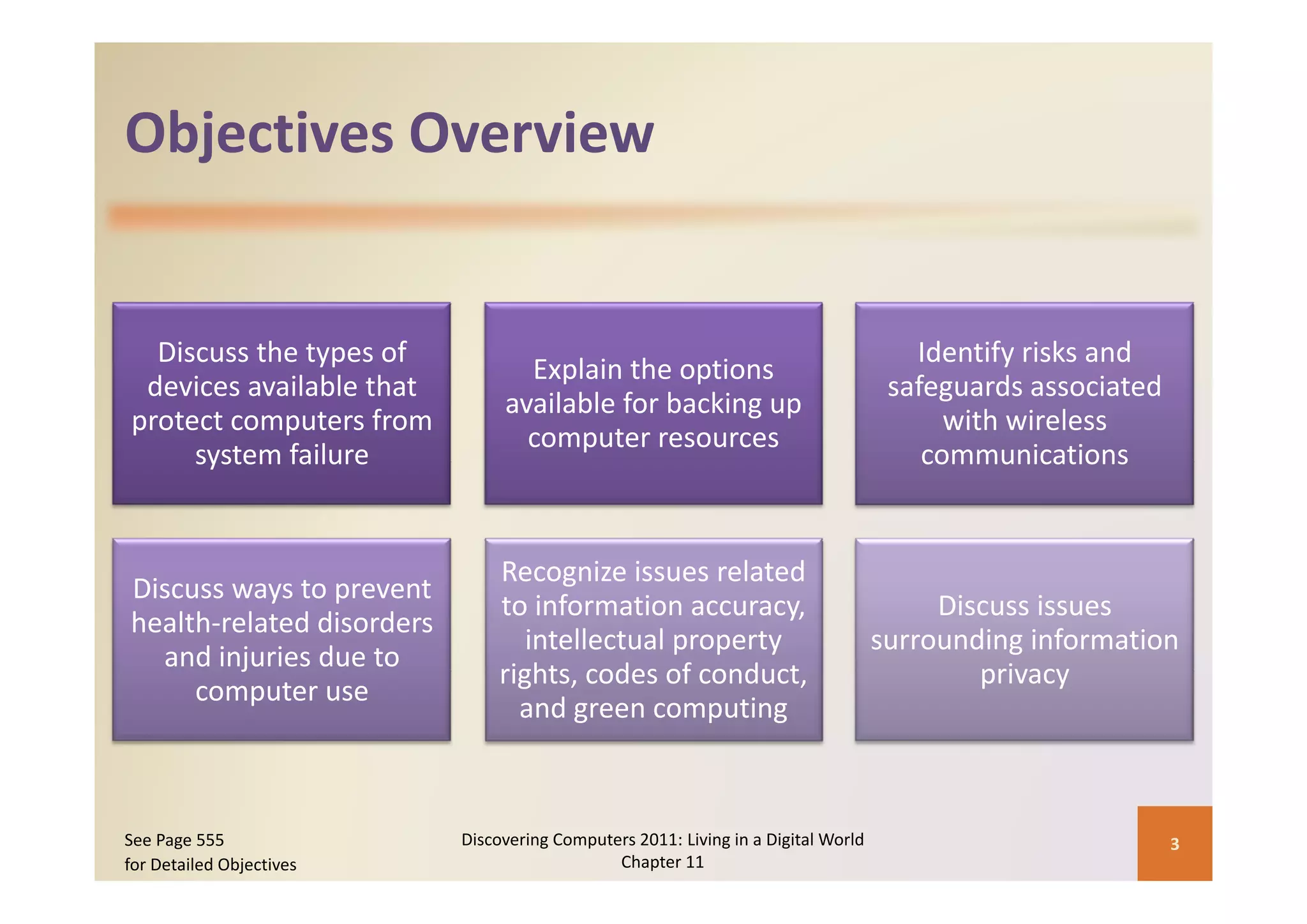
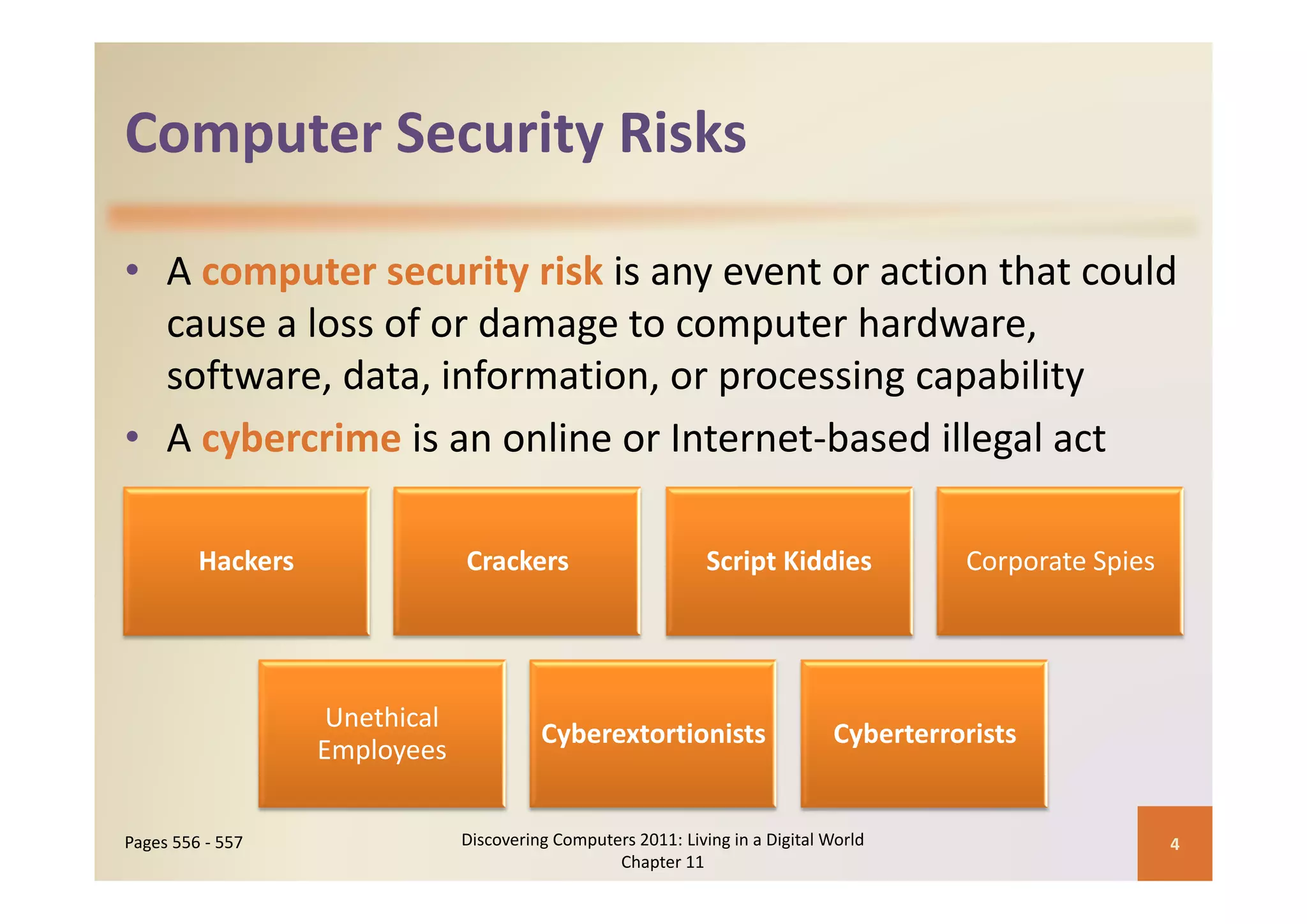
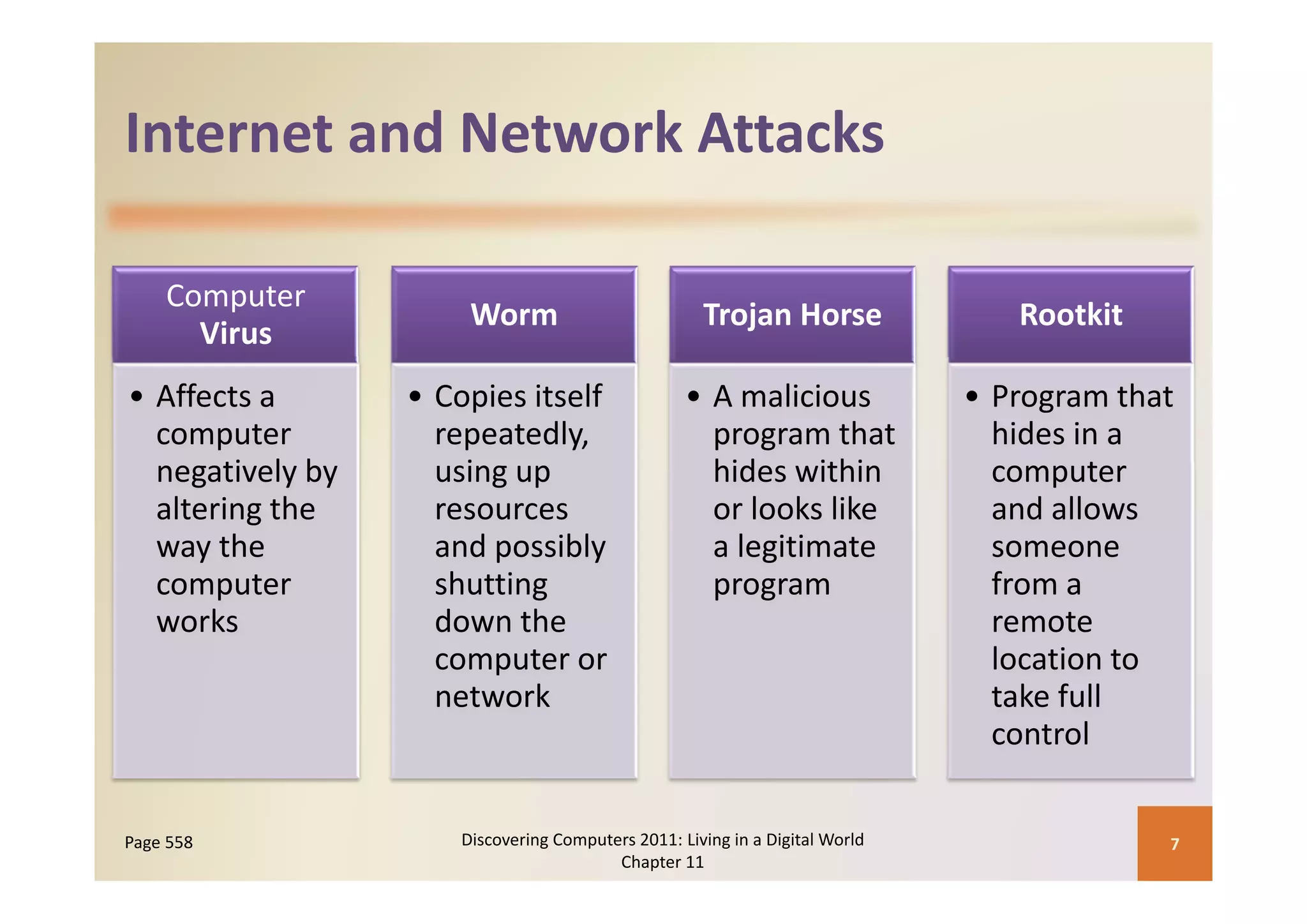
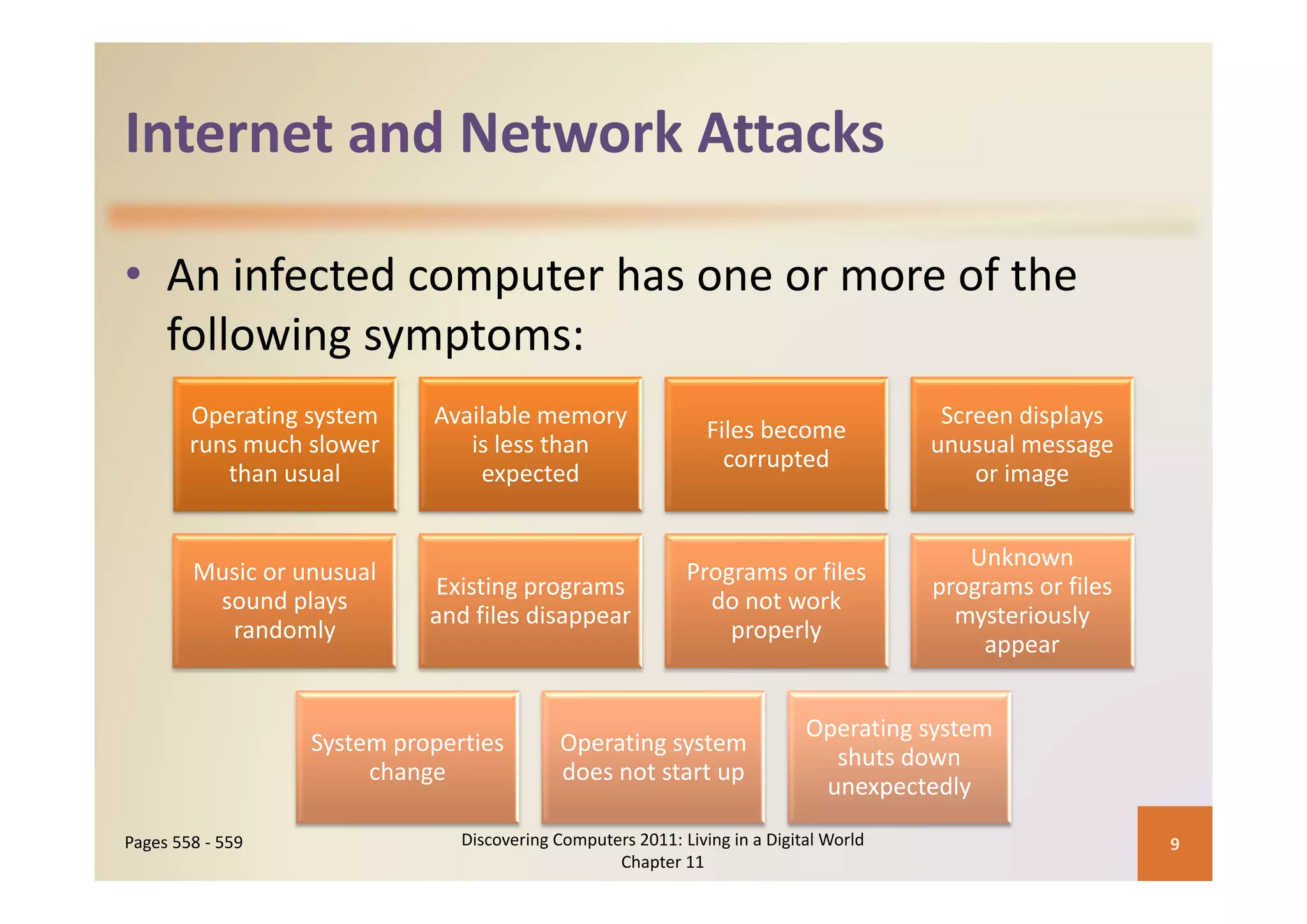
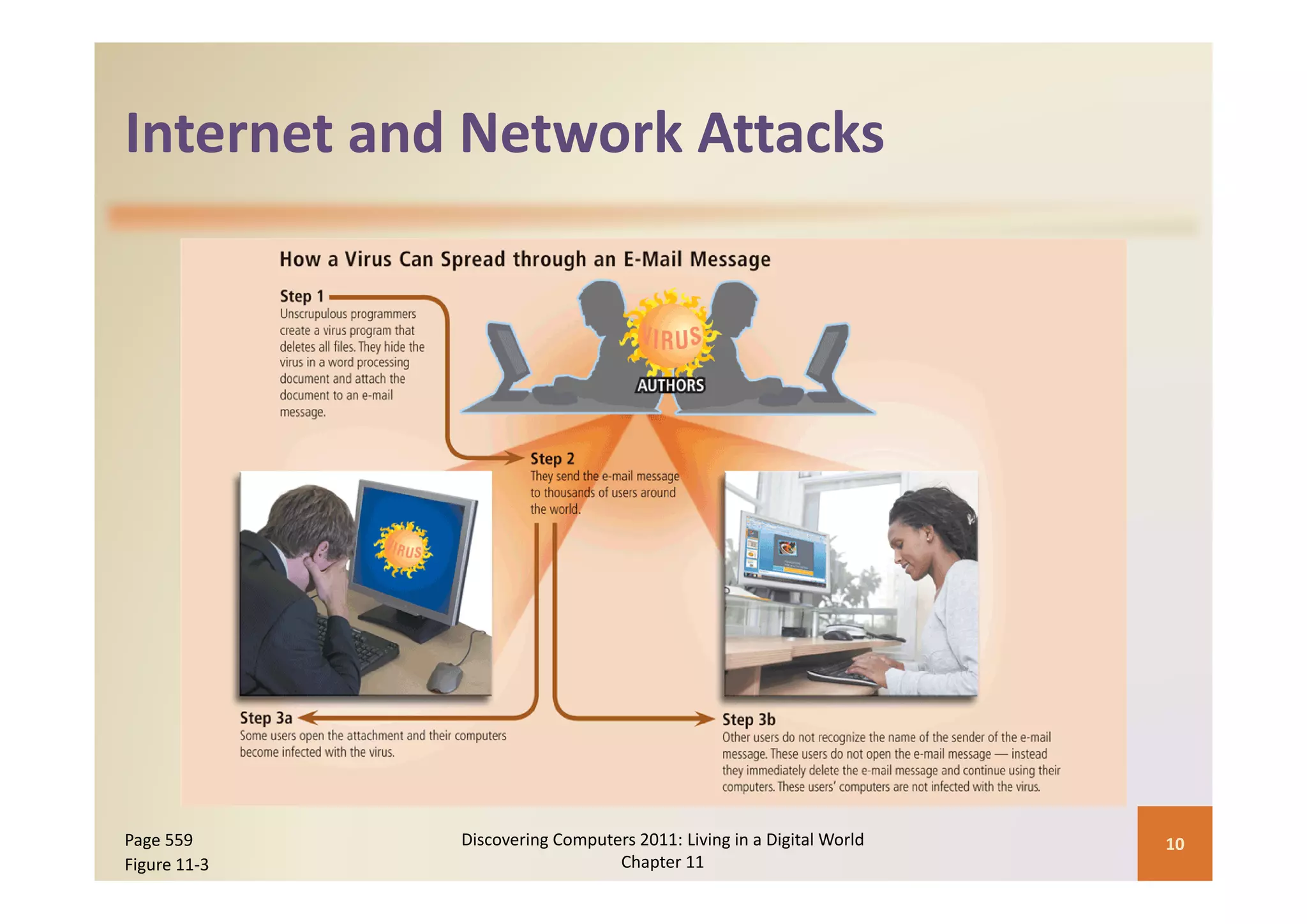
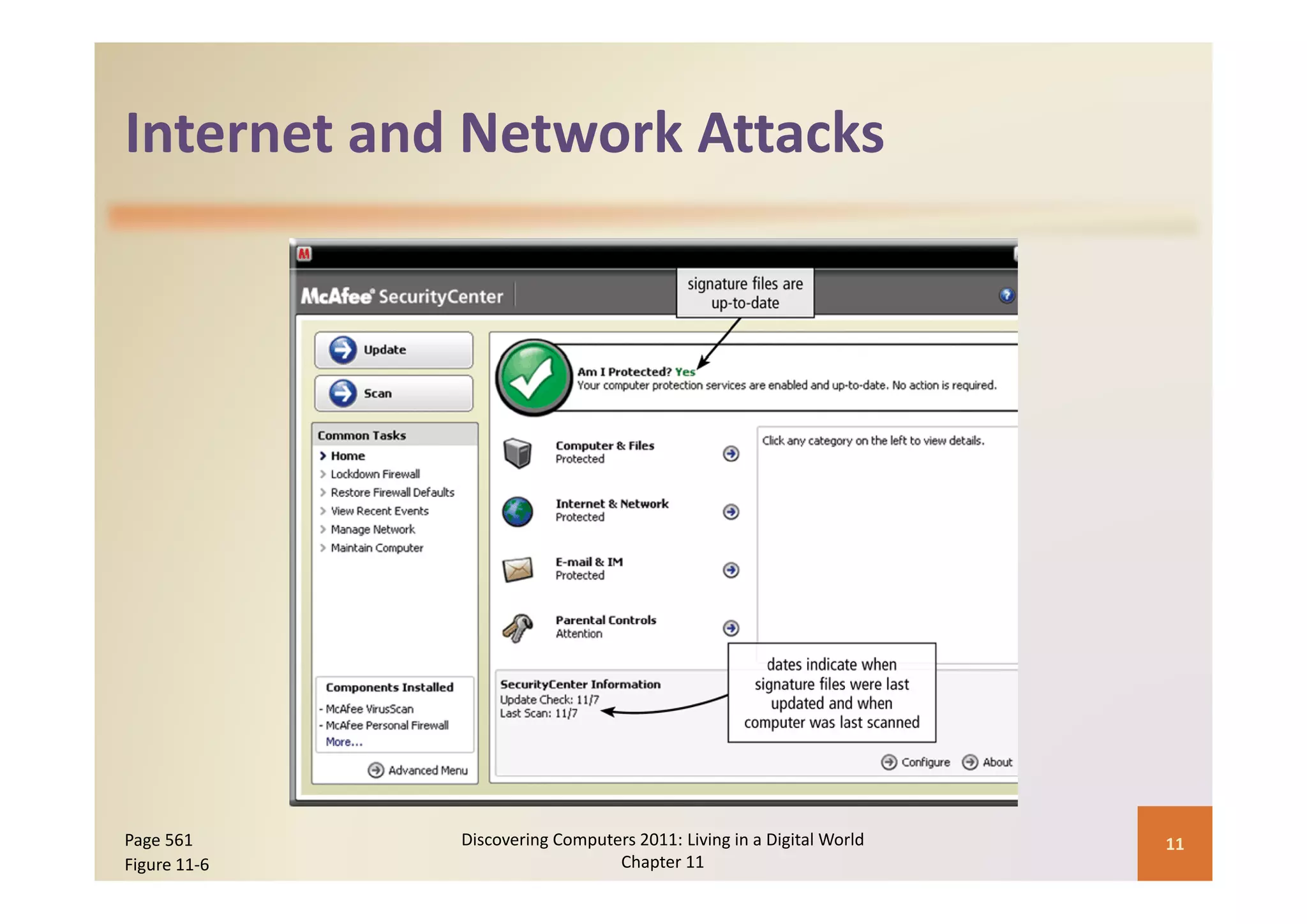
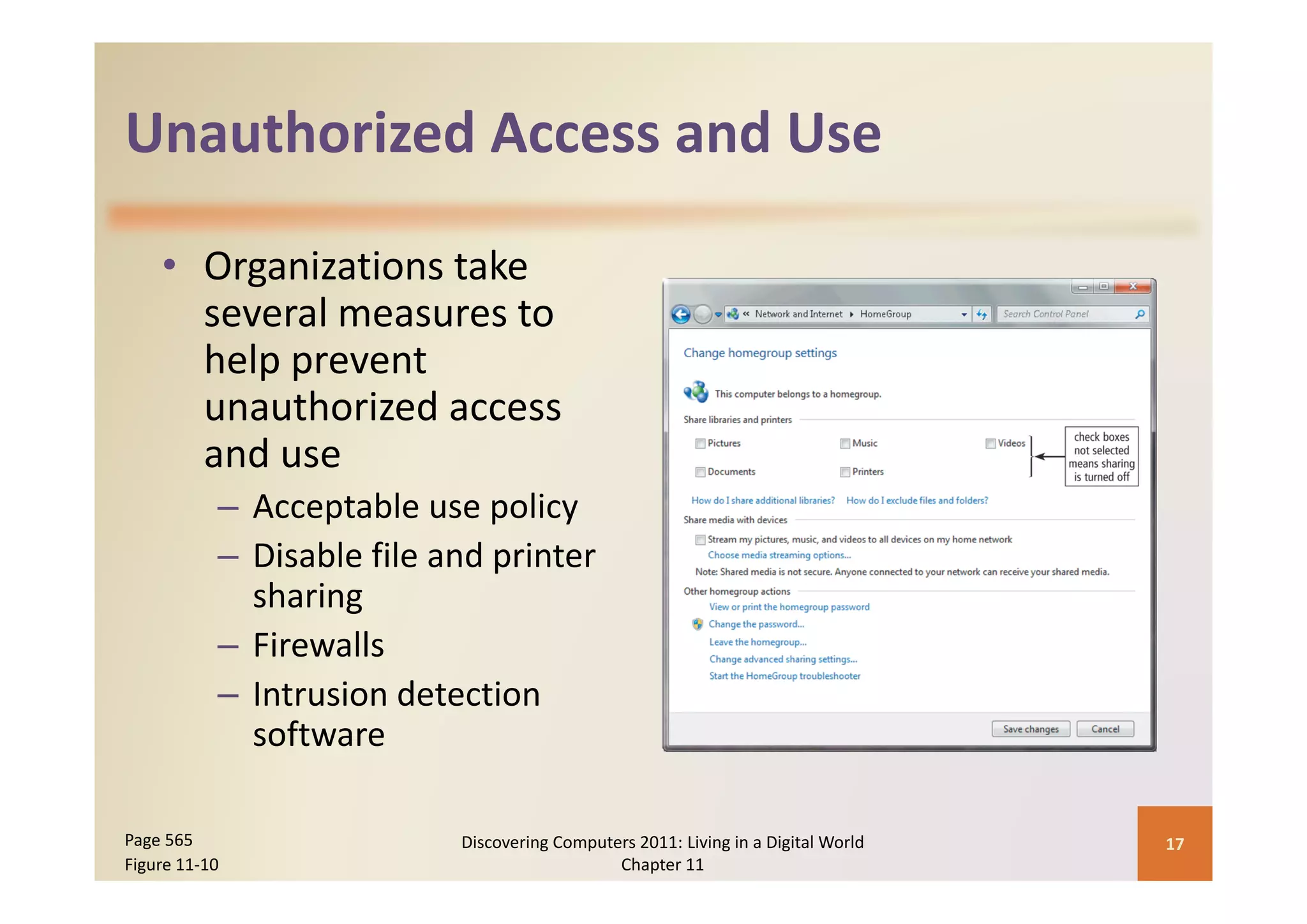
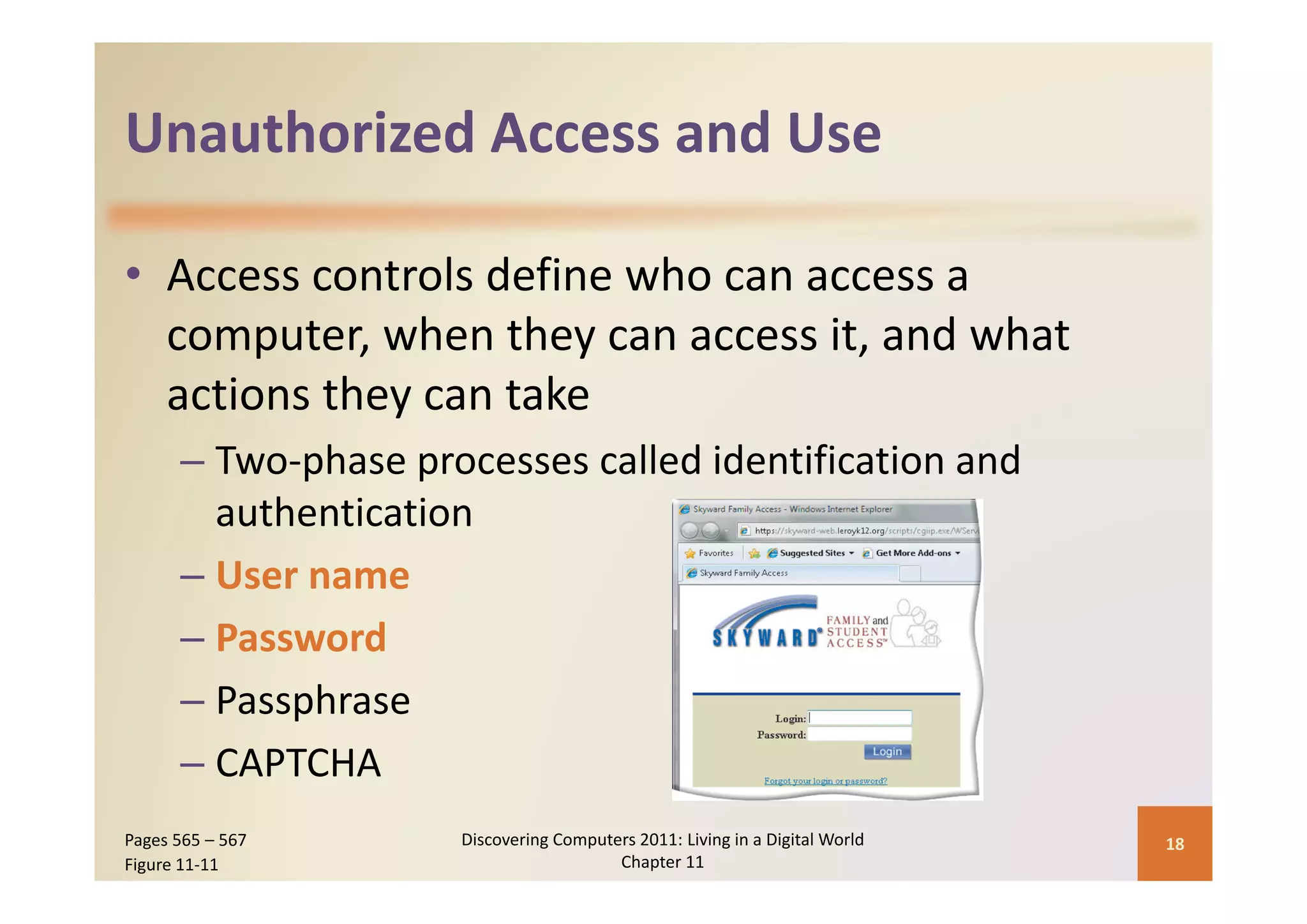
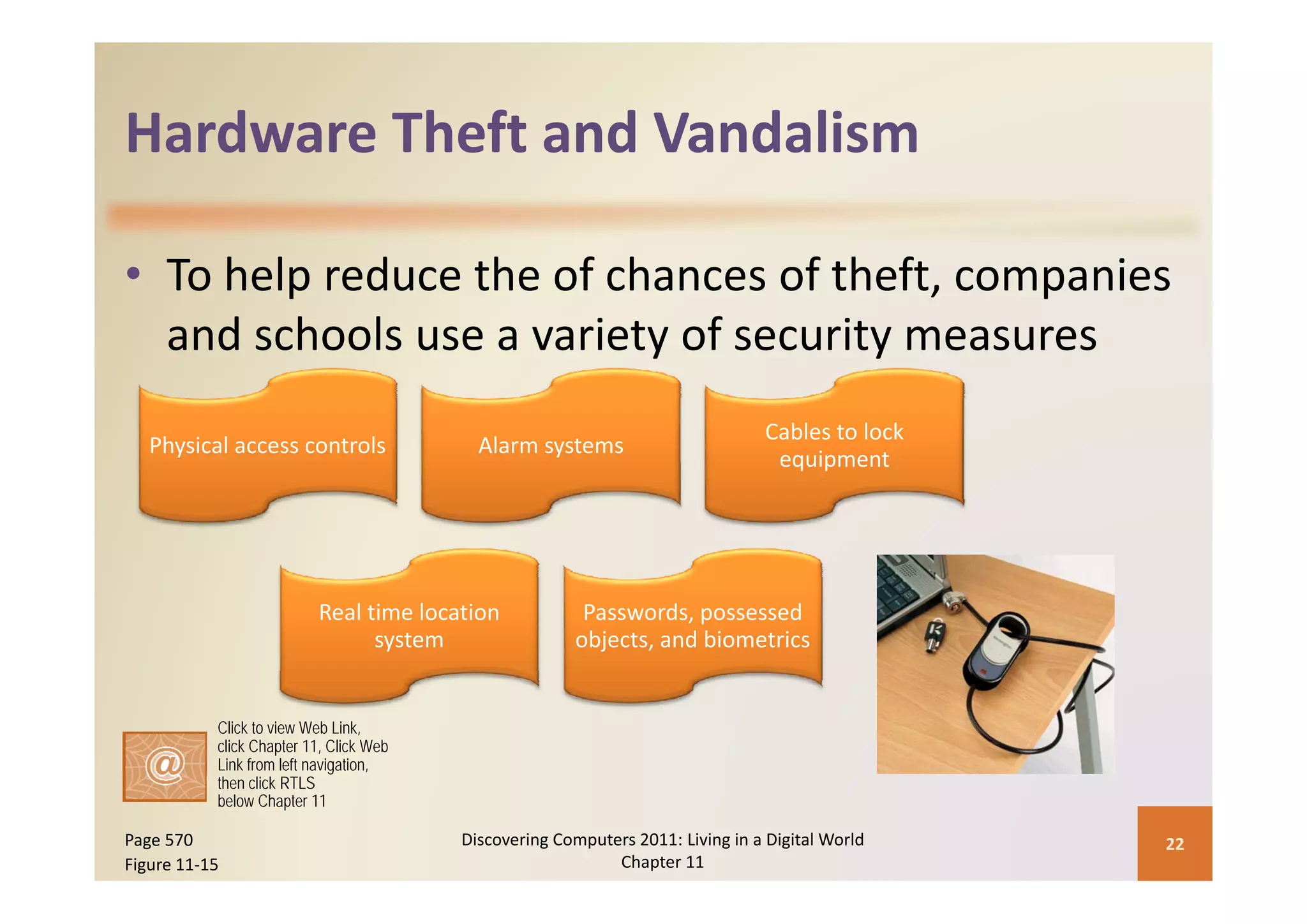
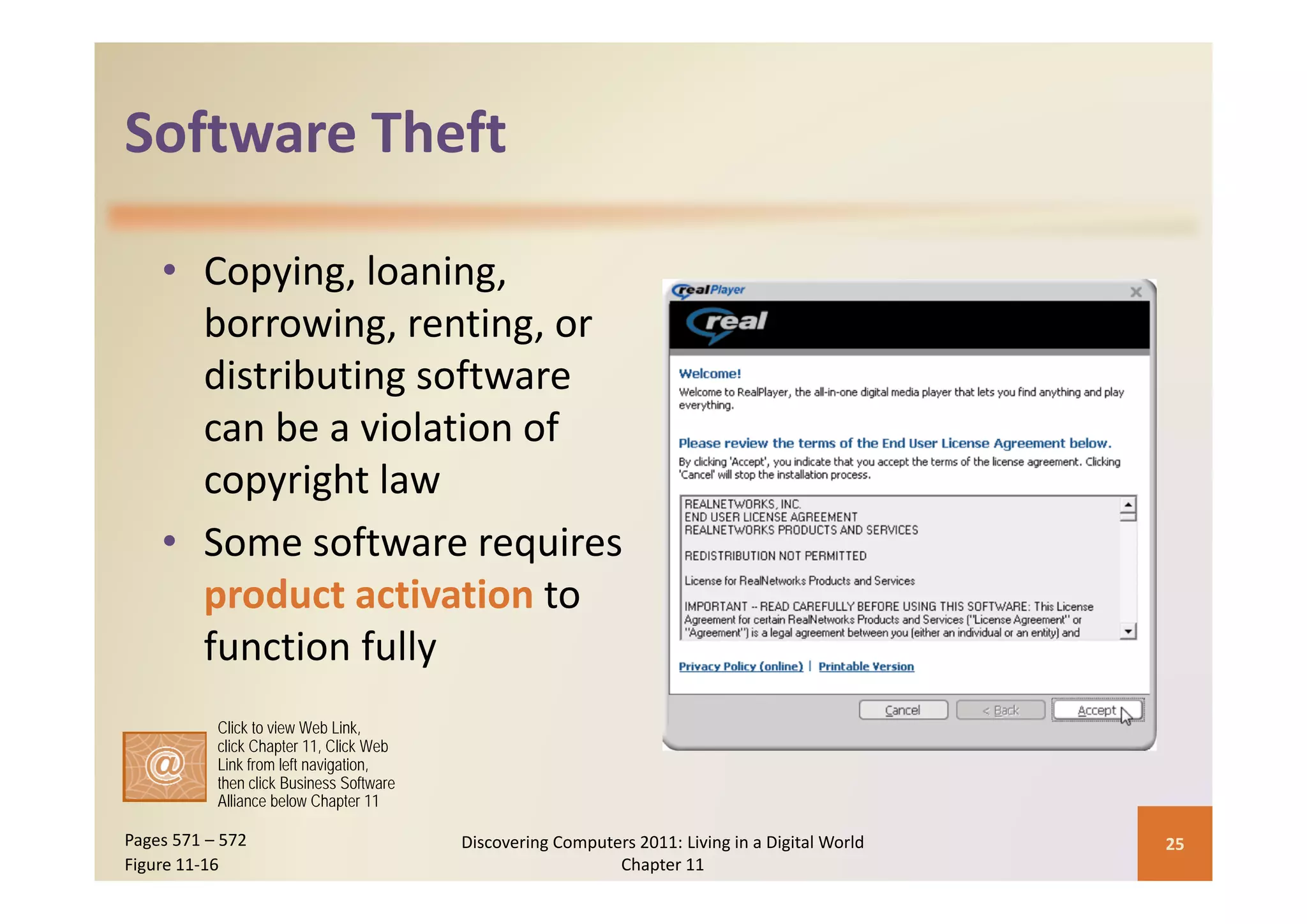
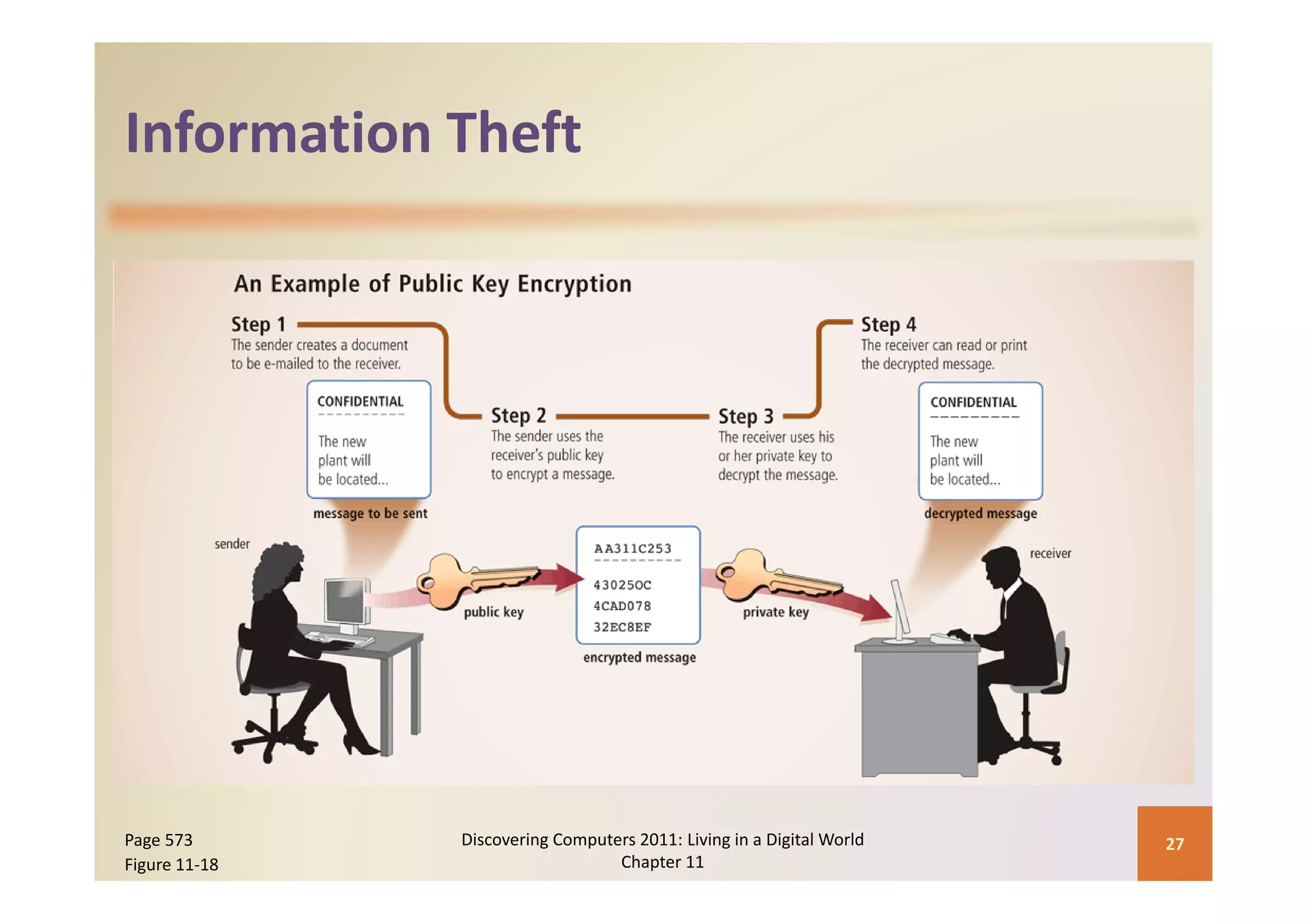
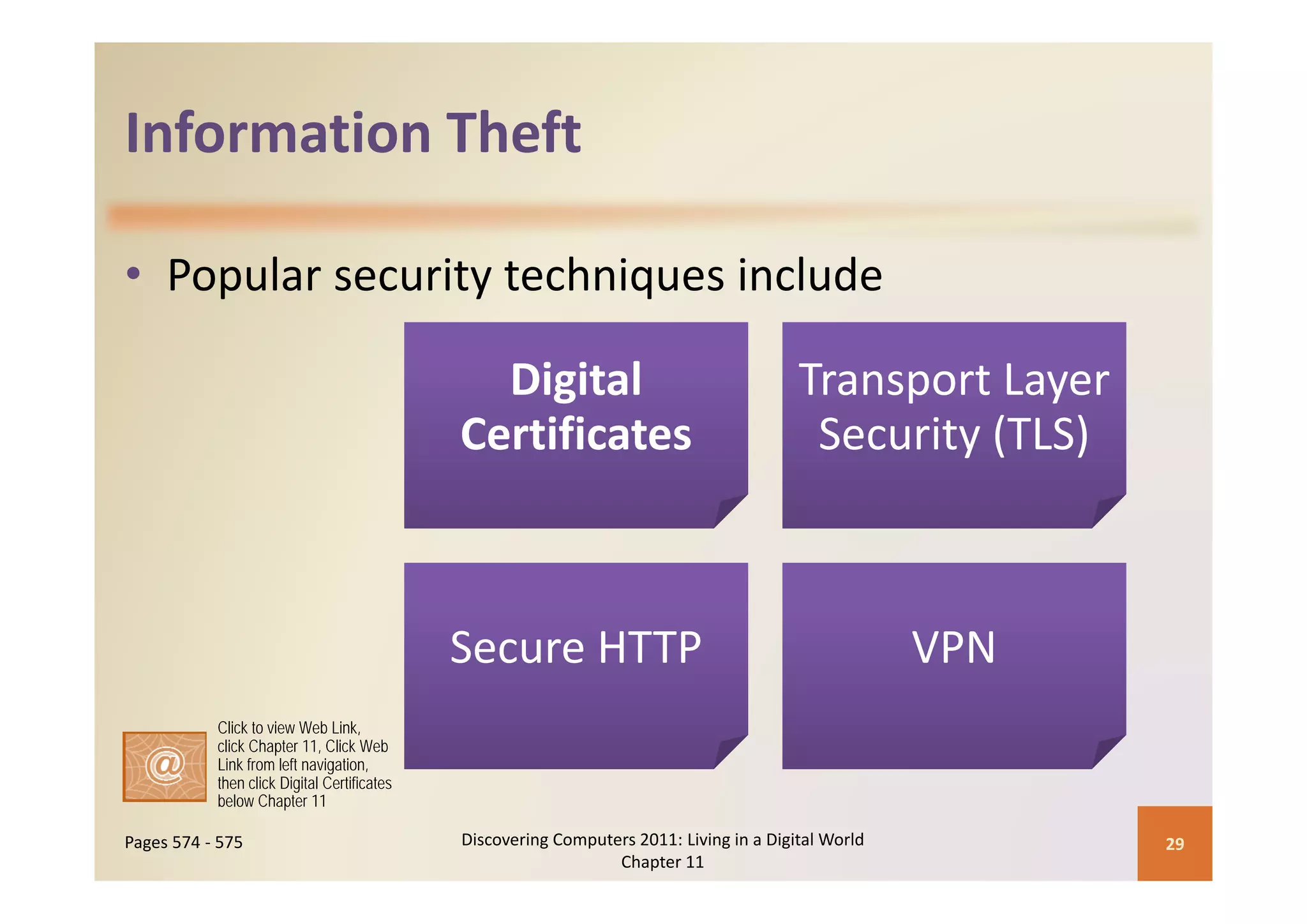
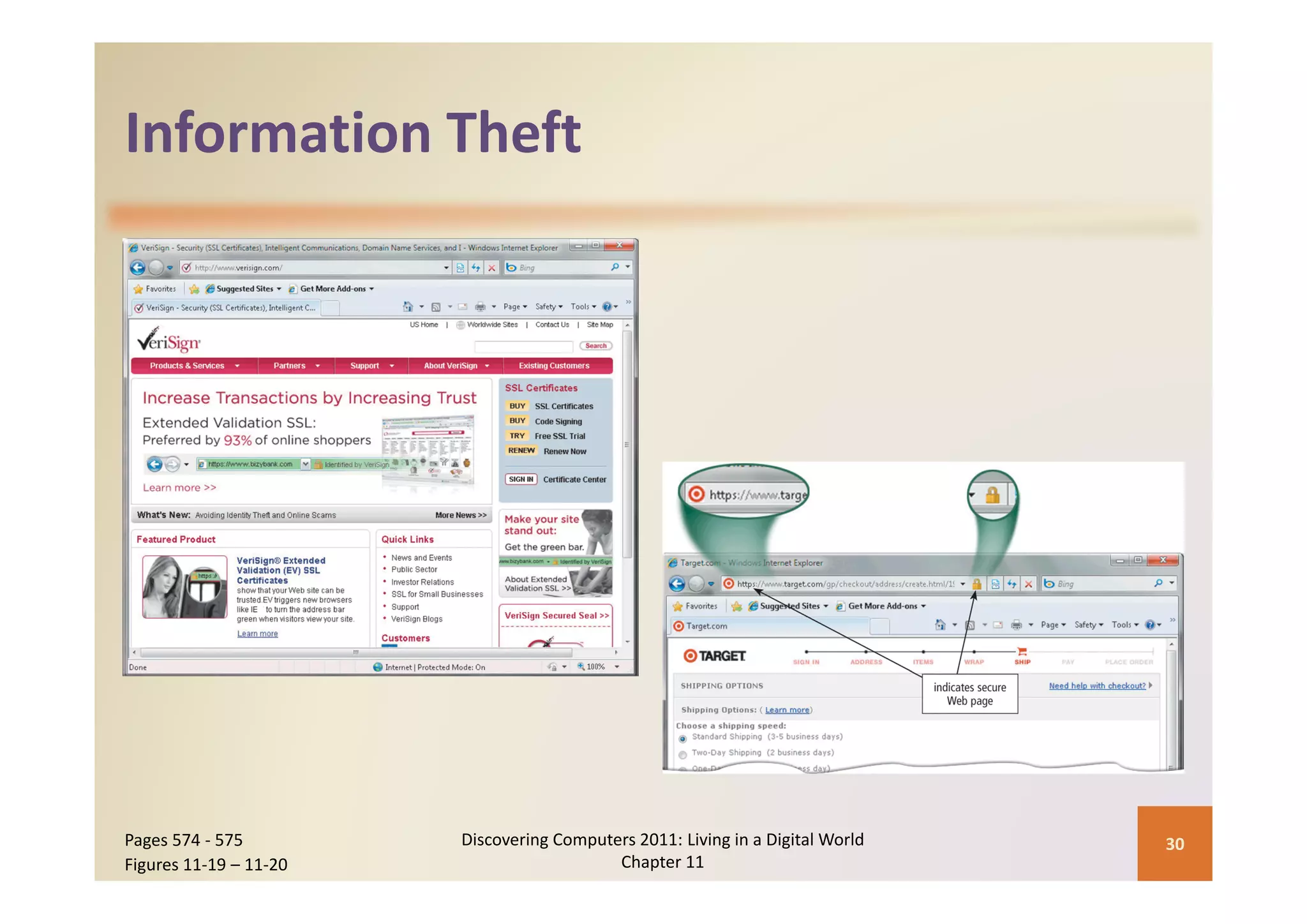
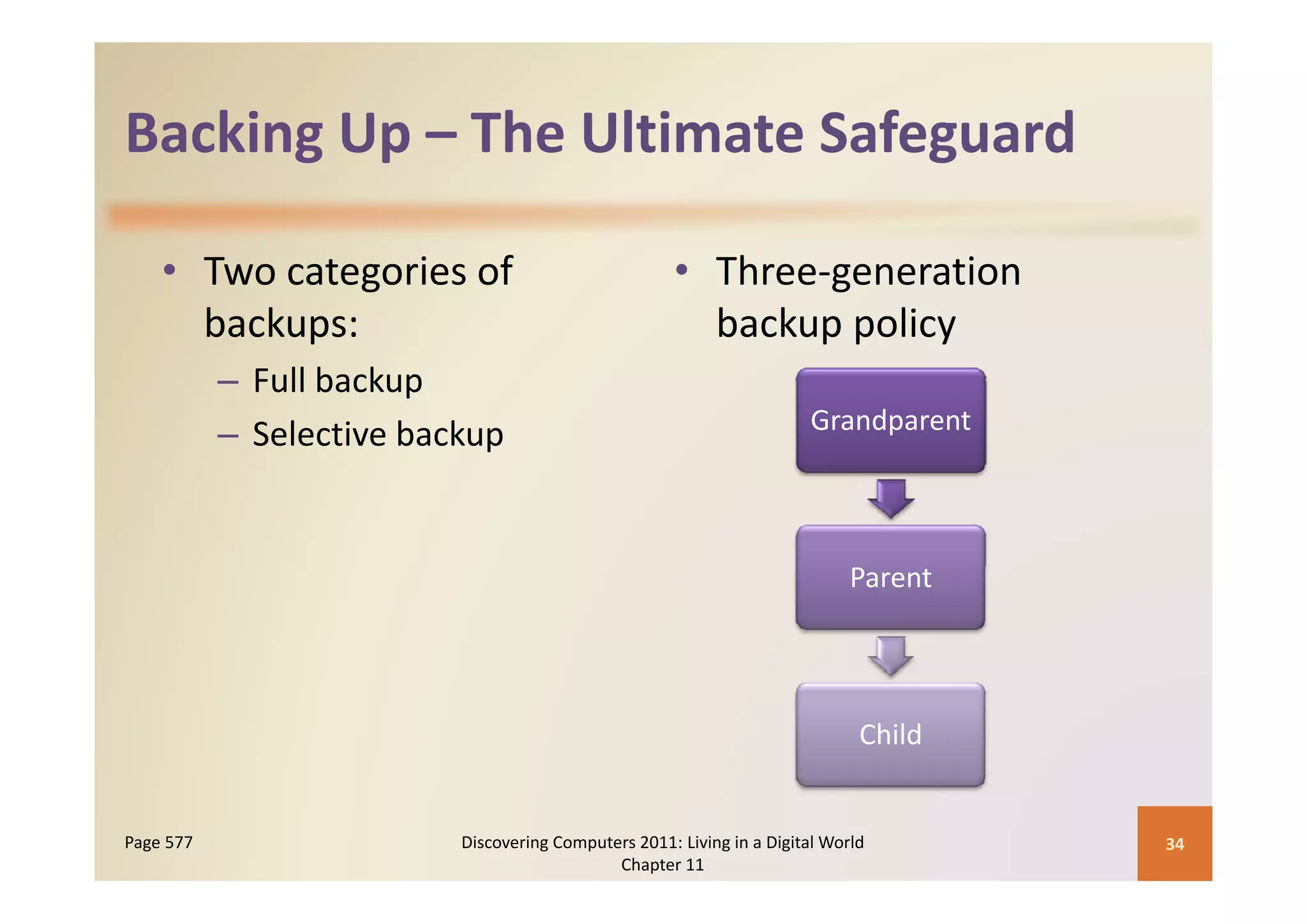
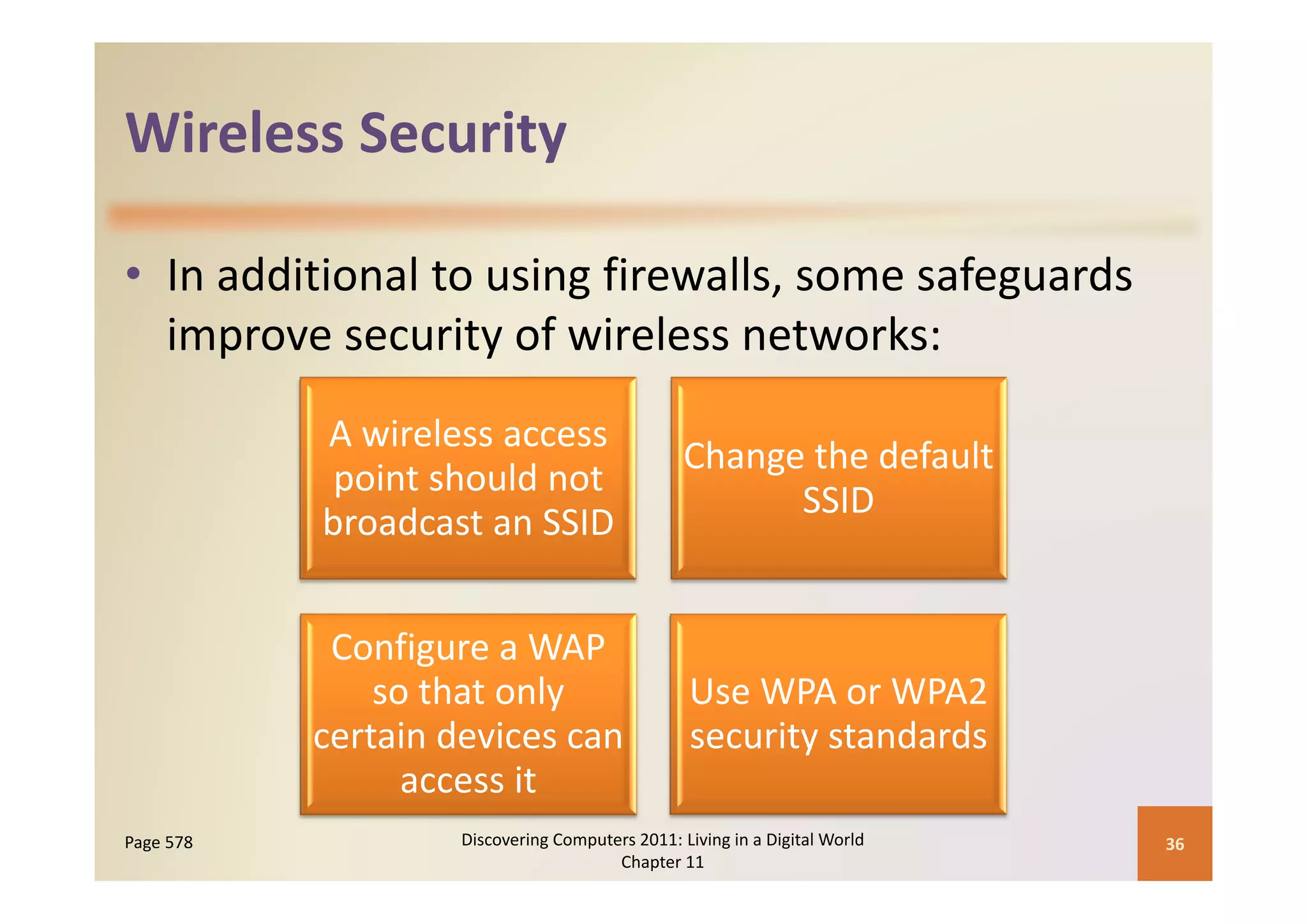
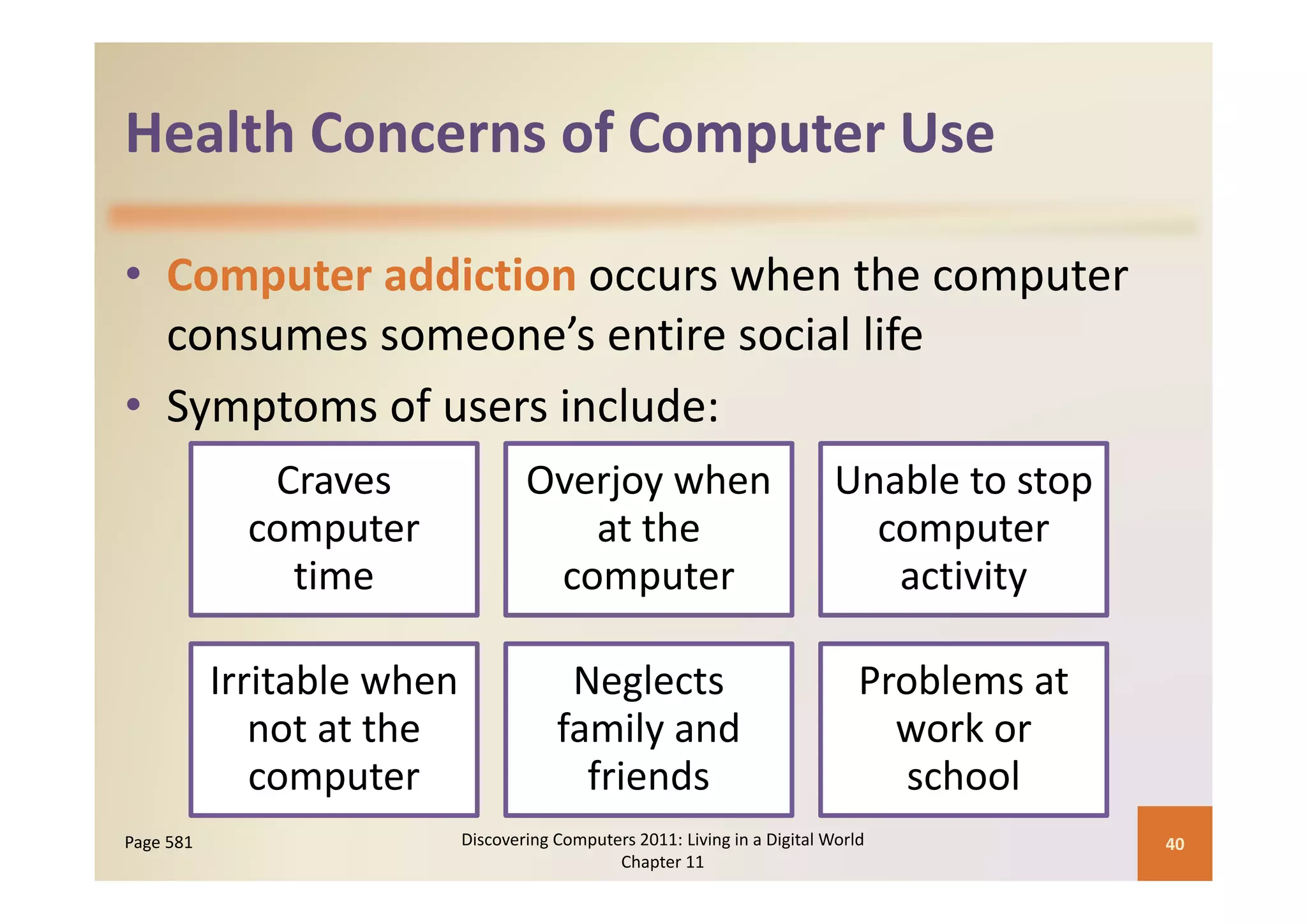
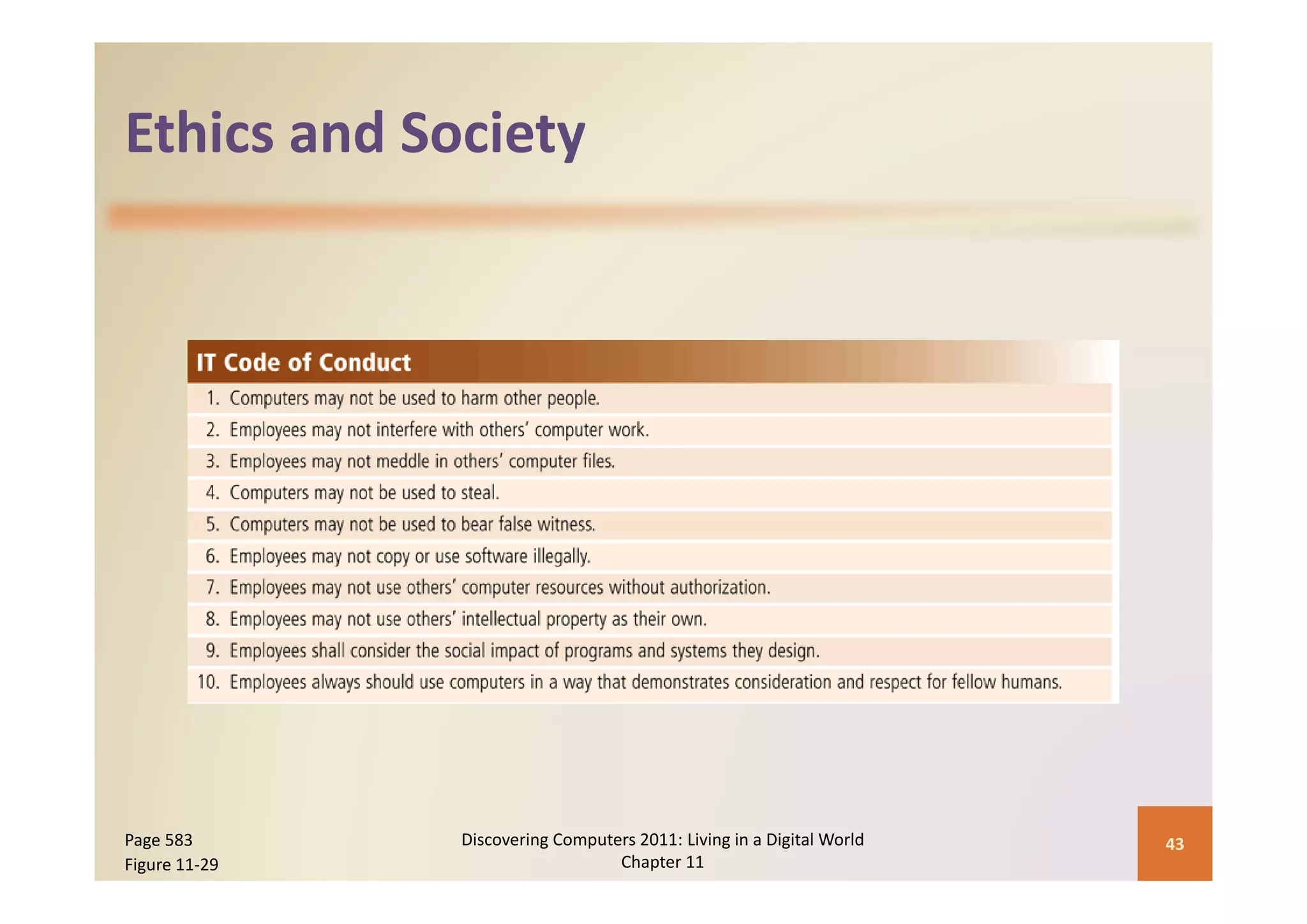
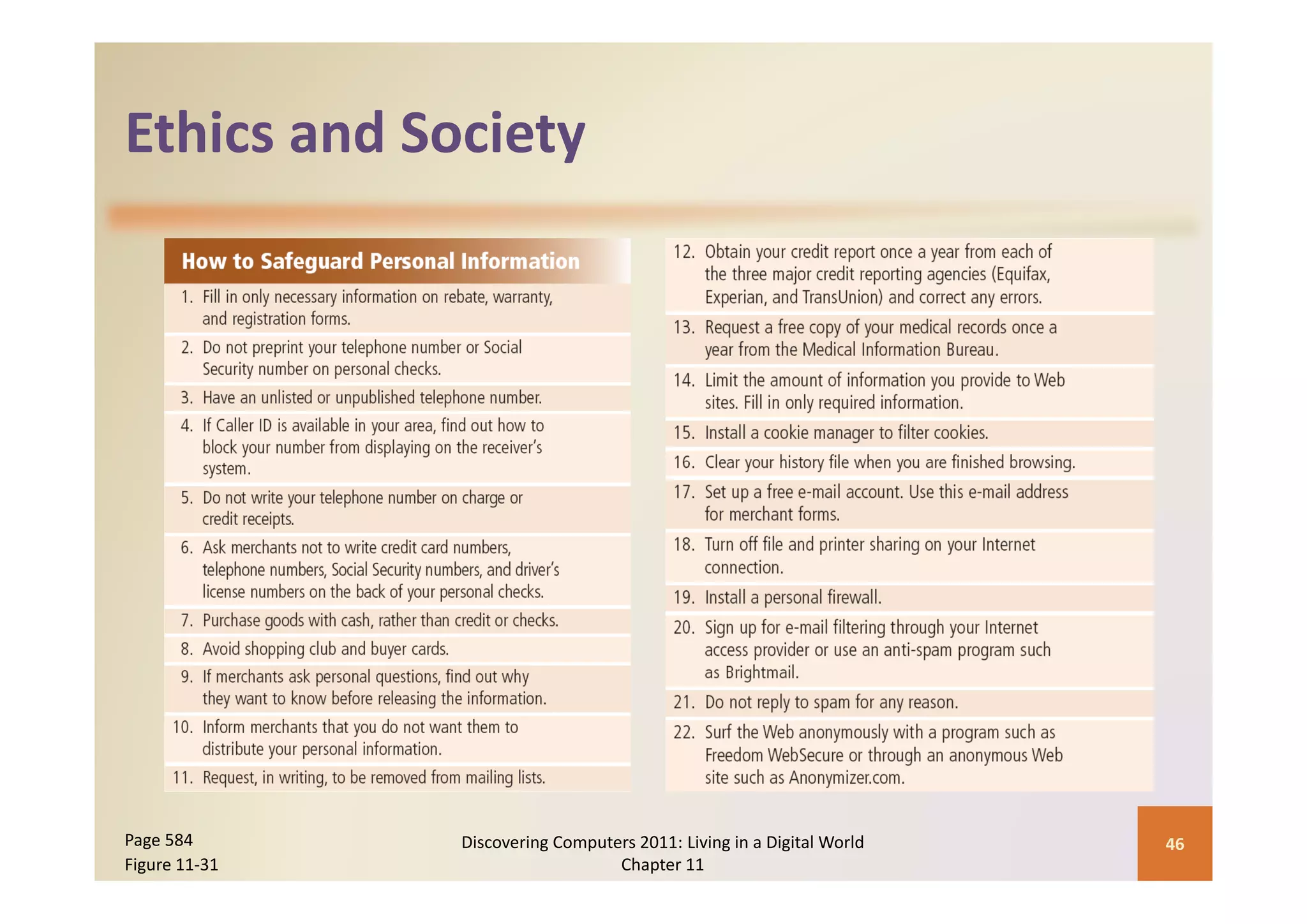
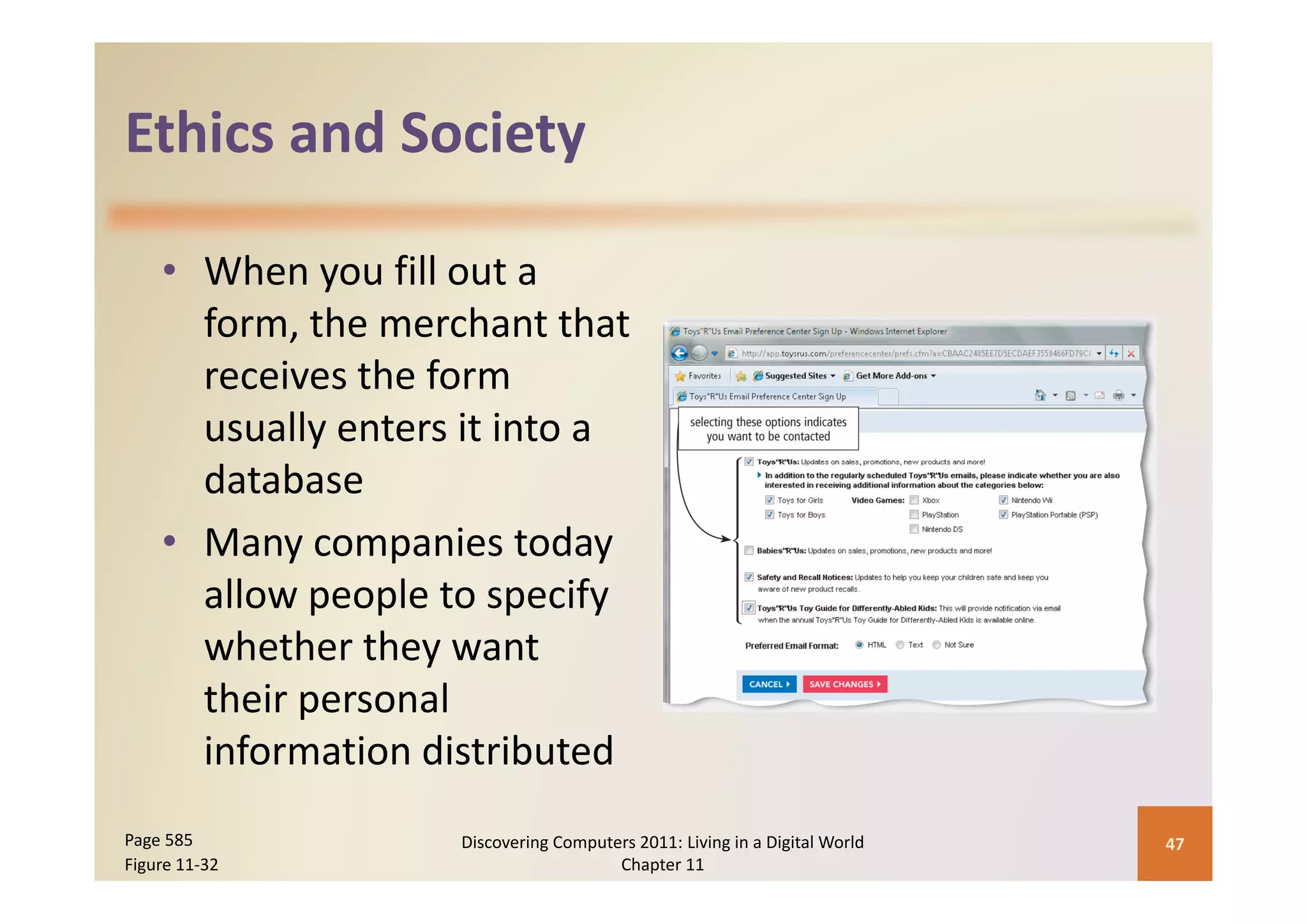
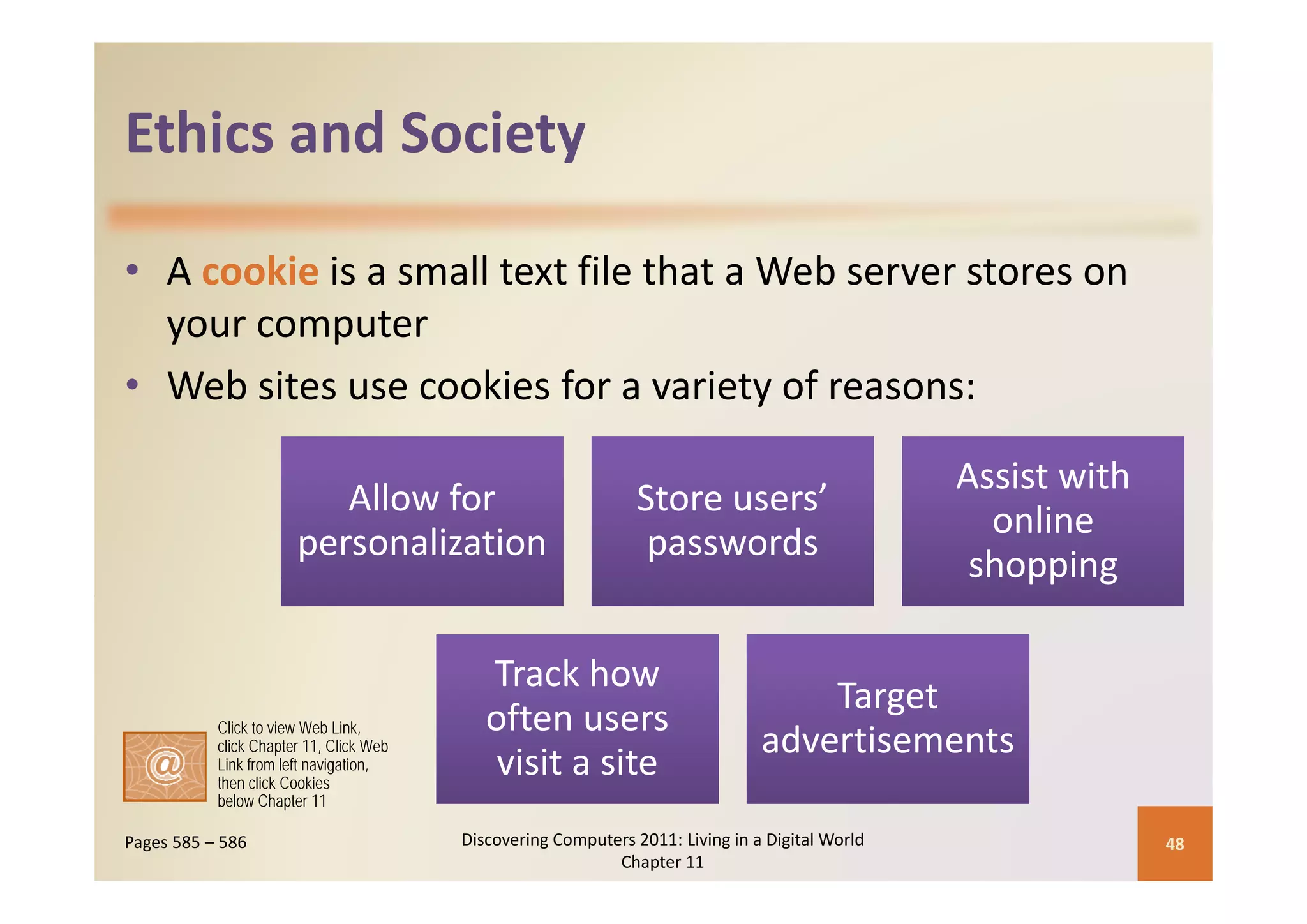
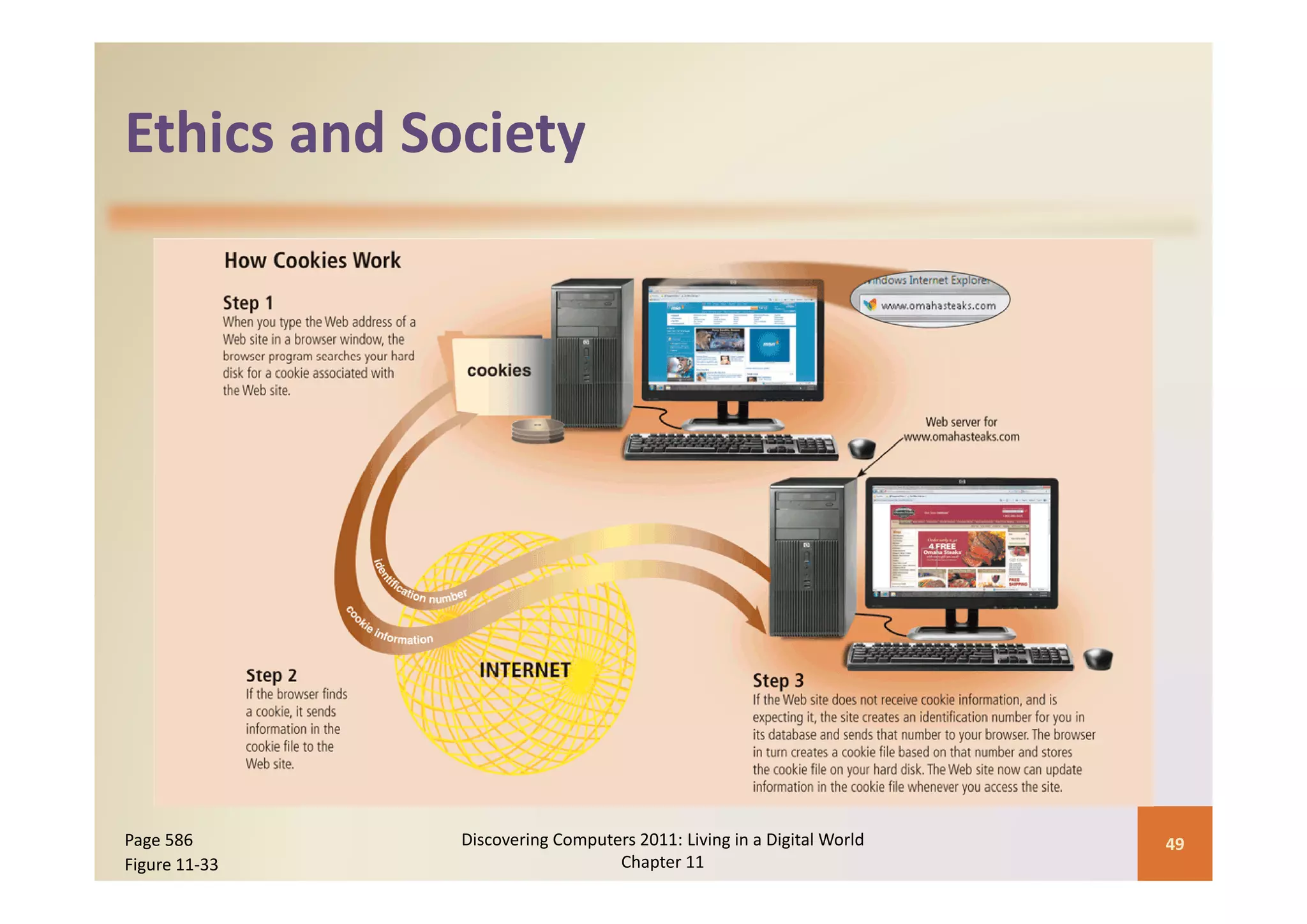
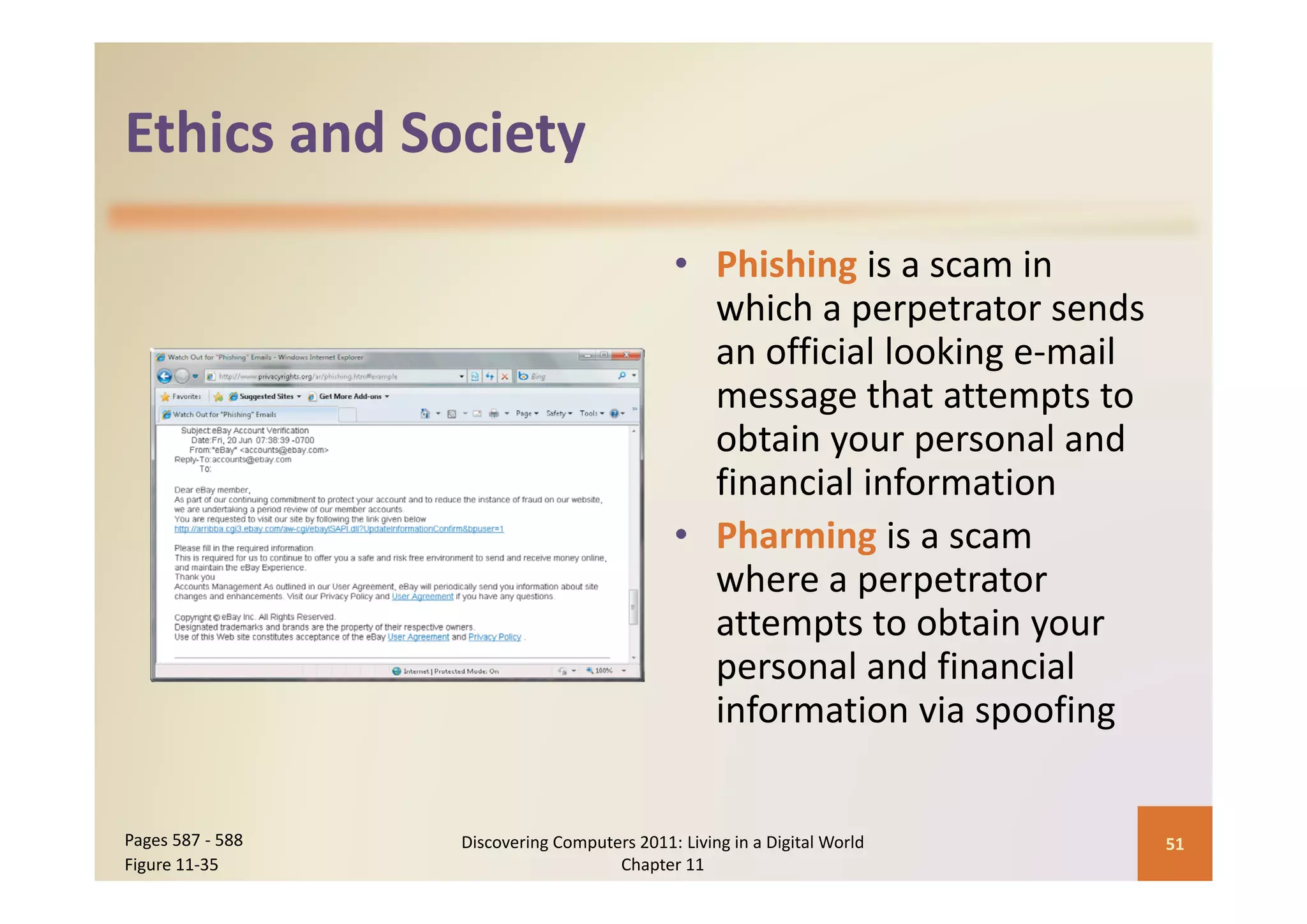
This document discusses computer security risks and techniques to protect against unauthorized access and use. It defines computer security risks and describes various types of cybercrime perpetrators. Various types of Internet and network attacks like viruses, worms, Trojan horses, and rootkits are explained. Symptoms of an infected computer and safeguards against hardware theft, vandalism, and malicious infections are presented. Users can take precautions like using antivirus software, firewalls, and strong passwords to safeguard against attacks.