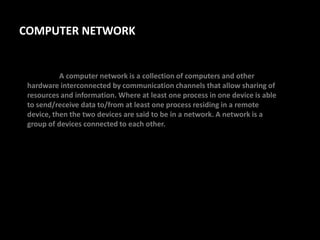
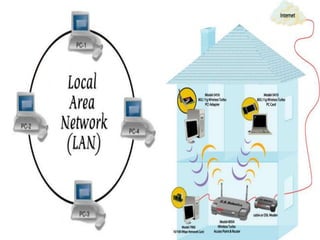
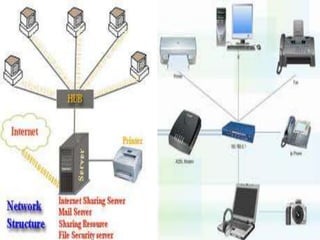
A computer network connects multiple devices through communication channels to allow sharing of resources and information. It consists of a collection of interconnected computers and other hardware. Communication protocols define the rules for exchanging data between devices on the network. Common protocols include Ethernet for local area networks and the Internet protocol suite for internetworking between multiple networks.