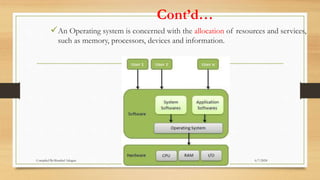
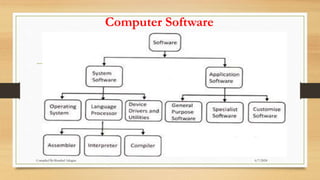
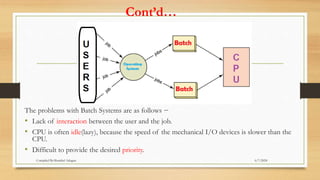
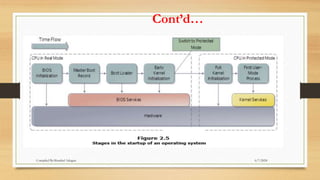
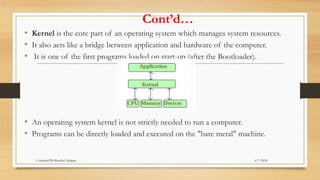
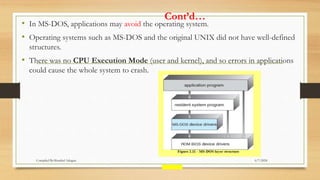
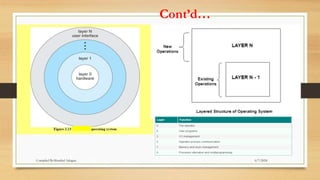
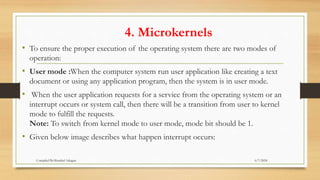
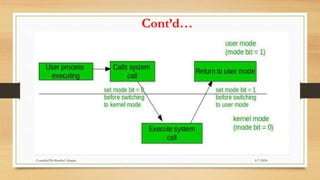
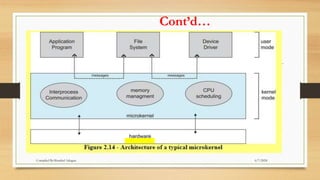
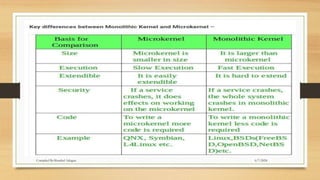
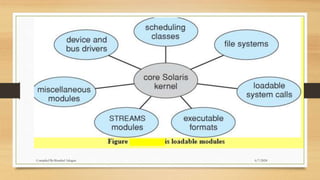
The document provides a comprehensive introduction to operating systems, detailing their overview, functionality, types, and history. It explains the essential roles of operating systems in managing hardware, memory, processes, and devices, alongside discussing different software categories. Additionally, it covers various types of operating systems, including batch, time-sharing, distributed, network, and real-time systems, as well as their respective advantages and disadvantages.