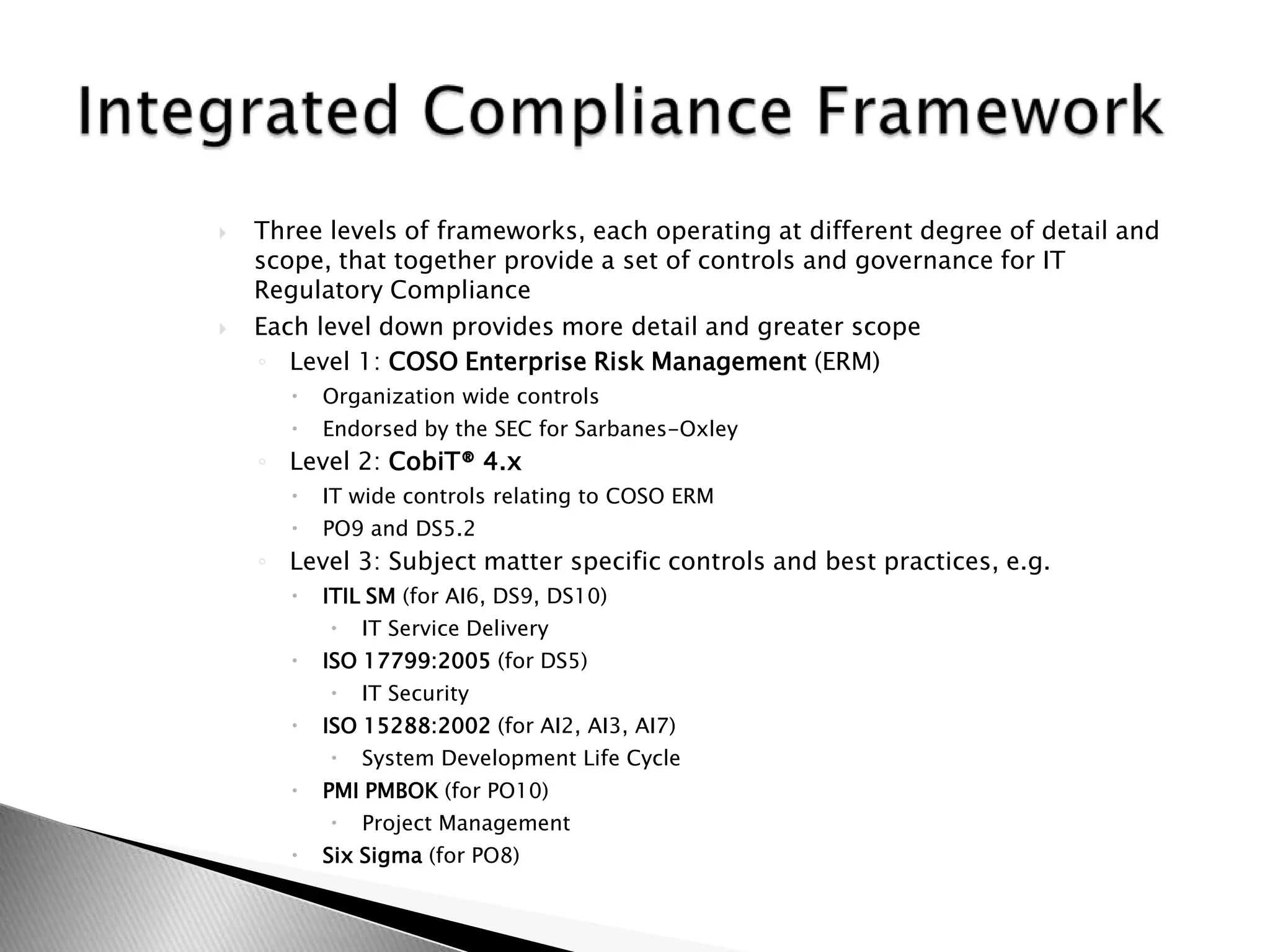
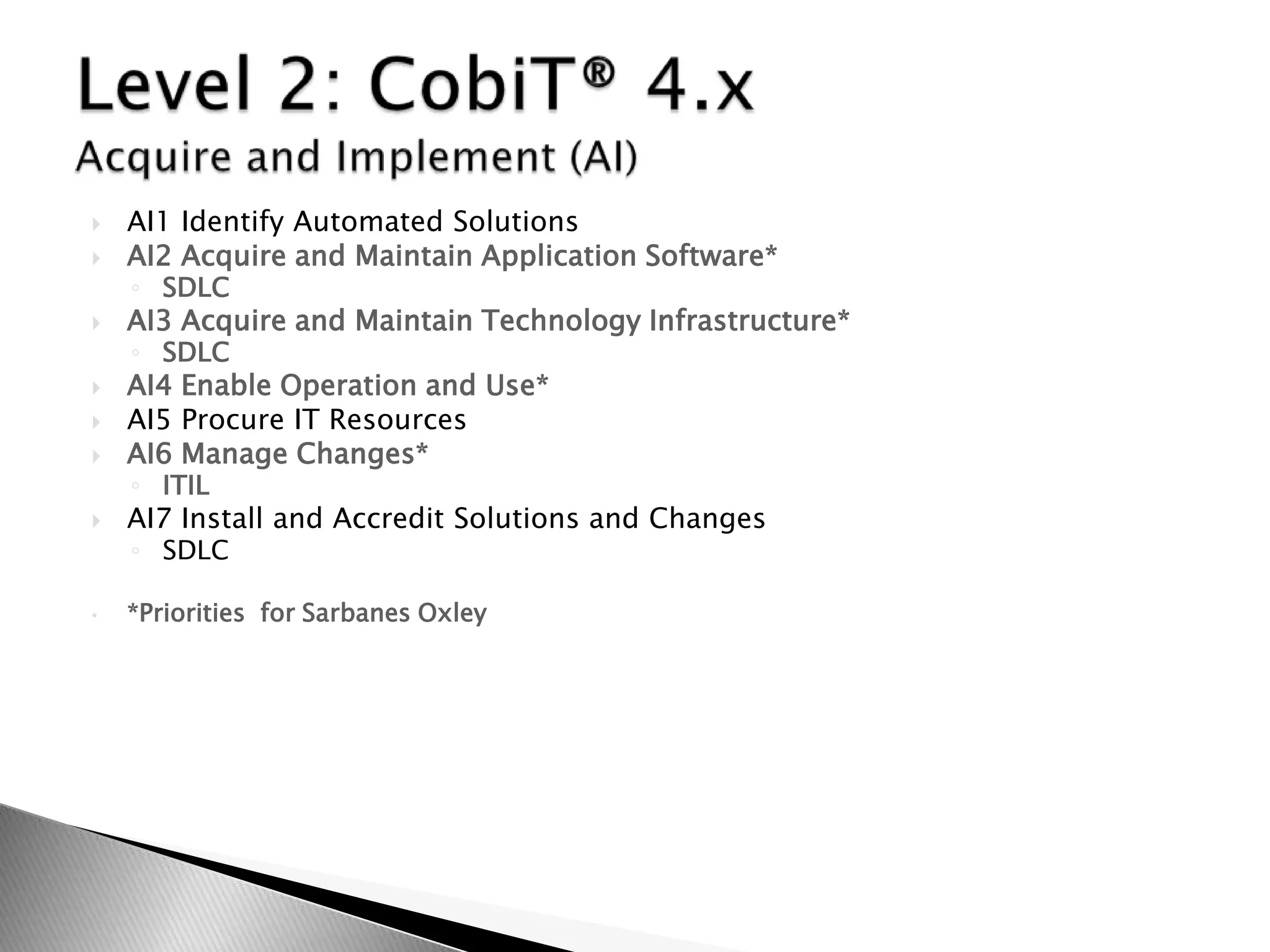
The integrated compliance framework consists of three levels that together provide controls and governance for IT regulatory compliance. Level 1 is the COSO Enterprise Risk Management framework. Level 2 is the CobiT framework, which provides IT controls related to COSO. Level 3 includes standards specific to subject matters, such as ISO 17799, ITIL, PMBOK, and systems development lifecycles, that address controls in CobiT. Adopting this multi-level framework using industry standards and best practices takes a risk-based approach to compliance.