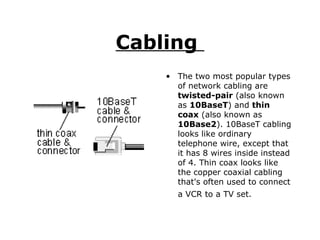
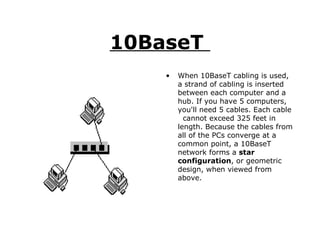
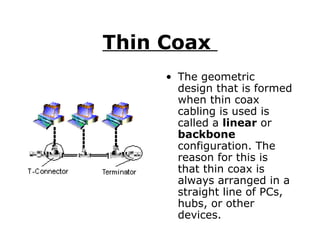
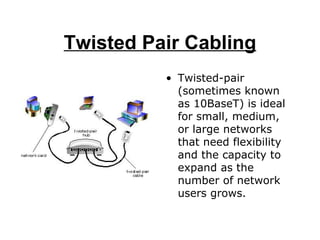
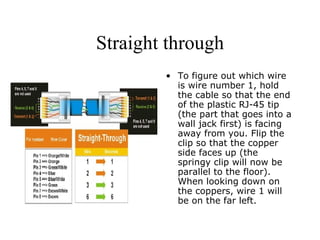
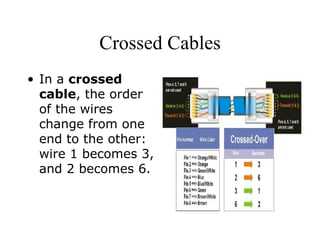
A network connects computers and devices together using cables to allow sharing of hardware, software, files and printers. Information travels over the cables at certain speeds depending on the type of network. There are rules and standards that networks follow regarding cabling, topology and speeds. Ethernet is a common and fast networking standard that uses either twisted-pair or thin coax cabling and network cards to connect nodes on the network.